A new type of Mac malware is masquerading as CleanMyMac or Photoshop cracks, and has been stealing data from browsers and pilfering cryptocurrency wallets. Here's how to stay safe.
According to MacPaw's Moonlock Lab, the malware often presents itself as legitimate apps. Once installed, it can use AppleScript to trick users into revealing their passwords, steal cookies from browsers like Chrome and Safari, and self-destruct if it detects that it is running on a virtual machine.
The script starts by getting the current username from the system along with other essential system paths for later use. Then, it creates a temporary folder to store the stolen data before sending it out.
Web browsers like Chrome and Safari can also be harvested for sensitive user information like browsing history, cookies, and saved passwords. Another function of the script is its ability to find and access popular cryptocurrency wallets. It can steal wallet files, potentially giving the attacker access to the victim's crypto assets.
The wallets it targets include Electrum, Coinomi, Exodus, Atomic Wallet, Wasabi Wallet, Ledger Live, Feather (Monero), Bitcoin Core, Litecoin Core, Dash Core, Electrum-LTC, Electron Cash, Guarda Wallet, Dogecoin Core, Binance, and TonKeeper.
The script then copies the "login.keychain-db" file, which holds macOS keychain data like passwords and sensitive credentials. It also takes data from Apple Notes by copying the "NoteStore.sqlite" and related files.
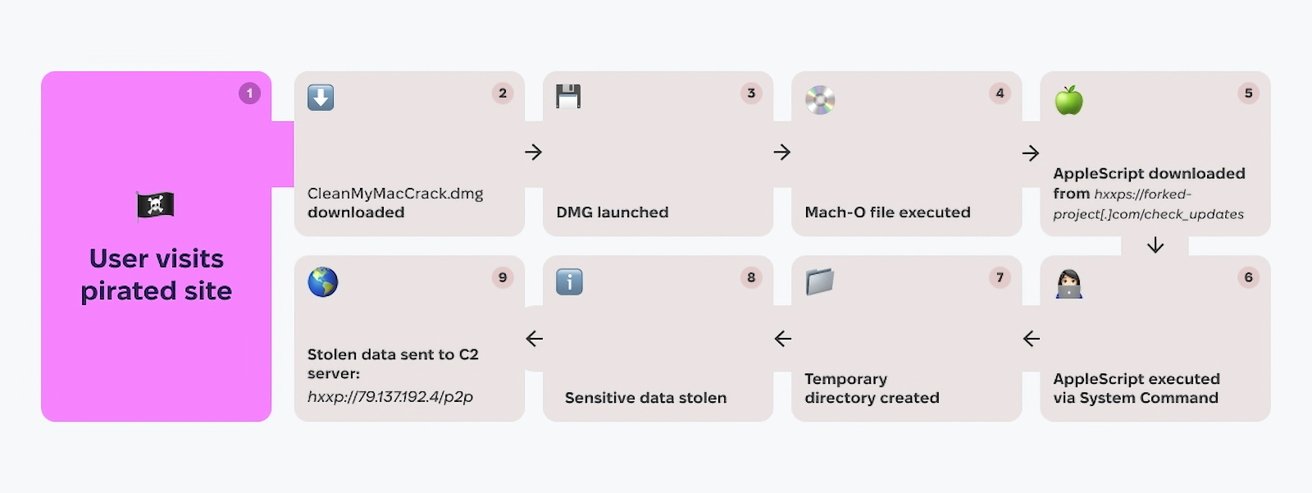 The infection chain starts when a user visits a site offering pirated software and downloads a file called CleanMyMacCrack.dmg
The infection chain starts when a user visits a site offering pirated software and downloads a file called CleanMyMacCrack.dmgThe malware is actually a variant of "Atomic Stealer." Initially identified in 2023, Atomic Stealer has evolved to become more challenging to detect.
It hides in illegitimate software downloads, gets into macOS through user error, and stays hidden using scripts while it steals sensitive data.
How Mac users can protect themselves from Atomic Stealer
Given these threats' advances, Mac users must take proactive steps to stay safe. Always download software from the official website or the Mac App Store and avoid third-party sites that might offer cracked or pirated versions.
Check the URL for any signs of irregularities, such as misspellings or unusual characters, and make sure the site is legitimate before downloading anything. Regularly updating macOS and all installed applications can protect against known vulnerabilities.
Gatekeeper — a built-in feature of macOS — ensures that only signed and trusted apps can be installed. Finally, avoid clicking on suspicious links or downloading attachments from unknown sources, as cybercriminals often use phishing tactics to spread malware.
 Andrew Orr
Andrew Orr







 Charles Martin
Charles Martin
 Wesley Hilliard
Wesley Hilliard


 Oliver Haslam
Oliver Haslam
 Marko Zivkovic
Marko Zivkovic
 Amber Neely
Amber Neely








1 Comment