Google's bug hunt to identify software flaws in Android has revealed 11 exploitable flaws in Samsung's software included on its high end Galaxy S6 Edge flagship, including "a substantial number of high-severity issues," within just a week of looking.
Google is facing even greater challenges to secure Android than Microsoft faced in its battles to contain viruses and security exploits for Windows XP in the early 2000s, because Google has less control over the products that ship with Android branding.
As Google's Project Zero team itself noted, Android's licensees "are an important area for Android security research, as they introduce additional (and possibly vulnerable) code into Android devices at all privilege levels, and they decide the frequency of the security updates that they provide for their devices to carriers."
Within the course of a week, teams at Google challenged the "security boundaries of Android that are typically attacked," with an aim to see if they could gain remote access to users' contacts, photos and messages, ideally without any user interaction; exploit the Android phone via an app installed from Google Play that did not require the granting of any permissions by the user; and install an attack on the device that could survive a factory wipe, maintaining a security infection.
The teams discovered a Samsung process that runs with system privileges, which unpacks ZIP file downloads from a given URL. "Unfortunately," Google noted, "the API used to unzip the file does not verify the file path, so it can be written in unexpected locations." [...] "this was trivially exploitable using the Dalvik cache using a technique that has been used to exploit other directory traversal bugs."
Another bug, in Samsung's email code, failed to authenticate when handling Android intents, an OS-level feature that lets apps pass commands between themselves. Without authenticating, Samsung's email software allowed an unprivileged app to hijack emails and forward them to other account.
Google noted that the mistake opened up "easy access to data that not even a privileged app should be able to access," further highlighting how little control Google has over Android in the hands of its licensees.
Google also found that buffer overflow flaws in three Samsung drivers "could be used by bugs in media processing, such as libStageFright bugs, to escalate to kernel privileges."
Five exploitable flaws were also found in Samsung's image processing code, two of which could allow privilege escalation when a rogue image file is opened in Samsung's Gallery app, while the other three could be triggered simply by downloading an image. "It was also surprising that we found the three logic issues that are trivial to exploit. These types of issues are especially concerning, as the time to find, exploit and use the issue is very short" - Google
Google expressed surprise at how quickly it could find these exploits, adding that "it was also surprising that we found the three logic issues that are trivial to exploit. These types of issues are especially concerning, as the time to find, exploit and use the issue is very short."
Google noted that Samsung's use of SELinux "made it more difficult to investigate certain bugs, and to determine the device attack surface," but that it also "found three bugs that would allow an exploit to disable SELinux, so it's not an effective mitigation against every bug."
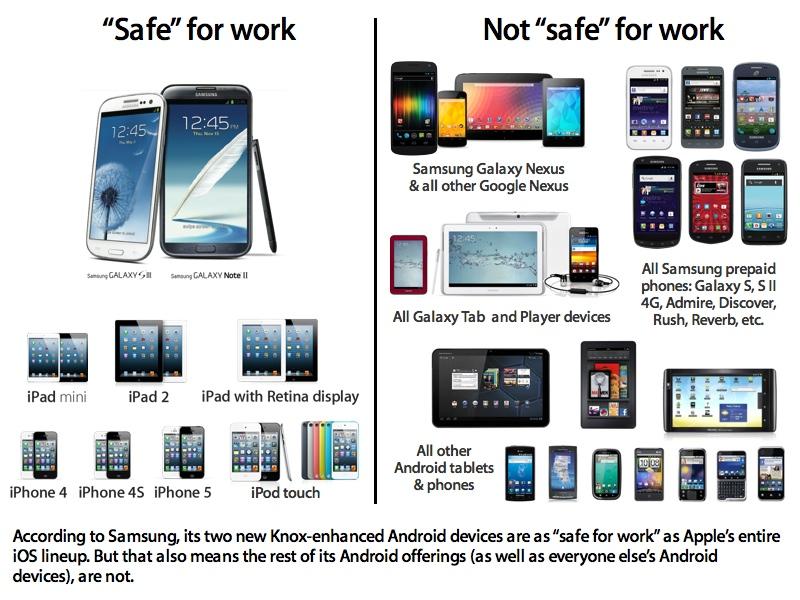
Samsung a leader in Android security, bugs
Samsung and Google have worked to patch the most serious bugs found, but the findings of just one week of bug hunting highlight the difficulty in securing even the most expensive models of Android phones on sale from its largest licensee, one that has a committed interest in wooing government and enterprise buyers with its self-signed seal of approval brand of "SAFE" or "Samsung for Enterprise."
Android's security problems have compounded since 2011, when researchers from North Carolina State University demonstrated that Android's permission-based security system could be easily circumvented due to flaws in the software that licensees— including HTC, Samsung, Motorola and even Google's Nexus-branded phones— were adding to their devices.
After reporting issues to Android vendors, the group noted that "we experienced major difficulties with HTC and Samsung," adding that they "have been really slow in responding to, if not ignoring, our reports/inquiries."
The blind patching the blind
Flaws in Google's own Android code are also a serious issue, complicated by the fact that few users are able to update their devices to a recent version of Android. Currently, three-quarters of Android devices on Google Play are running a version older than last year's Android 5.0 Lollipop.
In the summer of 2014, Google's chief executive Sundar Pichai introduced Android 5 with contributions from Samsung's Knox security software (that makes up the foundation of its SAFE initiative) ostensibly working to secure the platform.
A year later, Google has launched another new version of Android before seeing even a quarter of its installed base adopt last year's Android 5, making it somewhat ironic that the newest Android software has already been undermined by flaws in code added by Samsung itself.
 Daniel Eran Dilger
Daniel Eran Dilger







-m.jpg)






 Brian Patterson
Brian Patterson
 Charles Martin
Charles Martin


 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher
 Christine McKee
Christine McKee
 Marko Zivkovic
Marko Zivkovic









58 Comments
Just wow ...
What's today's word? "Schadenfreude"
What's today's word? "Schadenfreude"
Or as Phil Schiller would say: Shenanigans. Oh wait, that was for Samsung benchmark cheating.
zzzzzzzz, someone wake me up
the author forgot to mention: Conclusion A week of investigation showed that there are a number of weak points in the Samsung Galaxy S6 Edge. Over the course of a week, we found a total of 11 issues with a serious security impact. Several issues were found in device drivers and image processing, and there were also some logic issues in the device that were high impact and easy-to-exploit. The majority of these issues were fixed on the device we tested via an OTA update within 90 days, though three lower-severity issues remain unfixed. It is promising that the highest severity issues were fixed and updated on-device in a reasonable time frame. I'm all for android bashing as I am not a fan of it whatsoever but don't sink to this level. iOS and OS X have had security issues before which took Apple a while to patch also, how do you think they jailbreak iPhones? Security holes..