Cybersecurity firm Volexity on Tuesday said it discovered a new iOS exploit that was recently used to surveil the Uyghur Muslim minority in China.
In July 2019, Apple patched a handful of security vulnerabilities in its mobile operating system with the iOS 12.4 update, including several flaws in WebKit. But researchers at Volexity said that at least one of those flaws was actively exploited in the wild in 2020.
The exploit, which Volexity has dubbed "Insomnia," was loaded onto user devices after they visited websites themed around China's Uyghur minority. Attackers then used the exploit, which granted them root access to user devices, to steal plaintext messages from various messaging clients, emails, photos, contact lists and GPS location data.
Reportedly, the Insomnia exploit was used in the wild between January and March 2020.
Volexity said the exploit was deployed by a hacking group they've called Evil Eye, which they believe to be a state-sponsored outfit operating on behalf of China to spy on the Uyghur minority.
The hacking group is also believed to be the threat actor behind a similar slate of iOS surveillance exploits discovered by Google and Volexity in August 2019. Those exploits were used to spy on Uyghurs in China since at least 2016.
Compared to the previous exploits, Insomnia was expanded to target and include end-to-end encrypted communications from apps like ProtonMail and Signal. Researchers think that suggests Uyghurs were aware of surveillance taking place and were taking steps to protect their communications.
Since Insomnia is a WebKit-based exploit, it works on any browser running on an iOS device. Researchers confirmed that Safari, Chrome and Microsoft Edge browsers were vulnerable, meaning any iOS user who visited the Uyghur-themed websites could become infected.
The WebKit vulnerability was present in iOS 12.3, iOS 12.3.1 and iOS 12.3.2, but iOS 12.4 and newer versions are safe. It's worth noting that Insomnia did not achieve persistence on a device, which means that a simple reboot is enough to remove its malicious code.
 Mike Peterson
Mike Peterson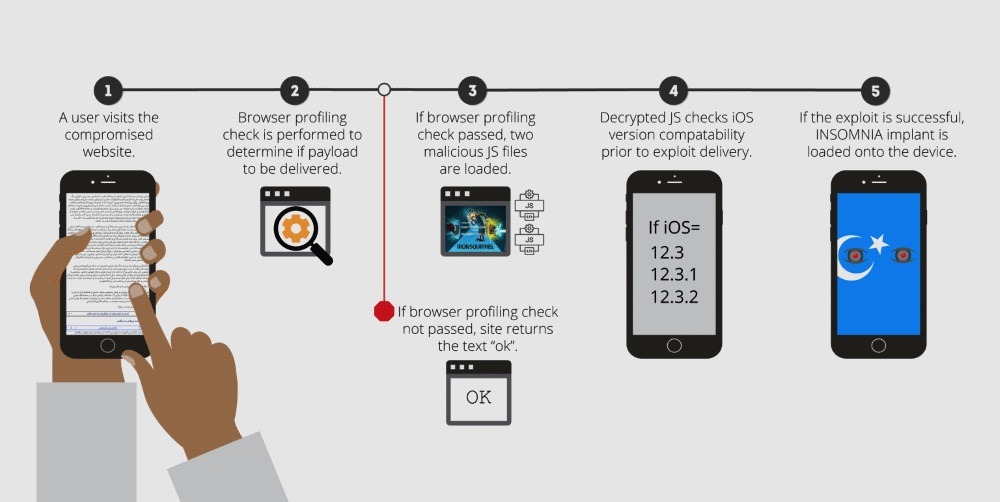




-xl-m.jpg)


-m.jpg)






 Mike Wuerthele
Mike Wuerthele
 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher
 Thomas Sibilly
Thomas Sibilly
 Wesley Hilliard
Wesley Hilliard
 Marko Zivkovic
Marko Zivkovic







13 Comments
Needs someone to proof this article.
So the U.S. government doesn’t really need a backdoor then.
Odd if the iOS exploit was only used this year (or maybe only noticed?) when iOS was patched in July 2019. They wouldn't have had many vulnerable devices to exploit.
Although, since they really only need to be able to crack one end of the communication there is a multiplier effect.
Russia/USSR threatens the western world. China threatens their own people.