Apple's effort to develop a standardized format for one-time passcodes sent through SMS messages is moving forward with the help of Google engineers, as the proposal this month garnered official status as a Web Platform Incubator Community Group (WICG) specification draft.
Announced in an updated GitHub explainer, an initial report of Apple's "Origin-bound one-time codes delivered via SMS" project was published by the WICG on April 2. The draft was co-edited by Theresa O'Connor from Apple and Sam Goto from Google.
First proposed by Apple WebKit engineers and backed by Google in January, the initiative seeks to simplify the OTP SMS mechanism commonly used by websites, businesses and other entities to confirm login credentials as part of two-step authentication systems.
While many websites and online services use OTP over SMS, a standardized method of formatting incoming messages text does not exist. As such, "programmatic extraction of codes from [SMS messages] has to rely on heuristics, which are often unreliable and error-prone. Additionally, without a mechanism for associating such codes with specific websites, users might be tricked into providing the code to malicious sites," the WICG publication notes.
Currently, users must manually input provided passcodes into a text field on a host website. Apple wants to push the status quo with a more refined solution that would also provide a higher degree of security.
Using a "lightweight text format," the proposed format embeds an actionable one-time code in an SMS message and links that code to an originating URL. The recipient system can then extract the code and log in to an associated website automatically.
An example OTP SMS:
747723 is your [website] authentication code.@website.com #747723
ZDNet reported on the WICG development on Tuesday.
"This proposal attempts to reduce some of the risks associated with SMS delivery of one-time codes," the explainer reads. "It does not attempt to reduce or solve all of them. For instance, it doesn't solve the SMS delivery hijacking risk, but it does attempt to reduce the phishing risk."
Publication as a WICG specification draft does not necessarily mean Apple's protocol will see mass deployment, but it does show the project is moving forward.
 Mikey Campbell
Mikey Campbell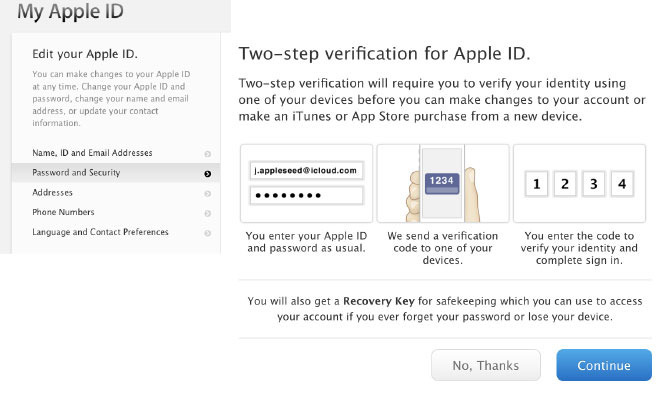

-m.jpg)






 Andrew O'Hara
Andrew O'Hara
 Malcolm Owen
Malcolm Owen
 Marko Zivkovic
Marko Zivkovic

 Chip Loder
Chip Loder
 Christine McKee
Christine McKee
 William Gallagher
William Gallagher
 Amber Neely
Amber Neely



-m.jpg)





24 Comments
I’ll use it when required, but I worry
Making
How much better is this 2FA over nothing at all? Probably a little because it means the bad actors need to do more work to access your accounts, but SMS isn't secure. I'd much rather see Apple include an authenticator app option for iCloud and in their iCloud Keychain, and then push authenticator apps as the best option for everyone.
Here's something I don't understand. Why does Apple's 2FA send a login notice and code to the same device you're trying to log into something with (ie your iCloud or Apple Support account etc). Doesn't that defeat the purpose, even if it is a "trusted device"?