Apple's Private Relay feature appears to have a flaw that can cause a system to ignore firewall rules and leak that a system is communicating with Apple servers, a new report claims.
According to VPN service Mullvad, Private Relay calls home to Apple servers without respecting a system's firewall rules. That causes a leak that isn't able to be mitigated without disabling Private Relay entirely.
More specifically, Mullvad detected QUIC traffic leaving a computer outside of the Private Relay VPN tunnel. Disabling the feature worked, indicating that Apple's VPN system is a trigger for the leak — even if it's not the source of the traffic.
"We believe they are just some heartbeat signal calling home to Apple," Mullvad wrote. "We do not know what information is transmitted to Apple, but since the destination is Apple servers, it is a strong signal to your local network and ISP that you might be a macOS user."
The VPN service points out that Private Relay mostly disables itself when any firewall rule is added to Apple's system firewall on macOS.
Private Relay, which is only available to iCloud+ members, works similarly to a VPN tunnel or a privacy system like Tor. It routes user network traffic in an encrypted format through relay servers before it reaches the internet.
Since the Private Relay feature is in beta, there's a chance that Apple could mitigate the leak before it launches in a final version. Until then, the only way to stop the leak is to disable the feature entirely.
 Mike Peterson
Mike Peterson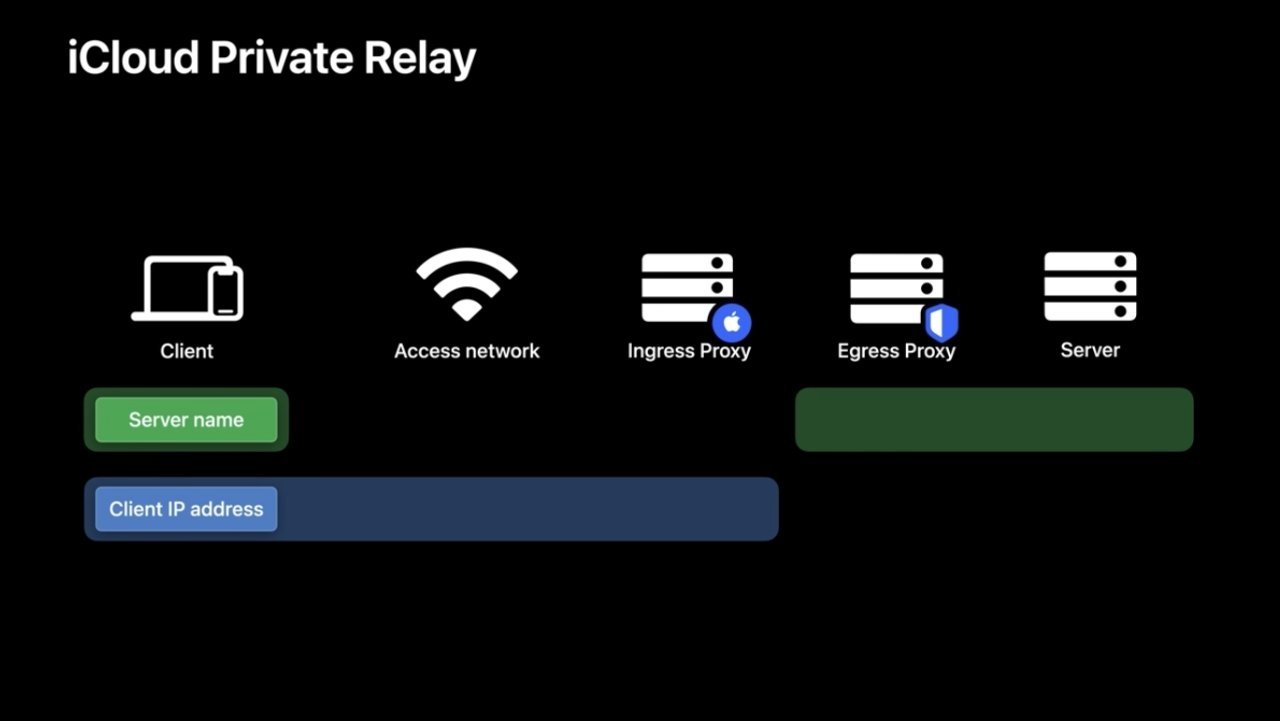








 Christine McKee
Christine McKee
 Charles Martin
Charles Martin
 Mike Wuerthele
Mike Wuerthele
 Marko Zivkovic
Marko Zivkovic
 Malcolm Owen
Malcolm Owen


 William Gallagher
William Gallagher


-m.jpg)






4 Comments
Interesting - just got a popup on my iPhone telling me PR wasn't compatible with my eero network. Had been running fine for weeks.
I suspect the use of Apple's relay servers would be just as strong an indication of Apple device usage as this data "leak" is. Likely just much ado about nothing.