The first software patch designed to mitigate the high-profile Stagefright vulnerability in Google's Android mobile operating system was insufficient, one security researcher discovered, leading to the issuance of yet another update.
Last week, security expert Jordan Gruskovnjak found that one version of the Stagefright patch — Â which allows a malformed MP4 file to cause an integer overflow — Â did not fully address the problem, and was able to bypass the fix with a new proof of concept. Google was notified on August 7, and has already begun distributing another update.
"We've already sent the fix to our partners to protect users, and Nexus 4/5/6/7/9/10 and Nexus Player will get the OTA update in the September monthly security update," a Google spokesperson told Threatpost.
Wireless carriers in the U.S. have also chipped in, working to block transmission of MMS messages that contain exploitable payloads.
First revealed publicly in late July, the Stagefright exploit relies on a bug in Android's media handling library. It allows attackers to craft a malicious MMS message that would execute arbitrary code whenever received by or opened on an Android device.
"Attackers only need your mobile number, using which they can remotely execute code via a specially crafted media file delivered via MMS," the flaw's discoverers explained at the time. "A fully weaponized successful attack could even delete the message before you see it. You will only see the notification."
Last week, Google announced plans to begin issuing regular monthly security updates for Nexus users. LG and Samsung have signed on to distribute those patches to their devices as well.
 AppleInsider Staff
AppleInsider Staff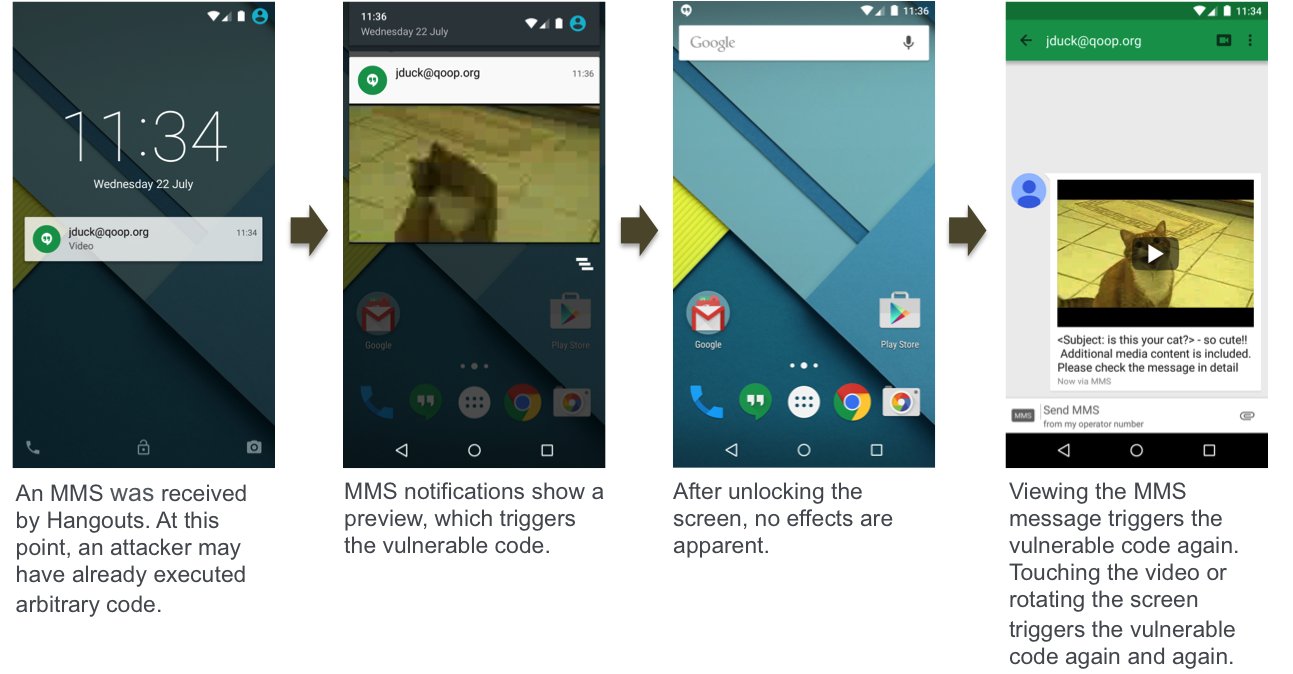







 Malcolm Owen
Malcolm Owen
 Amber Neely
Amber Neely


 Christine McKee
Christine McKee

 Chip Loder
Chip Loder
 Marko Zivkovic
Marko Zivkovic









39 Comments
2.6% of Android users have the latest version? Let's double that number by 2017! Reach for the sky, Google! Or maybe not. I know Samsung loves my friends who buy a new Android phone every year or so, to escape the problems of the previous one and get the latest Android features they love to brag about (despite never actually getting on their current phone). Android hardware tends to be abandoned by the manufacturer before it's even paid off.
Google likes to throw around big numbers when bragging about Android activations, but maybe in this instance, it might want to pretend all those once activated Android devices out there received as a $99 gift but are now sitting at the bottom of a junk drawer don't exist. But they do.
Patches? We don't need no stinking patches.
Let's see how the fanDroids spin this one. This is really gonna push their creativity. [quote name="sog35" url="/t/187722/googles-initial-android-stagefright-patch-inadequate-forced-to-issue-second-fix#post_2761050"]LOL. Android is such a clustersmuck. IMO, Google should just phase out Android. They basically make zero $ off of it. "Google would be better off if there were more iPhones since thats where are their mobile profits come from. this week, Goldman's analysts estimated that Google did $11.8 billion in mobile search revenue in 2014.
Goldman estimated that 75% of that revenue, $8.9 billion, came from Web searches made using iPhones and iPads.
That means that, at most, Google generated $3 billion from searches made on Android devices in 2014."
[URL=http://www.businessinsider.com/goldman-sachs-says-android-is-making-google-very-little-money-2015-4]http://www.businessinsider.com/goldman-sachs-says-android-is-making-google-very-little-money-2015-4[/URL] So Google only makes $3 billion in revenue from Android. They already lost $12 billion in the Motorolla purchase and no doubt pay a ton of salaries to keep Android running. Bottom line they don't make any money on Android. [/quote] The irony here is, if Giggle wouldn't have betrayed Apple they would have been making a ton more money with no work. I hope Apple cuts iOS revenue stream for them soon.
[quote name="jsmythe00" url="/t/187722/googles-initial-android-stagefright-patch-inadequate-forced-to-issue-second-fix#post_2761057"]Proof of concept? So how likely is this exploit bound to make it into the wild. Apple has had proof of concept security holes(fake a finger print to bypass touchid) but that didn't garner this much news. If it's a real issue then flame android, BUT, if it's a extremely unlikely to happen condition, then let them fix it and move along[/quote] Let the spinning begin!!