Within a day after the release of the Apple Vision Pro, a security researcher claims to have created a kernel exploit for visionOS, opening the way towards a potential jailbreak and malware creation.
The first releases of new hardware is often accompanied by a gold rush of security researchers and malware developers working to break the operating system. Just as jailbreak makers try to break iOS, people are already causing security problems for the Apple Vision Pro.
In a late Friday tweet by MIT Microarchitectural Security PHD student Joseph Ravichandran, it is claimed that a kernel exploit has been made for the Apple Vision Pro, potentially the first ever publicly discovered.
The world's first(?) kernel exploit for Vision Pro- on launch day! pic.twitter.com/9rVtaSmbei
— Joseph Ravichandran (@0xjprx) February 3, 2024
The tweets, spotted by iDevice Central, detail in a few photographs how the Apple Vision Pro reacts to the attempted kernel exploit. After being introduced, the Apple Vision Pro goes to a full passthrough view, before warning the user to remove the headset as it will restart within 30 seconds.
After the restart, another image shows a panic log for the headset, showing that the kernel had crashed.
Ravichandran also posted another image for the "Vision Pro Crasher" application, complete with a headset-wearing skull image and a button to "Crash My Vision Pro."
It is unclear if the researcher has submitted the findings to Apple, or if they intend to at all. If they do, there's a small chance that it could qualify under the Apple Security Bounty program.
Given Apple's tendency to work fast on security issues, as well as the high-profile nature of the Apple Vision Pro launch, it is likely that Apple will issue an update fixing the problem if the issue is disclosed.
At this extremely early stage, considering the slow roll-out of devices to a generally tech-literate early adopters, it seems unlikely that the discovery will cause issues for Apple and its users.
 Malcolm Owen
Malcolm Owen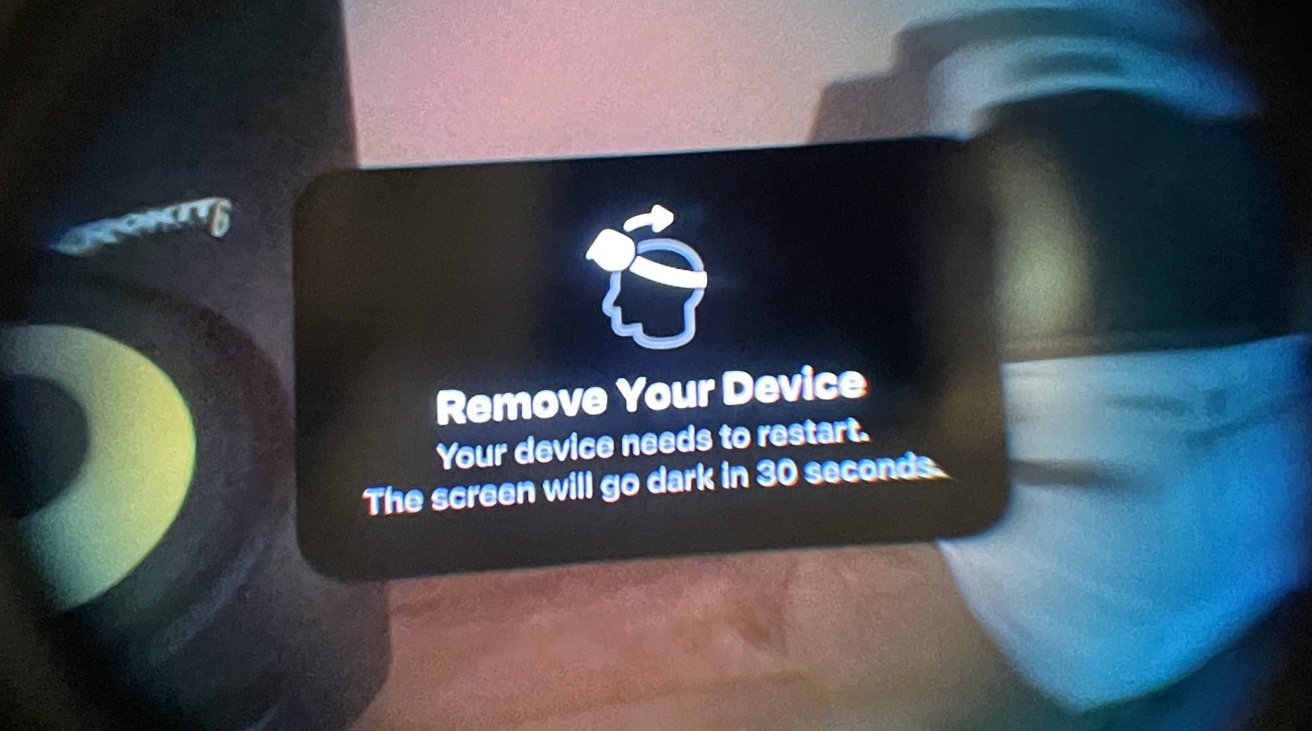

-m.jpg)






 Andrew Orr
Andrew Orr

 Amber Neely
Amber Neely

 Wesley Hilliard
Wesley Hilliard
 William Gallagher
William Gallagher











7 Comments
Looking at the panic log picture it appears to show this Vision Pro running 1.0 not the current 1.0.2 version of visionOS.
A developer is able to crash the Vision Pro?! :D <eye roll> This is not news. When someone is able to remotely exploit one it will be interesting.
Just imagine
a jailbroken vision pro with a pornhub app :)