A new way of attacking macOS with malware has been detailed by security researchers, with malicious online advertising found to have used steganography to disguise its payload within the ad's image files, in order to fool security systems.
Analyzed by Confiant and Malwarebytes, an attempt to infect Macs from January 11 until January 13 was performed by a "malvertizer" dubbed "VeryMal" by the firms. It is believed that the attempted attack ad was viewed on as many as 5 million Macs during the brief period of time it was active.
To those who saw the ad, the attack went down a familiar tactic of displaying notices that the Adobe Flash Player needed to be updated, and urged users to open a file that would attempt to download in their browser, writes Confiant. Those who accepted the download and ran the malware ended up infecting their Mac with the Shlayer trojan.
While many attempts to obscure an attack via advertising fail to dupe the various protection systems in place in advertising networks and on user's desktops, the attempt is notable for hiding the payload of the attack within the visible advert itself. The graphic file had hidden code, using steganography, that required other non-malicious code to examine the image file for extraneous data, which was then used as a payload.
Specifically, the code would create a Canvas object, grab an image file from a specific URL, and define a function that checks if a specific font family is supported by the browser. If a check for Apple fonts failed, nothing would happen, but on success, the underlying data in the image file would be looped through, with each loop determining a pixel value that became an alphanumeric character. This was turned into a string and executed.
Despite containing the payload, the image itself can be viewed without harm. It is only harmful when the code is run on the file, followed by the browser being redirected to a link included in the payload.
"As malvertizing detection continues to mature, sophisticated attackers are starting to learn that obvious methods of obfuscaton are no longer getting the job done," writes Eliya Stein of Confiant. Noting that common JavaScript obfuscators result in a "very particular type of gibberish" that is easy to spot, Stein adds "Techniques like steganography are useful for smuggling payloads without relying on hex encoded strings or bulky lookup tables."
VeryMal had performed similar attacks in the past, including targeting Macs and iOS in December, but the latest attempt is a subtle shift for the outfit to a less detectable method.
While macOS is generally easier to protect compared against other operating systems like Windows, it is still possible for bad actors to attempt to infect or acquire data from a target system. Mac users should continue to be wary of online notices urging to install or to update software from unofficial sources, and to closely scrutinize such notices to determine if they are indeed genuine. Additionally, users should not authenticate any request from the operating system, without knowing what it is for, and why it is asking.
Malware continues to be a problem for online users, but is becoming more of an issue for those using macOS, with seemingly more frequent attempts to defeat its security being discovered. It is not only limited to advertizing-based attacks, with reports in September noting even some apps in the Mac App Store were performing malicious actions, such as extracting a user's data.
Apple itself has also come under fire from critics for failing to share definitions of existing threats with third-party antivirus companies in a timely fashion.
 Malcolm Owen
Malcolm Owen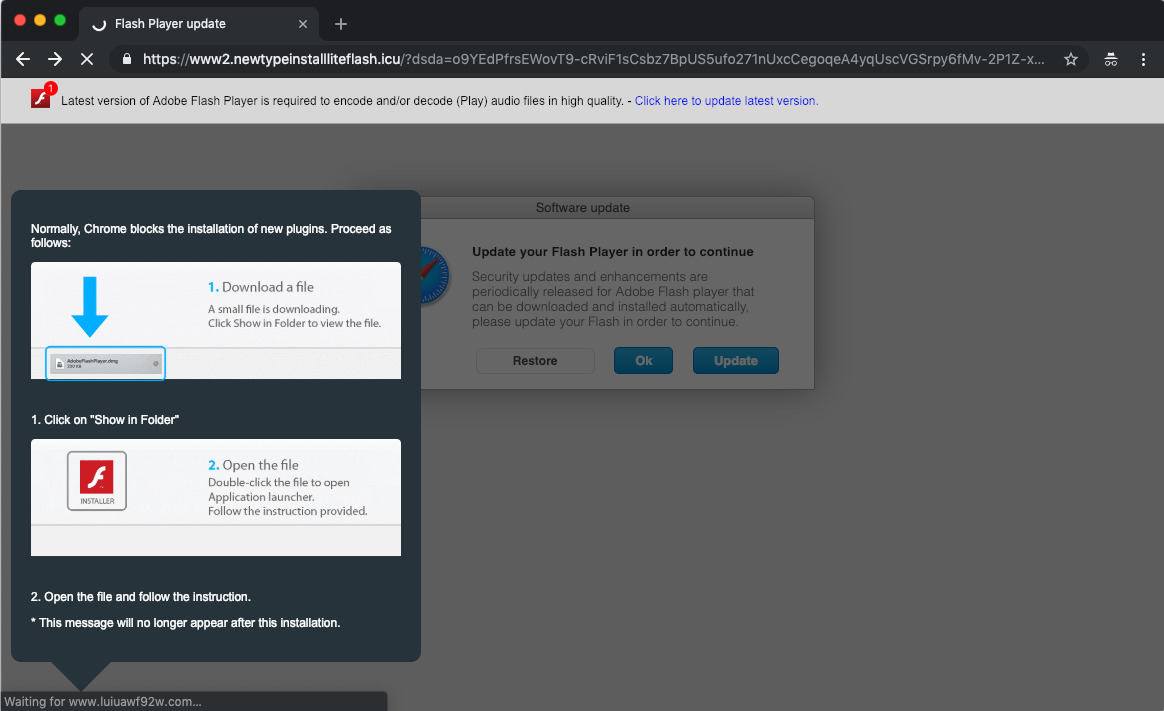







-m.jpg)





 Marko Zivkovic
Marko Zivkovic
 Wesley Hilliard
Wesley Hilliard
 Amber Neely
Amber Neely


 William Gallagher
William Gallagher

 Christine McKee
Christine McKee




-m.jpg)



15 Comments
Time for the penalty to be drastically increased. Eternity in a cell watching Big Brother maybe?
What is an “ad?” Oh that’s right, I use AdBlock so I never see those pernicious snids...
I use adblock too but ads still get through.
Can someone tell me how to block these battery draining ads such as on this site:
https://www.sfgate.com/local/article/Selfieville-Monterey-tickets-golden-state-theatre-13558792.php
I'm sure there is malware festering all over the place there.
So wait... the malware was Adobe Flash, right?