Following the disclosure — and wide media coverage — of a zero-day flaw in video conferencing service Zoom's Mac client that enables easy access to a user's camera feed, the company on Tuesday reversed course and said it plans to issue a fix for the vulnerability.
Announced in a post to Zoom's official blog, the emergency security patch will remove a local web server the company is using to bypass a Safari 12 protection mechanism, as well as allow users to completely uninstall the app.
The move is a course reversal for Zoom, which as recently as Tuesday said both actions would be difficult to implement. Zoom previously defended its use of a local host server to bypass built-in Safari security protocols in favor of a streamlined user experience.
Apple's latest Safari 12 requires users to by interact with a dialogue box when a website or link attempts to launch an outside app. Zoom, which prides itself on a streamlined UX and one-click-to-join video meetings, developed a workaround in the creation of a local host server that constantly runs as a background process.
As detailed by security researcher Jonathan Leitschuh, nefarious websites can take advantage of the local web server to trigger a video call with a simple launch action or an iframe exploit, automatically activating a Mac's webcam and connecting to a meeting without user consent. All Zoom Mac clients are vulnerable through Safari, Chrome and Firefox unless a "Turn off my video when joining a meeting" option is ticked in the software's settings menu.
In addition to granting potentially unwanted webcam access, the local server remains on a host machine even when Zoom is uninstalled and can re-install the client app without user interaction.
Zoom initially said it would not remove the server feature, but it appears the company had a change of heart after its CEO, Eric Yuan, discussed security concerns in a "Party Chat" with Leitschuh and various members of the Zoom community on Monday. That meeting, conducted through Zoom, was open to all comers and could be accessed through a proof of concept link provided in the security researcher's original report.
Along with removing the local host server, Zoom's Tuesday patch will also include a menu bar option to completely uninstall the Mac client. Earlier on Tuesday, the company said it did not have an "easy way to help a user delete both the Zoom client and also the Zoom local web server app on Mac that launches our client," saying the process had to be completed manually through Terminal.
The patch is expected to arrive later tonight.
 Mikey Campbell
Mikey Campbell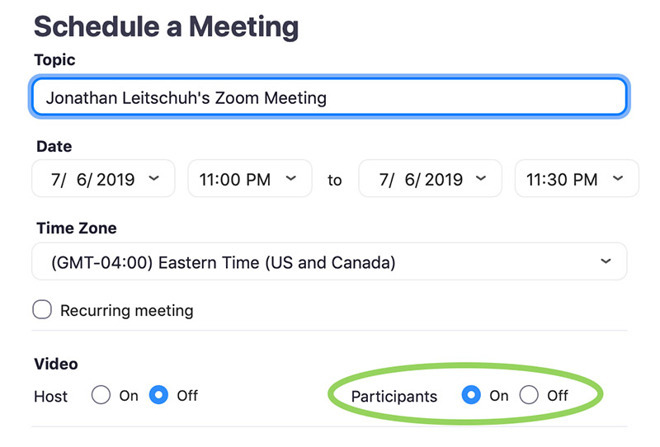







-m.jpg)





 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher

 Wesley Hilliard
Wesley Hilliard



 Christine McKee
Christine McKee




-m.jpg)




11 Comments
Riiiight. A company that knows how to install a local web server on a custom port and have it launch every time the system boots up, is somehow incapable of writing a shell script to automate the removal of that tool and hook into the OS frameworks that allow a temporary escalation to higher privileges for that script. Not like I ever used Zoom, but this convinces me to advocate against them and suggest a clean OS reinstall to anyone who's ever used the product.
“Difficult”, read as “we don’t wanna”.
Maybe their lawyers let them know they really ought to.
Gee, Zoom, that sure looks like a cleverly designed FEATURE more than a flaw to me.
What bothers me about this is that the user isn’t in control of OUR OWN CAMERA.
And I don’t even blame Zoom.
Sure, I’ll never use their software now as that’s an evil and creepy thing to offer - say an employers wants to force you into a video conference and you don’t even know you’re being seen... evil.
This is an APPLE issue. It shouldn’t even be possible for a software maker to do enable this.
There should ALWAYS be a OS LEVEL approval for the camera to activate.
An installer app can call on it, but the user should approve a prompt AT THE OS LEVEL.
this is beyond stupid.