Hackers have worked out a way to "jailbreak" the Nintendo Switch by attacking the game console's web browser, a technique that reused a vulnerability discovered in early 2016 commonly used to jailbreak iPhones running iOS 9.3.
A prolific hacker going by "qwertyuiop," previously known for iOS and PlayStation 4 jailbreaks, posted a screenshot of a supposed Webkit exploit on the handheld console on March 11, reports Wololo. A proof of concept for the hack has also been published by developer LiveOverflow today, based on the information revealed earlier.
According to qwertyuiop, he made a slight alteration to his existing iOS Webkit exploit to remove iOS-specific code. The proof of concept relies on hosting files on a local web server, then using tools to force the Switch's browser to access the files.
The original exploit, CVE-2016-4657, affects Webkit versions before 9.3.5, and is described by the National Vulnerability Database to allow "remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted web site." Apple has already patched this vulnerability, protecting users who have updated their iOS devices, but it appears Nintendo did not use a later and more secure version of Webkit in its browser.
The vulnerability could allow hackers the ability to install their own software on the Switch, opening up the possibility of using it for homebrew projects, or for playing pirated games. Such exploits are typically patched by console producers relatively quickly, especially shortly after the launch of new hardware, so a fix from Nintendo to close the vulnerability is likely to arrive in the near future.
The Nintendo Switch does include a web browser, though not one intended for typical Internet use. The browser is effectively only included for a limited number of situations, such as to give users the ability to log into public Wi-Fi hotspots, and has been restricted from being used for alternative purposes, but Nintendo may choose to introduce full browser functionality in a future update.
 Malcolm Owen
Malcolm Owen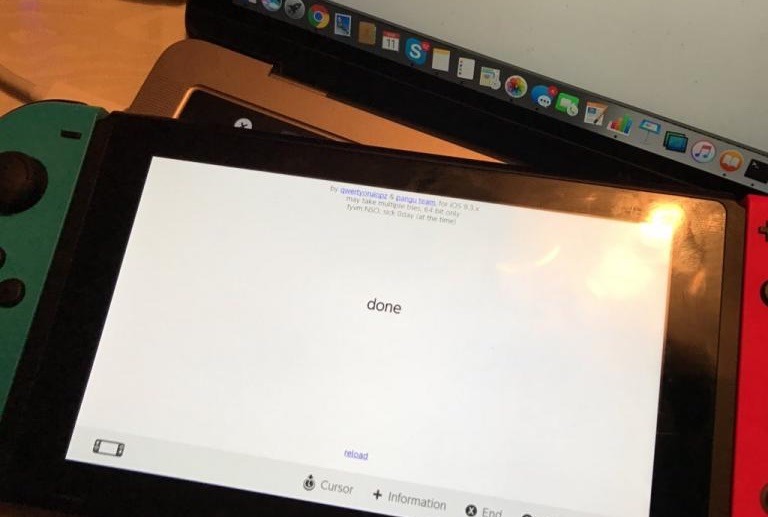







 Amber Neely
Amber Neely
 William Gallagher
William Gallagher


 Oliver Haslam
Oliver Haslam

-m.jpg)






4 Comments
You would think that manufacturers would be smarter than this -- including old versions of software with known vulnerabilities makes it so much easier for hacks rather than make the hackers actually have to do some hard work on finding all-new holes. Did they install SSH-1 also?
People actually want to buy this thing? Why?