A security researcher on Monday revealed a zero-day flaw — and the questionable use of a local host server — in the Mac client of popular video conferencing service Zoom that allows websites to force a user into a call with their camera enabled.
Discovered and made public by researcher Jonathan Leitschuh after a traditional 90-day grace period, the Zoom vulnerability impacts a variety of web browsers running on Mac, including Safari, Chrome and Firefox.
Detailed in a proof of concept, the flaw allows websites to initiate a video call on any Mac that has, or in some cases has had, the Zoom app installed. Depending on Zoom's app version, a nefarious website is able to trigger a video call with a simple launch action or an iframe exploit.
In Leitschuh's proof of concept, clicking a link opens the Zoom client with video enabled unless a user explicitly elected to turn off video streaming when joining a new meeting. Audio is also disabled by default.
AppleInsider confirmed the vulnerability is present in the latest version 4.4.4 of Zoom's Mac app.
Perhaps more troubling is the revelation that Zoom creates and constantly runs a local web server as a background process on a host machine. The strategy was employed as a "workaround" to changes made in Safari 12, an adjustment made in efforts to maintain the app's streamlined user experience, Zoom said in a statement to ZDNet.
With every Zoom installation, the local server runs on port 19421, through which Zoom calls can be initiated and updates delivered. Ironically, Zoom rarely, if ever, conducts an auto-update process despite the always-running server and open port.
Making the situation worse, uninstalling Zoom does not disable the server, which remains active and can re-install the client app without user interaction. According to Leitschuh, merely visiting a webpage can trigger re-installation.
Zoom in its statement to ZDNet defended the move, saying a web server is a "legitimate solution to a poor user experience, enabling our users to have seamless, one-click-to-join meetings, which is our key product differentiator."
Leitschuh informed Zoom of the zero-day in March. The company confirmed the flaw, but only offered a barebones fix that includes signing HTTP GET requests. Zoom requested an extension when Leitschuh more recently divulged the iframe vulnerability, but the researcher moved ahead with disclosure, saying the core issue — the local server — remained in the company's patch.
Zoom notes users have the ability to avoid exposure by electing to disable video when joining a meeting the first time the program runs. Users must be proactive to maintain that protection, however.
"All first-time Zoom users, upon joining their first meeting from a given device, are asked whether they would like their video to be turned OFF," Zoom told ZDNet. "For subsequent meetings, users can configure their client video settings to turn OFF video when joining a meeting. Additionally, system administrators can pre-configure video settings for supported devices at the time of install or change the configuration at anytime."
A release scheduled for July will save a new user's initial video access settings across all connected platforms, Zoom said. Further, the company has removed the ability for a host to automatically join a call with video enabled, ZDNet reports.
While Zoom will not go so far as to remove the localhost server, users can kill and delete the offending "feature" with Terminal commands detailed in Leitschuh's original report.
 Mikey Campbell
Mikey Campbell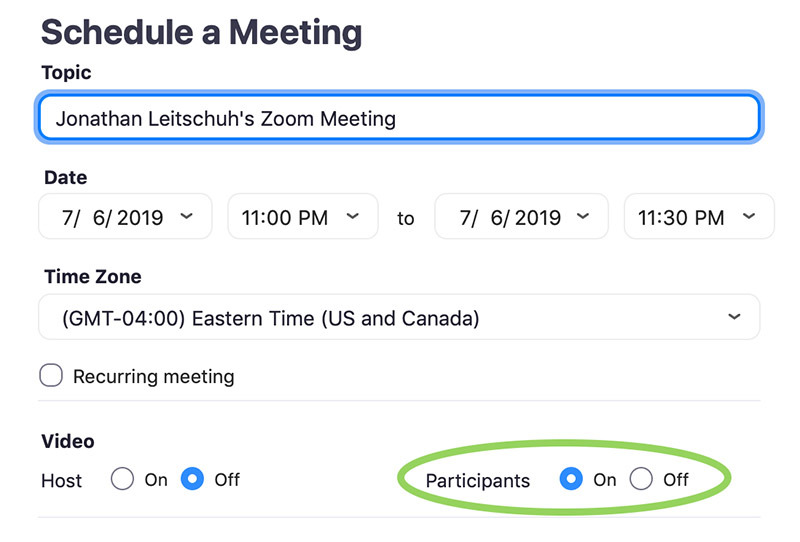

-m.jpg)






 William Gallagher
William Gallagher
 Andrew O'Hara
Andrew O'Hara
 Wesley Hilliard
Wesley Hilliard

 Malcolm Owen
Malcolm Owen
 Marko Zivkovic
Marko Zivkovic

 Chip Loder
Chip Loder




-m.jpg)




7 Comments
I hate software that installs always-on anything.
Their actual client software installation process also subverts the normal MacOS expected process. The unusual approach fails to provide the user the opportunity to review the product and installation files prior to installation. Specifically, they use the “This package will run a program to determine if the software can be installed.” step to actually perform the actual installation and to write configuration files outside of the program causing MacOS to run the software at each subsequent Startup!
I have been in contact with the developer on this topic and they eventually provided a different installer that behaved as a normal installation. However they declined to make this the default download from their site. So my advice; avoid Zoom.
These guys seem to be living in the past, for many years now you've had to put security foremost in networking products even if it does cause the user some extra steps. Misleading the user on installation isn't good either, let alone hidden reinstallation.
"
I am pleased never to have used the software, they will need a pretty convincing update to satisfy those that have.
Expert: „Guys, you have a serious security issue“
Zoom: „blah marketing blah“
Expert: „No, seriously, you have a real problem here“
Zoom: „blah marketing blah“
I hope someone sues them.