Following revelations that a serious bug in macOS High Sierra allows anyone root access to Macs running Apple's latest operating system, the company on Tuesday said it is working on a fix that will be pushed out in a coming software update.
In identical statements to The Loop's Jim Dalrymple and iMore's Rene Ritchie, Apple says it is crafting a patch for a major macOS High Sierra security hole that grants root level access to a logged-in Mac.
"We are working on a software update to address this issue," Apple said. "In the meantime, setting a root password prevents unauthorized access to your Mac. To enable the Root User and set a password, please follow the instructions here: https://support.apple.com/en-us/HT204012. If a Root User is already enabled, to ensure a black [sic] password is not set, please follow the instructions from the 'Change the root password' section."
Discovered earlier today, the flaw allows anyone to log in under a Mac's "root" System Administrator without the need for a password. In practice, the exploit merely requires access to System Preferences, and can be performed in a matter of seconds. Nefarious users can also exploit the bug to bypass a Mac's lock screen.
Beyond those who have direct access to a vulnerable Mac, the security hole also works remotely in certain scenarios where screen sharing, remote access or VNC sessions are enabled. Users should disable those features until Apple's update arrives.
As AppleInsider reported when the vulnerability was first aired today, macOS High Sierra users can prevent unauthorized Mac access by disabling the Root User under System Preferences. Alternatively, and as Apple suggests, users can enable the Root account and set a password.
Apple failed to provide a release timeline, but considering the bug impacts system-level directories and is relatively easy to exploit, a software update should be out soon.
 Mikey Campbell
Mikey Campbell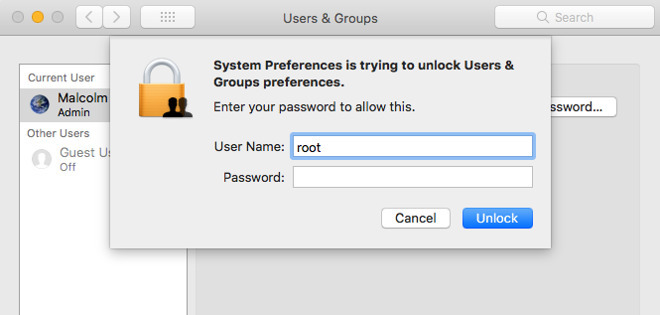








 Charles Martin
Charles Martin

 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher
 Christine McKee
Christine McKee
 Marko Zivkovic
Marko Zivkovic
 Mike Wuerthele
Mike Wuerthele










65 Comments
Well, this is how it should be. Immediate response when there is a really terrible bug.
And the person(s) responsible for this bug should be dealt with appropriately. This is not by accident.
Quick question? Why would you not have set the root password ahead of time? Sure, the fact that the “bug” exposes the account is serious. But, I learned when I first started working with OS X that you set the root password so as to avoid these issues.
Are you telling me that there are millions of OS X machines out there with blank passwords on the root account? That would be like leaving the Administrator account on Windows set to a default or blank password.
I do hope that Apple makes people set a different password on the root account in the future.