A report on Monday suggests Apple's recently modified OS X app signing policy is the result of an undisclosed Developer Portal security breach that leaked keys for multiple services, including Gatekeeper.
Noting tweets by user @SomeoneSW and one corroborating source, TUAW claims Apple's newly instituted policy forcing developers to re-sign app credentials is the result of a security breach that not only released Gatekeeper keys, but also "many other keys for many other things."
As seen in the tweets embedded below, @SomeoneSW, whose account was seemingly created today, claims inside knowledge of a data breach that released "virtually every key Apple used for anything." The Twitter user said they were approached with a proposal to buy said keys shortly after the undisclosed theft.
Apple could not be reached for comment on the issue.
@marczak @cabel @danielpunkass @mikeash The keys used for Gatekeeper* were stolen in that Developer Portal breach a while back. Consider thi
— Somebody Somewhere (@SomebodySW) August 18, 2014@marczak @cabel @danielpunkass @mikeash s your heads up. *and many other keys for many other things
— Somebody Somewhere (@SomebodySW) August 18, 2014According to the publication, also pilfered was Apple's Enterprise Signing Key, an asset used to sign activation tickets for bypassing iCloud locks. This particular key was used in a previously reported iCloud exploit that supposedly allowed hackers to defeat Activation Lock, the anonymous Twitter user said.
Gatekeeper is a security tool first offered in OS X 10.8 Mountain Lion that protects users from malicious software by placing restrictions on app installation. At its default setting, for example, Gatekeeper allows installation of apps from the Mac App Store and titles signed by developers who have registered through company's Developer ID Program.
The supposed Developer Portal breach would technically let nefarious users sign malicious apps as kosher, prompting Apple to change the way apps are recognized by Gatekeeper in OS X 10.9.5 Mavericks and the upcoming OS X 10.10 Yosemite.
 Mikey Campbell
Mikey Campbell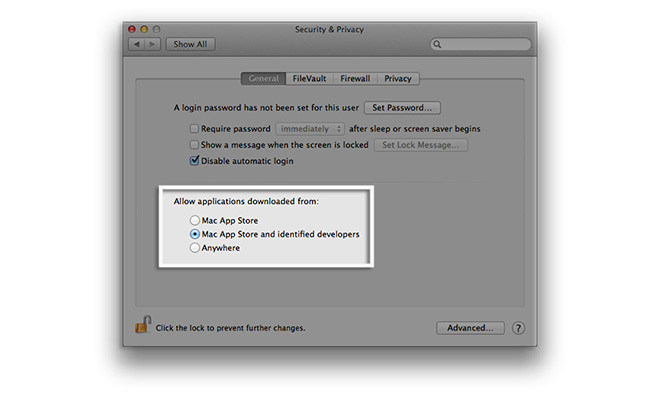







-m.jpg)






 Christine McKee
Christine McKee
 Malcolm Owen
Malcolm Owen

 Charles Martin
Charles Martin


 Mike Wuerthele
Mike Wuerthele



-m.jpg)






6 Comments
Sorry I have to say that but : duh!
I don't see any other reason that could explain the change.
Edit: Just to be clear, I'm not complaining about the article as it does bring some interesting new information. But obviously, a security issue was the reason behind the code signing change.
If true I am a little disappointed in Apple! If you remember that breach Apple took the dev portal down and then the iCloud in Australia incidents happened so its all lining up together. At the time Apple recommended every one change your password and don't use the same password on all websites. Did Apple lie or is it just a coincidence that all these these things happened in an order and this is now leaked to confirm it? Thing that is odd it was only random people in Australia, it wasn't everyone all over the place. So it doesn't sound legit there. Not sure what to think!
one question though. as I understand it this need to resign apps is tied to the whole 10.10 release. As in if you don't do it then your app even if in the MAS won't pass through gatekeeper.
but if this was tied to some security breach 'a while ago' wouldn't they have demanded the resigning of apps and now. Why have folks potentially in danger cause of the swiped keys for weeks
For the past several years now, the Public Key Infrastructure (PKI) of every certificate authority in the world has been under attack by hackers (known and unknown) attempting to steal the private signing keys used to sign the client digital certificates used for SSL site identification and also the certs used for code signing. I guess this is just the latest PKI breach coming to light. Of interest, Google's Certificate Transparency project (http://www.certificate-transparency.org/) is an attempt to detect (in near real time) SSL certificates that have been mistakenly issued by a certificate authority or maliciously acquired from an otherwise unimpeachable certificate authority. Google claims this also makes it possible to identify certificate authorities that have gone rogue and are maliciously issuing certificates. I don't believe I have heard of any similar project to identify rogue certs that are being used for code signing. A good article reviewing all the recent certificate authority misadventures is at: http://resources.infosecinstitute.com/cybercrime-exploits-digital-certificates/ A current list of 'bad' SSL certificates (issued in error or through manipulated PKI issuance) identified by abuse.ch associated with malware or botnet activities is at (https://sslbl.abuse.ch/).
[quote name="cashxx" url="/t/181869/rumor-undisclosed-security-breach-cause-of-apples-new-gatekeeper-app-signing-policy#post_2581094"]If true I am a little disappointed in Apple! If you remember that breach Apple took the dev portal down and then the iCloud in Australia incidents happened so its all lining up together. At the time Apple recommended every one change your password and don't use the same password on all websites. Did Apple lie or is it just a coincidence that all these these things happened in an order and this is now leaked to confirm it? Thing that is odd it was only random people in Australia, it wasn't everyone all over the place. So it doesn't sound legit there. Not sure what to think![/quote] I don't see a link to the icloud incidents to be honest - that did go a little wider than Australia but it was all traced to one individual who was caught and charged - nobody else has been able to do anything similar and the vast, vast majority of users were never affected - to me it sounds much more like he had a list of shared passwords (perhaps from some Australian based service) rather than something like this which would give him random access to the whole userbase.