A recently-discovered vulnerability in Apple's mobile operating system could allow attackers to trick users into replacing legitimate apps that have access to a variety of personal information — Â such as banking apps — Â with hacked versions that relay that information to malicious actors.
Hacked apps could be distributed via email or through web links and installed using iOS's enterprise provisioning system, which allows apps to be added to the device from outside of the App Store. The vulnerability, dubbed a "Masque attack" by security firm FireEye, is possible because iOS does not verify that the code signing certificate is the same for apps that use the same bundle identifier.
An app with the same bundle identifier as Bank of America's mobile banking, for example, could be installed over top of the legitimate Bank of America app, mimicking the latter's user interface but sending login data back to the attackers' servers. Default apps like Safari and Mail are not affected.
FireEye notified Apple of the issue on July 26, but iOS versions up to and including iOS 8.1.1. beta continue to be vulnerable. Apple has yet to respond to the public disclosure.
The Masque attack could be considered an advanced form of phishing, a social engineering attack usually propagated via email in which users are tricked into submitting sensitive information to real-looking but ultimately fake websites. Phishing continues to be a huge problem, despite special protections built into web browsers and email clients designed to thwart the attack.
 Sam Oliver
Sam Oliver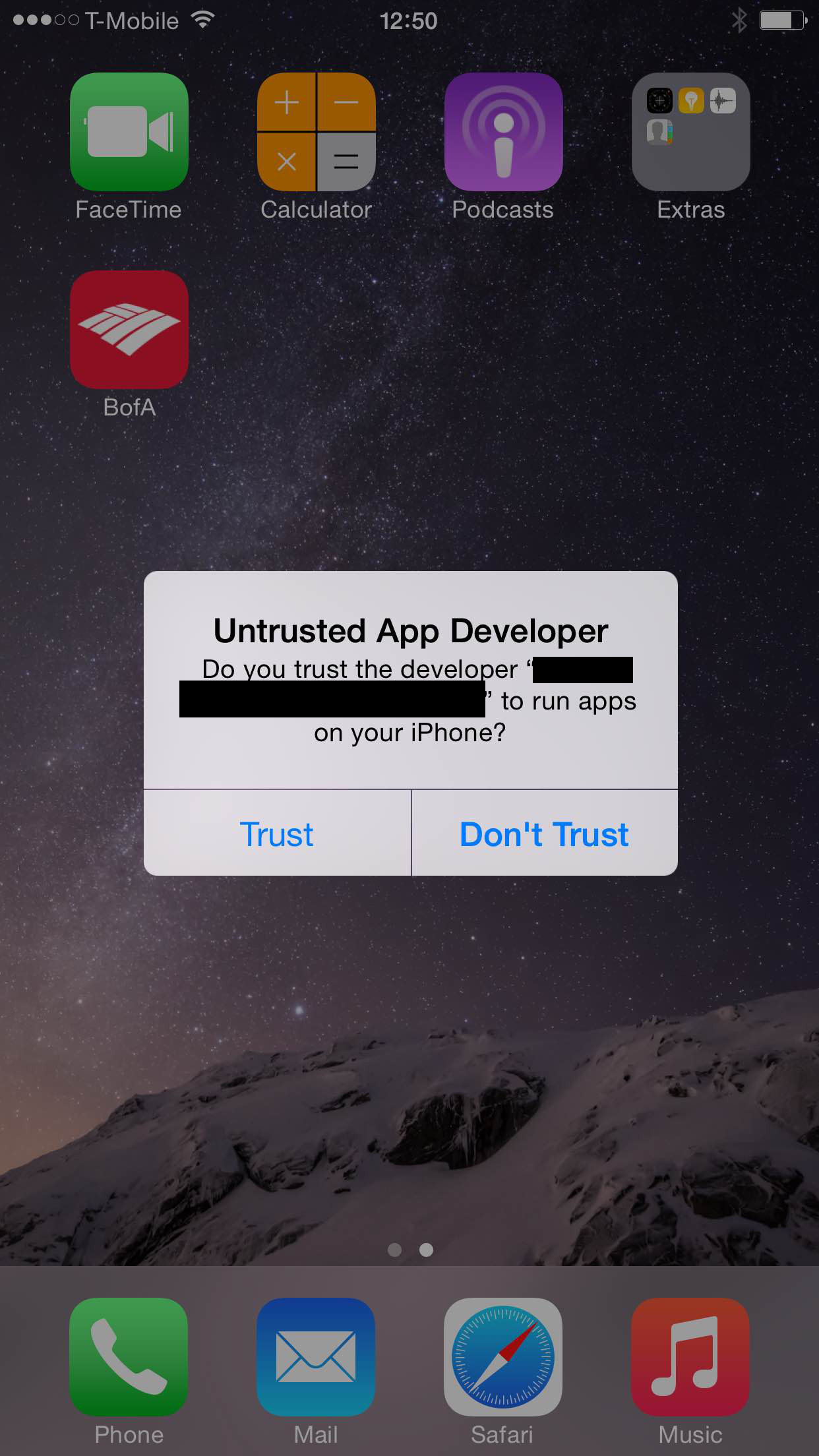








 Malcolm Owen
Malcolm Owen
 Mike Wuerthele
Mike Wuerthele
 Andrew Orr
Andrew Orr
 Andrew O'Hara
Andrew O'Hara

 William Gallagher
William Gallagher

 Christine McKee
Christine McKee



-m.jpg)


25 Comments
Requires a user to accept an enterprise certificate of a company they don't work for, and Apple to not revoke the cert. If you choose to download something from outside the app store, there will always be a risk.
This is an attack that can only happen if you download an App from a third party site or fall for a trick via e-mail or a Website. Apple explicitly warns customers to download Apps from the official Apple App Store only. Apple spends a lot of time and money checking these Apps to protect the customer. It is not Apple's fault if users choose not to use this protection or are careless Internet users in general. These kind of attracts are everywhere on the Internet and apply to all software that is downloaded. The fact that iOS can also be attract in this manner should not be labeled as a venerability or perceived as something Apple has to fix.. As has been said many time, it is impossible to protect people from their own stupidity and Apple shouldn't be expected to either.
So, when are the AI Fanboys gonna come out in droves to debunk this article. Obviously, the author is a Samsung or Google plant.
So, in other words there is almost no risk of this happening. Thanks.
So to be sure I understand correctly, the only way to install apps outside of the app store is to jailbreak your phone right? So this would not be a threat to an iPhone unless it was jailbroken?