Apple's iPhone might see wider adoption in government use, thanks to the recent validation of a cryptographic module for iOS.
via NIST Computer Security Division
Last week saw the National Institute of Standards and Technology's Computer Security Division granting FIPS 140-2 certification (via TUAW) to Apple iOS CoreCrypto Kernel Module v3.0. The Division tested the cryptographic module on an iPhone 4, iPhone 4S, and iPad running iOS 6.0.
"Apple iOS CoreCrypto Kernel Module is a software cryptographic module running on a multi-chip standalone mobile device and provides services intended to protect data in transit and at rest," the division's report reads.
The iOS module met Level 1 of Federal Information Processing Standard 140-2, the lowest level of security, as it has no required physical security components beyond the standard production-grade iPhone components.
FIPS approval could open a path to wider adoption of the iPhone in government operations. The Department of Defense is said to be close already to approving devices running iOS 6 for use within its operations after conducting its own separate evaluation of the technology.
 Kevin Bostic
Kevin Bostic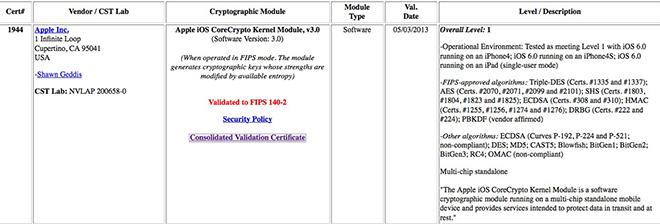








 Christine McKee
Christine McKee
 Wesley Hilliard
Wesley Hilliard
 Malcolm Owen
Malcolm Owen
 Andrew Orr
Andrew Orr
 William Gallagher
William Gallagher
 Sponsored Content
Sponsored Content








15 Comments
It's been possible to compile OpenSSL for iOS ever since Apple released the iPhone SDK (even without CoreCrypto), which means apps have been able to generate strong encryption keys for a long time now.
So the government doesn't want anyone listening to their phone calls? Oh, the sad, sad irony.
@auxio The problem with compiling OpenSSL for iOS is that it doesn't allow the same level of compatibility using CoreCrypto does. CoreCrypto is built-in and can operate at a level OpenSSL can't (third-party apps have forced sandboxing). Just because OpenSSL has approved algorithms doesn't mean OpenSSL used within iOS has been approved. Checking http://csrc.nist.gov/groups/STM/cmvp/documents/140-1/1401vend.htm shows it hasn't. FIPS 140-2 certifies the operating modules within specific devices. Government agencies are required to abide by these certifications. OpenSSL with iOS does not appear to be certified, therefore, it doesn't pass government requirements. Specific third-party applications that implement OpenSSL within iOS can be FIPS certified but this is done on a product by product basis. Now that half of the iOS CoreCrypto package has been certified, third-party applications can be written to use CoreCrypto and not have to go through FIPS certification. This means a lot to application developers and government users.
Specific third-party applications that implement OpenSSL within iOS can be FIPS certified but this is done on a product by product basis. Now that half of the iOS CoreCrypto package has been certified, third-party applications can be written to use CoreCrypto and not have to go through FIPS certification. This means a lot to application developers and government users.
Ah, I see. Thanks for the clarification.
Given that the OpenSSL codebase is largely identical on all platforms, and open source, I'm surprised that it's not easier to just certify a given version of it on a number of platforms. So that, if someone uses that version in their app, they simply need to prove it in order to be certified.
But anyways, looks like CoreCrypto is the way to go if/when I drop older iOS support in my apps.
Just because OpenSSL has approved algorithms doesn't mean OpenSSL used within iOS has been approved. Checking http://csrc.nist.gov/groups/STM/cmvp/documents/140-1/1401vend.htm shows it hasn't.
I checked http://csrc.nist.gov/groups/STM/cmvp/documents/140-1/1401val2012.htm#1747 and it seems that the OpenSSL FIPS module has been approved on iOS 5 (as well as a number of other platforms).