Apple's WebKit engineers are working on a standardized format for SMS messages containing one-time passcodes, an initiative that could one day better protect users by streamlining two-step authentication logins.
Posted to GitHub on Thursday, the proposal from Apple seeks to simplify the OTP SMS mechanism commonly used by websites, businesses and other entities to confirm login credentials as part of two-step authentication systems, reports ZDNet.
Two-step solutions require a user's password and another element, in this case a one-time code sent over SMS, to gain access to a target account. Currently, it is difficult to impossible for software to automatically extract the necessary information from an OTP SMS message, as they can arrive in a range of text formats. This means users must manually enter the provided code into an input box.
Apple's proposal seeks to eliminate user intervention in the OTP SMS process, namely copy-and-pasting one-time codes from messages into a browser. It also states that a more refined solution would ensure that one-time codes sent over SMS are used only on originating sites.
Using a "lightweight text format," the proposed format embeds an actionable one-time code in an SMS message and links that code to a particular originating URL. Doing so allows recipient systems to automatically extract the code and log in to an associated website.
Apple provides an example SMS:
747723 is your [website] authentication code.@website.com #747723
The first line in the message above is optional human-readable text to explain the incoming message, while the second line contains information for programmatic use. Special characters are employed to denote the one-time code and originating URL, which in this case is "747723" and "website.com," respectively.
Apple and Google have signed on to the proposal, while Mozilla has not made an official statement on the standard, the report said.
For its part, Apple has moved its products from two-step verification to more secure two-factor authentication methods that rely on passcodes sent to pre-enrolled trusted devices.
 AppleInsider Staff
AppleInsider Staff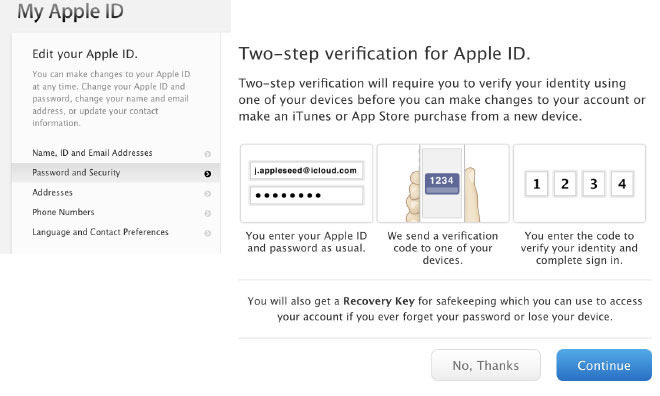








 Marko Zivkovic
Marko Zivkovic

 Malcolm Owen
Malcolm Owen

 Amber Neely
Amber Neely

 Wesley Hilliard
Wesley Hilliard










29 Comments
Bring it on! While they're at it, I wish that websites had a simple, robots.txt-like file that would detail the password parameters so that when using a password manager to create complex, random passwords, it could look at that file to know what characters and other rules are allowed (or disallowed) before generating a unique password.
That is a really excellent idea…
I'm not so sure about Apple re-enforcing SMS as a multi-factor standard, though. SIM-jacking is real, the security standards of AT&T Verizon and Tmobile are laughable.
One of my favorite newer features in iOS/macOS is the ability to auto-populate OTP codes sent via SMS in apps and Safari without having to even look at Messages. This seems like an extension of that by way of more security and standardization?
Yes
Yes
Oh god
Yes
I thought the point of two factor authentication is that even if a bad actor gets your login credentials, he won't be able to get into your account using his own computer if he doesn't have access to your phone. I've never really seen the point of using TFA when the website or app being protected is accessed on the same device that receives the access code.