Apple's operating system updates on Thursday patched an exploit chain capable of compromising iOS 16.6 devices with the Pegasus spyware without any interaction from the victim.
The exploit was discovered on an iPhone owned by an individual employed by a Washington DC-based civil society organization. The exploit was used to deliver NSO Group's Pegasus mercenary spyware.
Toronto's Citizen Lab states that the exploit involves PassKit containing "malicious images sent from an attacker iMessage account to the victim."
Citizen Lab disclosed their findings to Apple, who promptly issued CVE-2023-41064 and CVE-2023-41061 related to the exploit chain. The iOS 16.6.1 patch fixes the security gap, and Thursday's report from Citizen Lab confirms that.
Both Citizen Lab and AppleInsider recommend that iPhone owners update their devices as soon as feasible. Users can download the security fix by opening the Settings app, tapping Software Update, and installing iOS 16.6.1 from the menu.
The security researchers will publish a more detailed discussion of the exploit chain in the future.
 Amber Neely
Amber Neely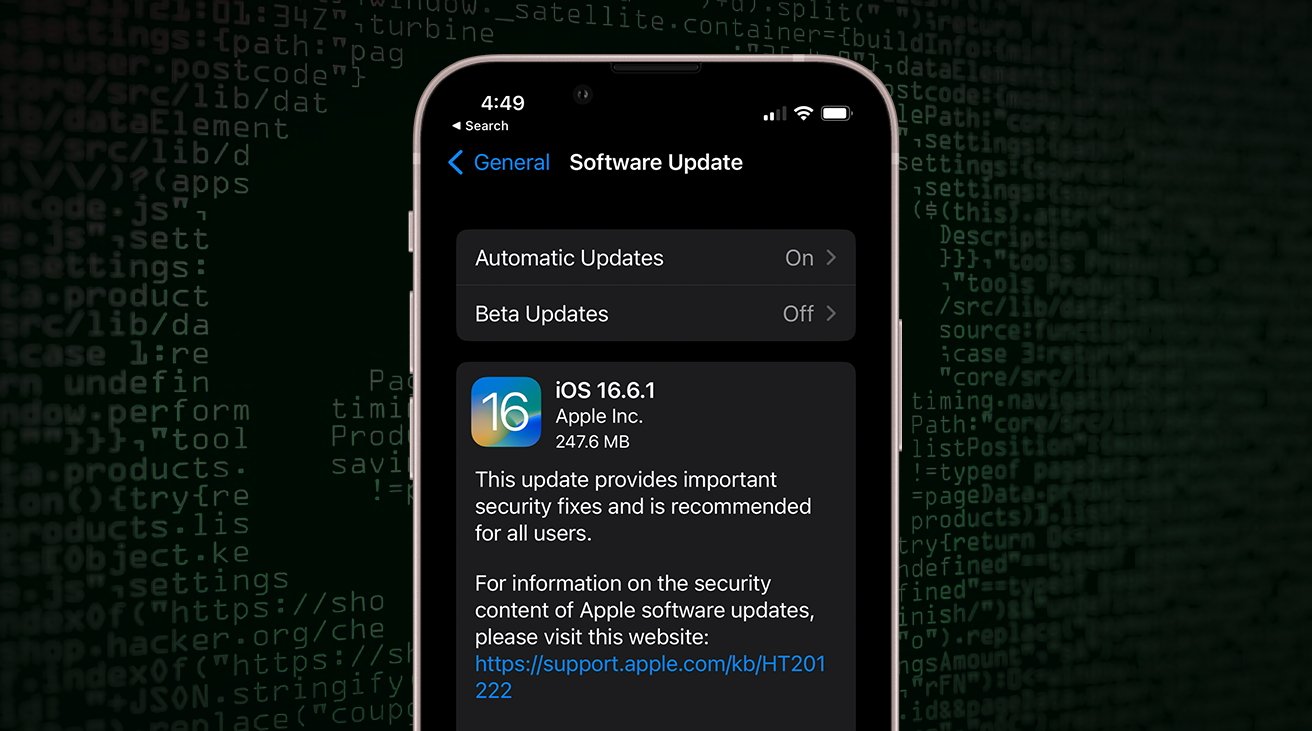








 Christine McKee
Christine McKee
 Charles Martin
Charles Martin
 Mike Wuerthele
Mike Wuerthele
 Marko Zivkovic
Marko Zivkovic
 Malcolm Owen
Malcolm Owen


 William Gallagher
William Gallagher

-m.jpg)






4 Comments
So much for the so-called “
I wondered about that, too.
Evidently the same problem was found/fixed on the MacOS side.
I have often wondered if security patches like this eliminate the problem if you already got infected, or if the patch just prevents you from being infected going forward.