A series of previously unknown Windows hacking tools used by the U.S. National Security Agency has been leaked, enabling "zero day" exploits to be used against millions of Windows PCs to deface websites, lock up systems to demand a ransom payment or to steal emails and other data.
As noted in a report by Lorenzo Franceschi-Bicchierai for Motherboard, the NSA tools were leaked by hacker group known as the "Shadow Brokers."
The package of exploits includes "Fuzzbunch," and easy-to-use hacking tool with basic instructions that even non-technical users could follow to gain control of PCs running multiple versions of Microsoft's Windows prior to the latest Windows 10, specifically Windows XP, Vista, 7 and 8 as well as server versions including NT, 2000, 2003, 2008 and 2012.
The report cited a former employee of the U.S. Department of Defense as saying "it's not safe to run an internet facing Windows box right now," and that the payload of exploits is "the worst thing since Snowden."
Motherboard previously cited comments from security architect Kevin Beaumont, who noted that "all of the Windows implants are new to VirusTotal [an online file scanning tool], which suggests they've not been seen before."
More Windows PCs are vulnerable vs. those on on modern software
According to web browser stats from NetMarketshare, only 25 percent of web users are using Microsoft's latest Windows 10 (which was released in the summer of 2015), while over 66 percent of active web users are using older versions of Windows that are vulnerable to the attacks launched by the released tools.
There are many Windows PCs that are connected to the Internet but do not generate web traffic— particularly back end servers and other utilitarian machines. A worm or virus could easily launch broad exploits at Windows users and find plenty of vulnerable machines to steal data from or recruit into global botnets of exploited PCs.
Microsoft has worked aggressively to upgrade users to Windows 10, but the vast majority of PCs worldwide remain stuck on older versions with known problems. The new cache of hacker tools makes it that much easier to exploit those users.
A spokesperson for Microsoft said that it is "reviewing the report and will take the necessary actions to protect our customers."
Apple's security through obscurity (and update superiority)
Apple's installed base of Macs and iPad users are not affected by exploits found in Windows (apart from Macs intentionally booted up into an old version of Windows by the owner). That's a feature Apple has long advertised for Macs, and has recently noted in its ads for iPad Pro.
In part, Apple's limited exposure to malware and exploits comes from its divergence from the monoculture of Windows (or Android) software, a sort of "security by obscurity," where the easiest to use hacking tools simply don't work because the platform isn't as easy to target as Windows PCs and Android devices are.
Apple's installed base of computer users has grown rapidly however. Horace Dediu of Asymco recently noted that there are about 100-150 million Macs in active use and an installed base of over 300 million iPads. That's about the same as the 400 million PCs in the installed base of Windows 10 that Microsoft cited at its Ignite conference last fall.
The difference is that there is at least another 400-600 million PCs that are running vulnerable versions of Windows. Apple also has an even larger installed base of iPhones, but most of those are updated.
So the larger reason why Macs and iOS devices are protected from the routine efforts to hack into Android and Windows is due to Apple's far faster ability to distribute new OS updates, which it does without cost. Apple's system update efforts have resulted in the majority of iOS users rapidly adopting the latest version and regular new patches between major updates.Macs and iOS devices are protected from the routine efforts to hack into Android and Windows due to Apple's far faster ability to distribute new OS updates
As of February 20th, Apple reports that 79 percent of iOS users are on the latest iOS 10, while another 16 percent are on iOS 9, both of which are at least as recent as Microsoft's Windows 10.
Apple does not appear to report macOS version adoption figures, but Go Squared reports that 44 percent of Macs are using the latest macOS Sierra while another 21 percent are on macOS El Capitan, both of which (65 percent total) are as new as Windows 10. The same site reports adoption of Windows 10 at 49 percent, with a nearly equal number still on Windows 7.
The same site reports that 89 percent of iOS users are on the newest iOS 10, as of April.
Google notes that as of April, only 4.9 percent of devices actively accessing Google Play are using the latest Android 7 Nougat, and only another 31 percent are on 2015's Android 5 Marshmallow, released alongside iOS 9. The majority of its active users are on versions of Android older than that, most of which will never be updated. Users in other regions, particularly China, are much less likely to use Google Play and even less likely to be updated to recent versions of the OS.
 Daniel Eran Dilger
Daniel Eran Dilger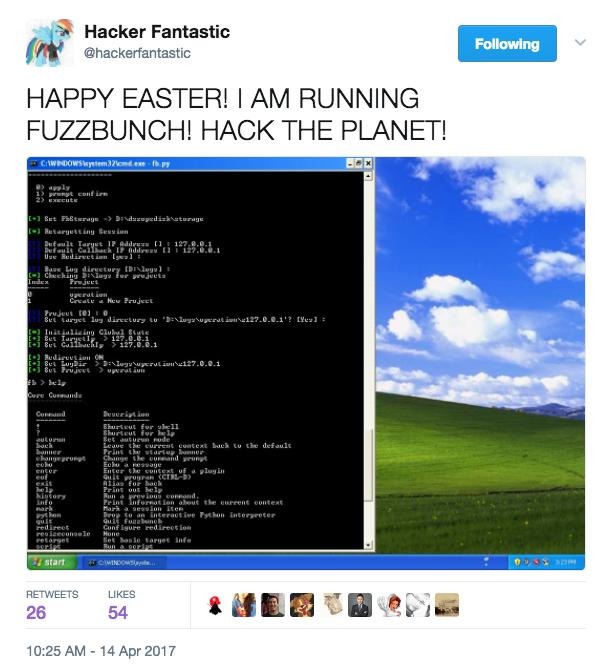







-m.jpg)






 Christine McKee
Christine McKee
 Marko Zivkovic
Marko Zivkovic
 Mike Wuerthele
Mike Wuerthele

 Amber Neely
Amber Neely
 Sponsored Content
Sponsored Content
 Wesley Hilliard
Wesley Hilliard










26 Comments
"Security through Obscurity"? I thought we got rid of that statement a long time ago. macOS and iOS are not obscure operating systems, at least not anymore. I have to wonder if Microsoft is actually behind this since they want everyone to upgrade to Windows 10. I'm seeing other articles about Microsoft's changing policies on how and on which platforms Windows is allowed to run. Adding this to the mix and you have to wonder.
How does locking/ransom work on a home computer? If it's locked, how can you use it to see how much to pay and who to send it to? If the ransom is more than a couple of grand, why not just buy a new Mac and restore from iCloud?