Three serious vulnerabilities in cross-app resource sharing protocols on Apple's desktop and mobile platforms have been discovered and used successfully to steal data — Â like passwords and secret authentication keys — Â including one that lays Keychain open to attackers.
Discovered by a team of six researchers at Indiana University, Georgia Tech, and China's Peking University, the exploits rely on fundamental flaws in the implementation of Keychain's access control lists, OS X's app containers, and URL schemes that allow apps to call out to each other. Apple was notified of these vulnerabilities last October, the researchers told The Register, and then requested a six-month extension before the paper was made public, which was granted.
The vulnerability in Keychain stems from its inability to verify whether apps should be entitled to modify entries. Using the newly-discovered exploit, a malicious app can delete existing entries — Â or create them before the legitimate app has a chance to — Â and give both itself and the legitimate app access, reading the contents of the entry after the legitimate app has written to it.
A proof-of-concept video shows the team removing the Keychain entry for a local user's iCloud account, then creating a new one using a malicious app. After signing in to iCloud through System Preferences, the malicious app successfully retrieves the secret iCloud token stored in that entry. The same attack was used to retrieve passwords stored in Keychain by Google's Chrome browser, which will reportedly remove Keychain access until a fix is issued.
Another vulnerability exists in OS X's app containers, which are designed to keep Mac App Store apps from accessing data belonging to other apps without explicit permission to do so. Apple enforces this access control in part by giving each app a Bundle ID, the uniqueness of which is ensured by the Mac App Store.
The Mac App Store does not verify the uniqueness of Bundle IDs belonging to helper apps, however — Â one example of a helper app is 1Password Mini, which is a separate app from 1Password but included in the same download. By creating a malicious helper app with the same Bundle ID as an existing app, malicious apps can gain access to the legitimate app's containers.
An additional flaw in URL Schemes allowed the researchers to hijack the URL schemes of other, legitimate apps and exfiltrate any data passed between them. In one example, their malicious app registered the fbauth:// scheme that iOS apps use for Facebook sign-in and was able to intercept the user's Facebook authentication token.
The flaws remain unfixed in the latest pre-release versions of OS X Yosemite, though they have not yet been tested against OS X El Capitan, which was announced last week. The team was also successful in getting proof of concept apps into the Mac and iOS App Stores, where the malware was not detected during the approval process.
It remains unclear how Apple plans to mitigate these threats going forward, as it would require significant architectural alterations to the way OS X and iOS interact with apps.
In the meantime, users are advised to follow standard security precautions: Do not install apps from unknown sources, and be cognizant of any suspicious password prompts.
 AppleInsider Staff
AppleInsider Staff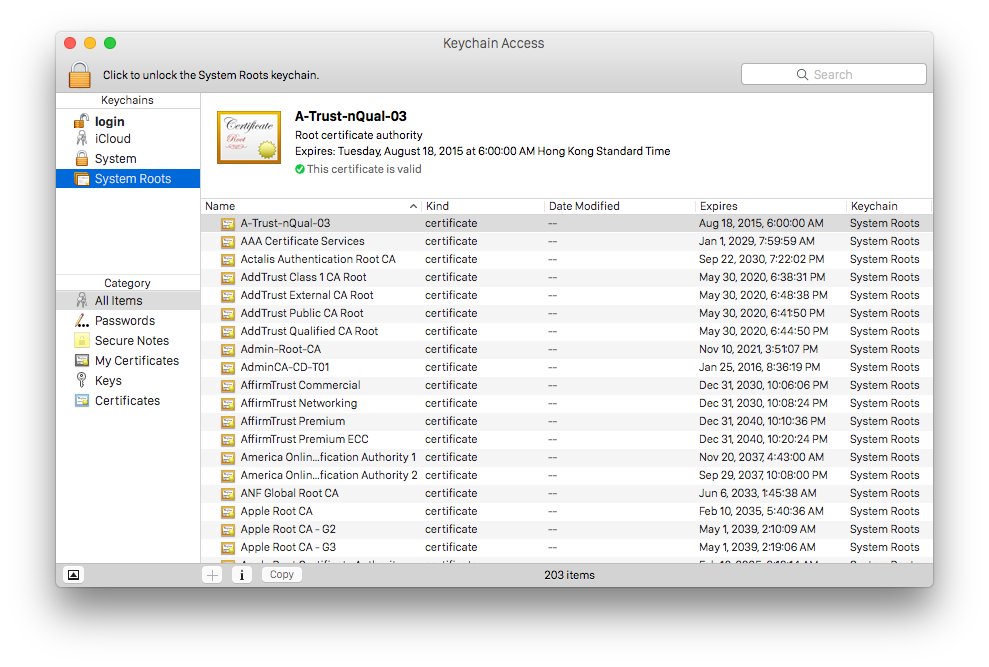






-m.jpg)





 Charles Martin
Charles Martin
 Andrew O'Hara
Andrew O'Hara
 Wesley Hilliard
Wesley Hilliard
 Marko Zivkovic
Marko Zivkovic

 Malcolm Owen
Malcolm Owen










70 Comments
"Apple was notified of these vulnerabilities last October, the researchers told The Register, and then requested a six-month extension before the paper was made public, which was granted."
Yikes... Just, yikes.
It remains unclear how Apple plans to mitigate these threats going forward, as it would require significant architectural alterations to the way OS X and iOS interact with apps.
I presume this is why they asked for a six month extension on the release of information on the exploits. Hopefully they've incorporated the fixes for this into El Capitan. Somewhat disappointing to hear it's not resolved in the latest pre-release of Yosemite. Hopefully they'll fix it at least by the last point release for Yosemite (and possibly even patch earlier OS X releases).
Can the writer of the click bait headline explain exactly whose passwords were stolen?
So Apple has known about this since last Oct. but has not addressed it in any updates? Cook is going around making grandious speeches about security, but not staying on top of things in his own backyard. Sounds just like a politician.
Epic fail, wow!