More details have emerged about the need for the iOS 9.3.5 patch, which looks to have terminated a trio of exploits capable of a remote jailbreak and mass exfiltration of data from a target's iPhone, including device and account passwords.
A chain of events that started with a targeted attack on an activist's phone has led to the discovery of the assault package, delivered through a link embedded in a SMS message. According to Motherboard, unwary recipients who clicked on the link would be subject to a silent, three-pronged attack that would result in every contact in all of the target's communication data pilfered by the attackers.
The company blamed for the spyware and iOS malware delivery vector appears to be Israeli company NSO. The package, named "Pegasus" was solely crafted to infect an iPhone and exfiltrate all of the target's communications to a remote monitor.
The target of the attack was suspicious, and forwarded the information to digital rights monitor Citizen Lab, as well as mobile security company Lookout.
"The threats that they are facing today are threats that perhaps ordinary users will face tomorrow."
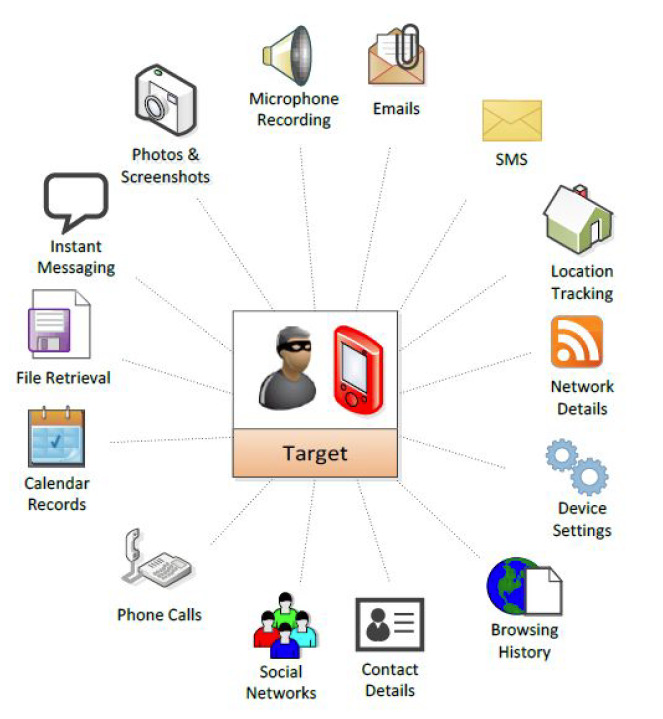
"It basically steals all the information on your phone, it intercepts every call, it intercepts every text message, it steals all the emails, the contacts, the FaceTime calls," said Lookout's Vice President of Research Mike Murray. "It steals all the information in the Gmail app, all the Facebook messages, all the Facebook information, your Facebook contacts, everything from Skype, WhatsApp, Viber, WeChat, Telegram— you name it."
The malware performs multiple tasks remotely with a single click. After the target clicks on the link with the "Pegasus" package, the iPhone is jailbroken, and the monitoring and data theft suites are installed.
Three zero-day vulnerabilities were discovered as a result of the misfired attack. The first is a vulnerability in Safari WebKit that allows the attacker to compromise the device if a user clicks on a link.
The WebKit flaw, coupled with an information leak in the Kernel problem, and an issue where Kernel memory corruption could lead to a jailbreak allowed for the entire attack method to be implemented against the discoverer, and one additional activist in Mexico.
Lookout claims that the payload delivered by "Pegasus" allows the attackers to access passwords, messages, calls, emails, and logs from apps including Gmail, Facebook, Skype, WhatsApp, Viber, FaceTime, Calendar, Line, Mail.Ru, WeChat, SS, Tango, amongst others.
Besides just stealing stored data, the malware also constantly updates GPS information and sends it to the command and control server, loads the iOS Keychain and dumps all the victim's data, steals credentials from every wi-fi network the user has connected to, grabs stored Apple router passwords, intercepts phone calls in real-time, and intercepts WhatsApp messages and calls unencrypted.
A compromised phone can also be used as a remotely actuated audio and video recorder.
The overall "Pegasus" package is not iOS exclusive, and can exploit flaws in Android and BlackBerry as well. It appears that the attacker must have some knowledge of platform that the targeted user utilizes to aim the attack, and develop a server-side payload delivery and data receptacle suitable to the device.
Based on some indicators in the code, the spyware's iOS variant is capable of infecting users on iOS 7 or above. Successive updates to the devices afflicted by the malware appear to have no effect on existing malware installations.
Citizen Lab and Lookout informed Apple of the vulnerabilities on August 15. Today's iOS 9.3.5 patch blocks the attack. Despite the severity of the attack, Lookout believes the vast majority of users will not be impacted by Pegasus at all given the "sophisticated, targeted nature" of the attack.
"Dissidents, activists — these are kind of the people on the front-lines of what is to come for all of us tomorrow, these guys are sort of the canaries in the coal mine," Citizen Lab researcher Bill Marczak said. "The threats that they are facing today are threats that perhaps ordinary users will face tomorrow."
 Mike Wuerthele
Mike Wuerthele







-m.jpg)






 Charles Martin
Charles Martin
 Christine McKee
Christine McKee
 Wesley Hilliard
Wesley Hilliard
 Malcolm Owen
Malcolm Owen
 Andrew Orr
Andrew Orr
 William Gallagher
William Gallagher
 Sponsored Content
Sponsored Content







36 Comments
I'm reading this is the first time this sort of access has been done on an iPhone, but I recall JailbreakMe from 2011 allowing for a jailbreak by simply going to a webpage. What am I missing.
The JailbreakMe was just a jailbreak, and had to be executed willingly by the user, and wasn't silent.
It didn't take two more steps and compromise all your passwords and data on the phone at the same time.