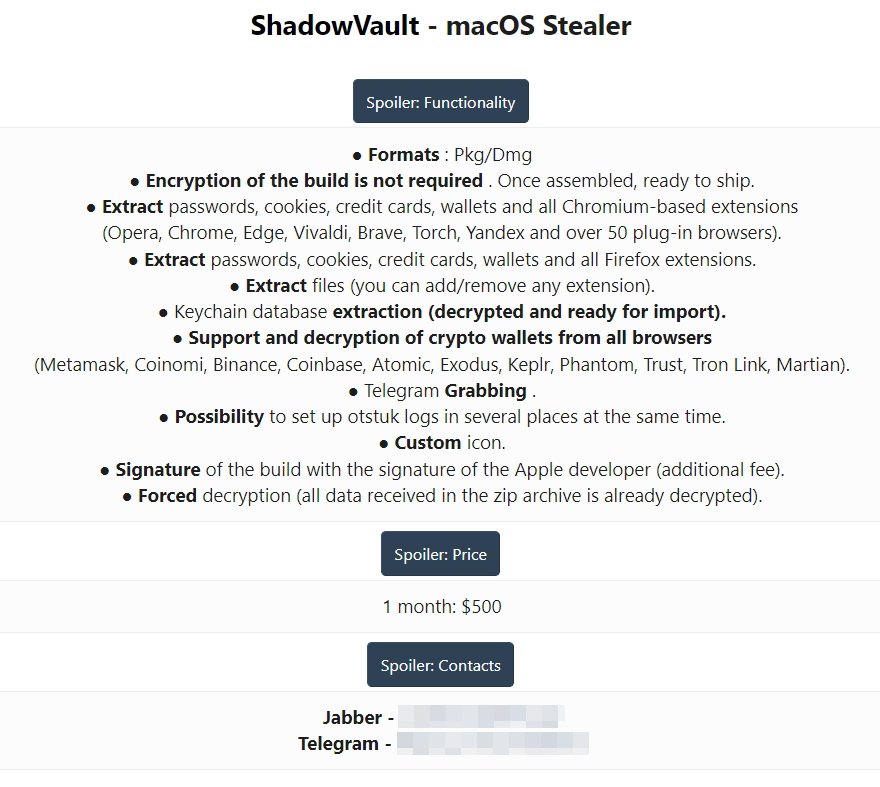
A newly-spotted security threat called ShadowVault works in the background on macOS to access logins, banking details, and more personal data.
Macs have traditionally been less targeted by malware developers in part because of the security in macOS, and partly because it's presented a smaller target than Windows. It's still the case that Macs have fewer malware issues than PCs, but also it's being targeted by different types of security threats.
Now according to Guardz Cyber Intelligence Research (CIR), a new specific threat to macOS has been uncovered. CIR claims to have used "sophisticated covert operations" in order to identify ShadowVault while it was still being developed.
It's not clear whether ShadowVault has been seen in active use, nor how it is intended to be delivered once in the wild. Since it runs in the background on Macs, though, users presumably have to be tricked into downloading and running it.
When discovered, ShadowVault was being offered for sale for $500 for one month. It claims to be able to extract "passwords, cookies, credit cards, wallets," and "all Chromium-based extensions."
How to protect yourself from ShadowVault
AppleInsider has a thorough guide to protecting Macs against malware, phishing and more. In short, users can prevent security threats by being wary of anything unexpected — and not following links or opening files unless certain they are genuine.
Many phishing attempts will be easily recognizable, but if in doubt, users should look for issues such as company names being spelt correctly in emails. Typing mistakes still seem to convince junk filters that the mail is from a real human being, but companies do not misspell their names.
They also don't include links to anywhere suspicious. While users should never click on a suspicious link, they can hover the mouse cursor over the link and see where it would really take them.
CIR says ShadowVault was specifically built to steal data from macOS devices. Describing it has having "potent capabilities," CIR also claims to have developed countermeasures for its clients.
Apple has not commented on ShadowVault.
 William Gallagher
William Gallagher







-m.jpg)





 Charles Martin
Charles Martin
 Marko Zivkovic
Marko Zivkovic
 Andrew Orr
Andrew Orr
 Amber Neely
Amber Neely

 William Gallagher and Mike Wuerthele
William Gallagher and Mike Wuerthele










6 Comments
How do you steal a Blockchain wallet remotely - you need the eleven random passwords made randomly and the passcode you create - as for a physical wallet like Ledger it only has 250 bites so no possible physical room for malware. Plus the random words and so on... Blockchain is unhackable. I once read the odds are one trillion to the exponent one million.