Apple has announced a series of three powerful new tools to protect users' most sensitive data, in new iCloud and iMessage features that will be rolling out between now and the end of 2023.
As far back as 2015, Apple was stepping up security with two-factor authentication on the App Store. For 2023, it's implementing a trio of further security options for all users.
"Apple makes the most secure mobile devices on the market," Ivan Krstic, Apple's head of Security Engineering and Architecture, said in a statement. "And now, we are building on that powerful foundation."
"Advanced Data Protection is Apple's highest level of cloud data security," continued Krstic, "giving users the choice to protect the vast majority of their most sensitive iCloud data with end-to-end encryption so that it can only be decrypted on their trusted devices."
Apple's three new or expanded data protections are:
- iMessage Contact Key Verification (coming 2023)
- Security Keys for Apple ID (coming early 2023)
- Advanced Data Protection for iCloud (in beta now, US by end of 2022, globally in 2023)
"At Apple, we are unwavering in our commitment to provide our users with the best data security in the world," said Craig Federighi, Apple's senior vice president of Software Engineering. "We constantly identify and mitigate emerging threats to their personal data on device and in the cloud."
"Our security teams work tirelessly to keep users' data safe," he continued, "and with iMessage Contact Key Verification, Security Keys, and Advanced Data Protection for iCloud, users will have three powerful new tools to further protect their most sensitive data and communications."
iMessage Contact Key Verification
With the optional iMessage Contact Key Verification, users who enable it will get alerted, says Apple, "if an exceptionally advanced adversary, such as a state-sponsored attacker, were ever to succeed breaching cloud servers and inserting their own device to eavesdrop on these encrypted communications."
The same feature also allows users to compare what Apple calls a Contact Verification Code, "in person, on FaceTime, or through another secure call."
Security Keys for Apple ID
This takes Apple's existing two-factor authentication and strengthens it. by require one of those two factors, to be a hardware security key. Users will have the option to use this, and if they choose to, will then also get a choice of third-party hardware security keys.
"This feature is designed for users who, often due to their public profile, face concerted threats to their online accounts, such as celebrities, journalists, and members of government," says Apple.
Advanced Data Protection for iCloud
Multiple categories of iCloud data, such as passwords in iCloud Keychain and health information, are already protected using end-to-end encryption. Once the new feature is available, users can choose to encrypt a further 9 categories.
Those new categories include iCloud Backup, Notes and Photos. Apple notes that only iCloud Mail, Contacts, and Calendar remain without end to end encryption, and says it's because of "the need to interoperate with the global email, contacts, and calendar systems."
Why Apple is adding extra security now
The Wall Street Journal's Joanna Stern asked Federighi why Apple has chosen now to do this, when security experts have been calling for it for years. He replied that Apple has been consistently working on the issue.
"Some of the steps we took over a decade ago and designing iCloud and the way we encrypted were necessary precursors to build toward this moment," he said, "and using end to encryption for the other types of data like passwords and browser history and so forth, help [improve] that technology."
 William Gallagher
William Gallagher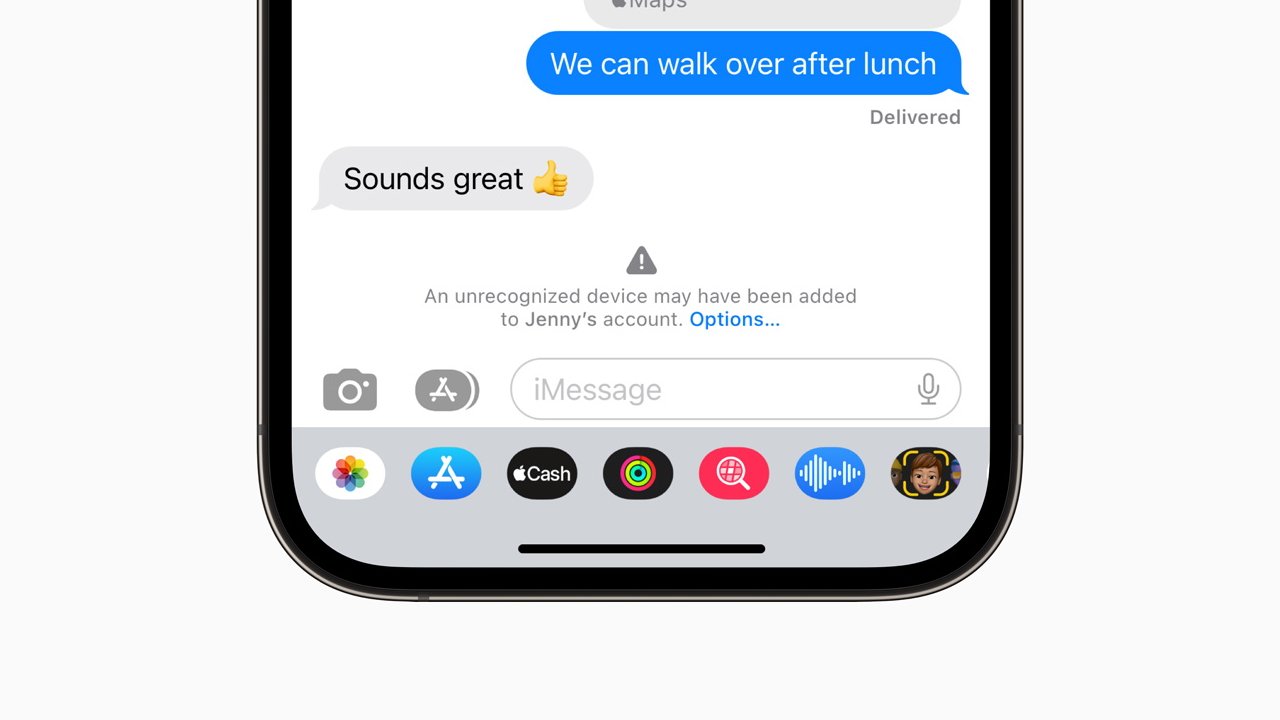








-m.jpg)






 Christine McKee
Christine McKee
 Marko Zivkovic
Marko Zivkovic
 Mike Wuerthele
Mike Wuerthele

 Amber Neely
Amber Neely
 Sponsored Content
Sponsored Content
 Wesley Hilliard
Wesley Hilliard










11 Comments
Bravo, Apple.
Bravo, Tim.
A fuller explanation of this would be helpful, and if there is a complete and clear opt out option...
Does S/MIME fit in to this...? Core ML derivative data and the Siri 'learn from this app' that is on by default ?
Does Apple also have a key to every iCloud account...?
Third-party hardware security keys—it’s about time. I used RSA token hardware 29-30 years ago. I would live an Apple “copy” of RSA’s rotating keys using an iOS app connecting to an Apple server.