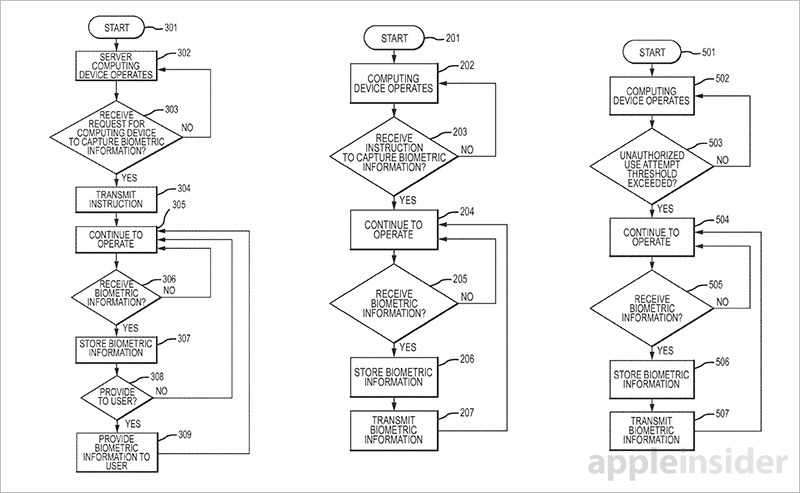
An Apple patent application published on Thursday describes a method of storing an unauthorized user's biometric information, which can help strengthen security management or assist in device recovery and criminal prosecution in the case of a theft.
As published by the U.S. Patent and Trademark Office, Apple's invention covering "Biometric capture for unauthorized user identification" details the simple but brilliant — and legally fuzzy — idea of using an iPhone or iPad's Touch ID module, camera and other sensors to capture and store information about a potential thief.
In practice, the proactive security system works in much the same way as existing Touch ID verification processes.
Currently, users have five attempts to unlock iPhone or iPad with Touch ID before the device defaults to a 6-digit passcode or custom alphanumeric code. Ten failed passcode attempts results in a "cool down" period or a complete data wipe, depending on user settings. Further, passcodes are required after restarting the device, after more than 48 hours has elapsed between unlocks and when an owner wants to manage Touch ID and Passcode device settings.
Apple's patent is also governed by device triggers, though different constraints might be applied to unauthorized user data aggregation. For example, in one embodiment a single failed authentication triggers the immediate capture of fingerprint data and a picture of the user.
In other cases, the device might be configured to evaluate the factors that ultimately trigger biometric capture based on a set of defaults defined by internal security protocols or the user. Interestingly, the patent application mentions machine learning as a potential solution for deciding when to capture biometric data and how to manage it.
Other data can augment the biometric information, for example time stamps, device location, speed, air pressure, audio data and more, all collected and logged as background operations.
The deemed unauthorized user's data is then either stored locally on the device or sent to a remote server for further evaluation. In some embodiments, stored information is purged at regular intervals to save onboard space. Alternatively, purges can also take place when the system determines the data is no longer needed. For example, a device owner's child who is not provisioned to use the device might attempt to access it anyway, leading to multiple invalid attempts over a given period of time.
As for offloading the biometric data, Apple says server-side systems may be able to cross reference fingerprint and photo information with an online database containing information of known users. Additionally, the system can log keystrokes to determine what operations the unauthorized user was attempting to execute while using the device. Given today's litigious climate and emphasis on personal privacy, however, these last two features feel a bit intrusive.
Apple ushered in the era of tenable biometric security technology with Touch ID, a fingerprint sensor that delivers quick, accurate and consistent results. Most importantly, and especially with zippier hardware introduced in iPhone 6s, Touch ID is integrated seamlessly into iPhone's user experience, meaning more people use it.
Touch ID has in some respects cut down on the scourge that is smartphone theft. Thieves doing risk/reward calculations now think twice before stealing an iOS device that might very well turn into a brick.
That being said, today's invention moves away from industry standard countermeasures and into the gray area of proactive digital forensics. As such, it is unlikely that Apple will introduce the technology in a consumer product anytime soon.
Apple's application for collecting biometric information from unauthorized device users was filed for in April and credits Byron B. Han, Craig A. Marciniak and John A. Wright as its inventors.
 Mikey Campbell
Mikey Campbell







-m.jpg)






 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher
 Andrew Orr
Andrew Orr







-m.jpg)




18 Comments
Last year, for reasons I can't explain, I completely forgot my passcode. Something about my brain screwing up the order of the numbers and trying to second-guess my muscle memory caused me to enter the wrong code over 10 times. When I finally remembered the right sequence, I was able to unlock my now-wiped phone. Didn't lose any data, restored everything from backup, invented a new code so I wouldn't fall into that rut ever again, and no it's like nothing ever happened. It was just an accident, the phone never left my person. But with this, TouchID enabled or not, my face and fingerprint would now be on file with law enforcement, even though I no criminal record whatsoever. Just because I caught a bad case of the stupid one night. I hope this is another copyright-and-bury patent that Apple filed explicitly to prevent anyone from doing such an NSA thing.
Just tested it. Passcode is required after three failed Touch ID requests.