The firm says that Java, which can be used to write standalone applications that run across multiple platforms or applets that are embedded in web pages, has a serious flaw that could allow local code on a user's Mac to be executed remotely.
"This can lead to 'drive-by attacks,' where users are attacked simply by visiting a malicious web site and loading a web page," the firm said.
The exploit could allow a third-party to execute code, access or delete files, or run applications on the compromised machine. Combined with other exploits, hackers could even potentially run system-level processes and gain total access over the affected Mac.
Since the vulnerability relies solely on Java, with no native code required, it theoretically exists in all browsers on all platforms that have not been patched. This is the case with Mac OS X 10.5.7 and earlier, meaning the vulnerability affects even the update released just a week ago.
The firm claims that Apple has been aware of the exploit for at least five months, when it was publicly disclosed and fixed by Sun, but has yet to issue a security patch. It was first discovered by Landon Fuller, who has released a proof of concept exemplifying the security hole.
Intego says it has not found any malicious applets in the wild thus far, but the publicity around this vulnerability may entice hackers to target the exploit before Apple issues a security update. The firm's VirusBarrier X5 already blocks potential malware but unless users are sure they trust the site they're viewing, simply disabling Java in the browser may provide the best protection while Apple works on a fix.
To do this, launch Safari, choose Safari > Preferences, click the Security tab, and uncheck Enable Java if it is checked. In Firefox, this setting is found on the Content tab of the program’s preferences. It is safe to leave JavaScript activated, since the vulnerability only affects Java applets.
 Sam Oliver
Sam Oliver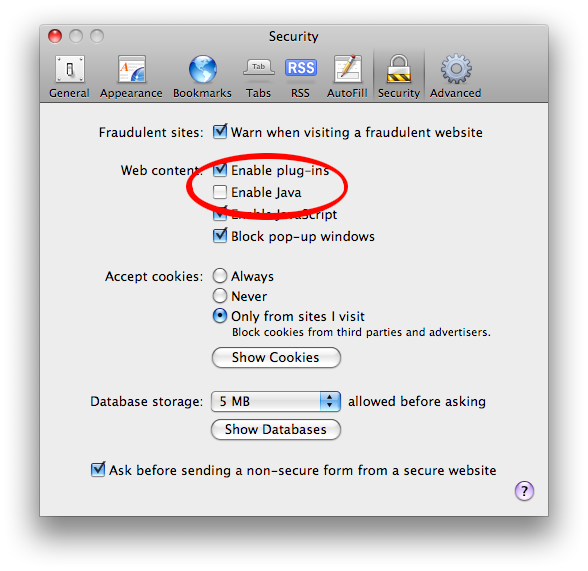







-m.jpg)






 William Gallagher
William Gallagher
 Malcolm Owen
Malcolm Owen


 Charles Martin
Charles Martin
 Wesley Hilliard
Wesley Hilliard









54 Comments
Considering that I have noscript installed in Firefox in addition to having Java disabled browser-wide unless I need it for a specific website, I should be fairly safe for a moment.
Also, "the Apple" sounds much better, as long as you disregard grammar.
Considering that I have noscript installed in Firefox in addition to having Java disabled browser-wide unless I need it for a specific website, I should be fairly safe for a moment.
Also, "the Apple" sounds much better, as long as you disregard grammar.
The issue with Java on the Mac wouldn't surprise me as the Mac version of Java is FAR behind the windows version (no JavaFX support yet, Apple is still on J2SE, version 5.x, when Windows, Linux and Solaris has had Java 6.x for quite a while now). Apple barely updates Java for Mac; they don't seem to be on top of it. They seem to update certain technologies only when they really feel like it.
Case in point:
Java
Apache
SAMBA
mySQL
Wiki server
all have received only security and bug fix updates since Leopard came out. The one real exception is Safari, but Apple has been pretty lax with keeping Safari updated compared to Firefox, Chrome and Opera. It's nice they didn't require 10.5 or Intel macs for Safari however.
etc. Apple only seems to majorally update these components with new OS releases. SAMBA on OSX is signficantly far behind SAMBA for FreeBSD, SOLARIS and Linux releases.
Oh well. Java sucks anyway and has been turned off for quite some time. I suggest everyone never turn java on again!!
I followed that link, then ran the example exploit; sure enough the java applet executes usr/bin/say and your mac talks to you in it's default voice... but from the command line. So it is capable of running commands.
Note that it can't do a sudo rm -f / (which wipes everything from your drive) because it would need to know your password. But it could do less dangerous things, such as deleting things from your home folder, or uploading your files somewhere online maybe. Not nice anyway.
How many Mac users run without ANY password? If you know any, pass on that they need to have a password set, anything will do, because if and when a vulnerability / exploit exists in the wild, it might just try deleting things using nothing as the password, as in my experience a lot of mac users don't use a password.
Also do this (in addition to turning off Java)
1: Turn off Safari's "Open Safe Files" in preferences.
In addition to disabling Java support, Safari's 'Open "safe" files after downloading' must also be disabled to prevent websites from automatically loading a Java WebStart application via a JNLP file
2: If you are running the original user set up with the machine, it being a Admin user and all (not good)
Create another Admin User (lets call it #2) and log into that, change the original Admin to Standard by unchecking "Let this users Administer this computer"
Now log back out and into your regular (now Standard) user. It will require you to enter the Admin 2 name and password to make certain changes. It offers a substancial layer of security.The reason for this is the Java exploit only has the powers of the user being exploited. So if it's a Admin, your rootable (via application alteration using your requested password.) If a Standard user, then just your files.
One is worse than the other and something like this is bound to happen again. So by being a Standard user, at least you don't get rooted (using sudo)And last of all, SHAME ON YOU APPLE!!!
6 months and you did nothing! What you waiting for Snow Leopard?
Ok, I'm finished.