Nefarious actors using a mobile Safari exploit to extort iTunes gift cards from unwitting iOS device users will need to look elsewhere, as Apple patched the web browser flaw as part of Monday's iOS 10.3 update.
Using the vulnerability, which leveraged the way Safari handled JavaScript pop-up windows, ransomware scammers primarily targeted users viewing pornographic material, bootlegged music and other content, reports ArsTechnica.
In practice, the flaw present in iOS 10.2 allowed scammers to enact an endless loop of pop-ups, effectively locking users out of the browser. The pop-ups would continue — some incorporating threatening messages — until victims paid a "fee" in the form of an iTunes gift card code delivered to a phone number via text.
Explaining the scam, mobile security firm Lookout called the exploit "scareware," as social engineering was key to the method's success. Scammers would carry out attacks from domains like "pay-police[.]com" and others named to evoke legitimate law enforcement authorities.
Combined with customized web content published to owned domains, the goal was to elicit fear from targeted users. As seen in the example above, exploit code planted on certain websites would lead users to a landing page containing text claiming their device was locked "for illegal pornography."
The attack would revert to a never-ending loop of pop-ups reading "Cannot Open Page." Tapping "OK" would invoke yet another pop-up containing the same message.
"The attackers effectively used fear as a factor to get what they wanted before the victim realized that there was little actual risk," writes Lookout researchers Andrew Blaich and Jeremy Richards.
Lookout notes a cache reset, performed by navigating to Settings > Safari > Clear History and Website Data, would rectify the pop-up loop issue, but users not familiar with mobile Safari's inner workings were unlikely to discover the simple fix. Further, victims were perhaps unwilling to ask for help due to the content of pages where the attack code was embedded.
Lookout shared the details of the scareware campaign with Apple after discovering it last month. The iPhone maker subsequently patched the flaw by making JavaScript pop-ups a per-tab event, rather than app-wide.
 Mikey Campbell
Mikey Campbell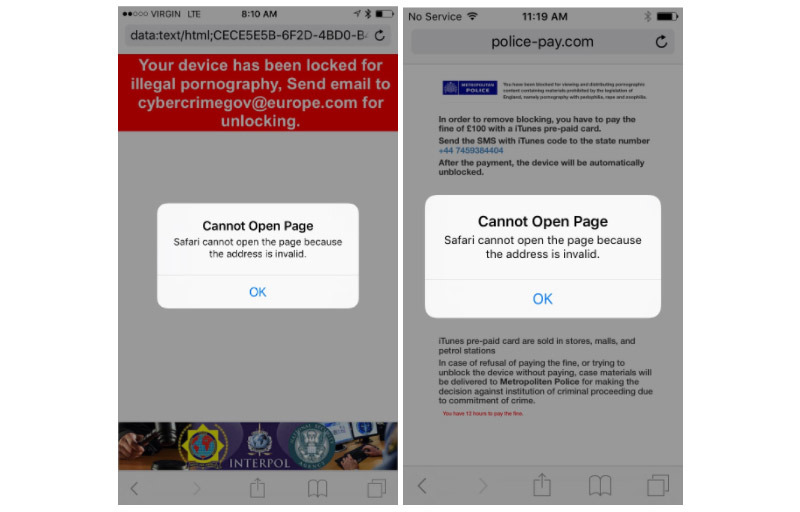






-m.jpg)





 Wesley Hilliard
Wesley Hilliard
 Malcolm Owen
Malcolm Owen
 Amber Neely
Amber Neely
 Christine McKee
Christine McKee
 Andrew Orr
Andrew Orr

 Mike Wuerthele and Malcolm Owen
Mike Wuerthele and Malcolm Owen








9 Comments
This is not just fake ransomware, a lot of sketchy URL redirects use this same technique. The trick to breaking the JavaScript/popup loop is to put the iPhone/iPad in airplane mode, at that point you can kill the session and/or kill Safari via the task manager.