Malware is bad software you don't want to encounter, as it can harm your Mac or cause data loss. Here's how to protect against it.
With security being an ever-increasing concern in the connected age, malicious attacks by bad actors continue to be a problem for many organizations and users.
Malignant software (malware) can be planted on your devices, which can lead to credential or data loss, corruption of operating systems, or ransomware.
As billions of digital devices proliferate worldwide and more commerce moves online, malware has become an ever-increasing threat.
Software security models
In the early days of software - before the internet became mainstream, most systems were open and software could be installed from anywhere. Usually it was from CD-ROM or floppy disk.
With online software stores now the standard, this is a little less of an issue. This is because app storefronts check most software before it is released to ensure security.
Nonetheless, bad software can and does sometimes slip through.
Apple tried to solve this problem with the introduction of curated stores, such as the iOS App Store. But even there, some bad software has occasionally been released.
Curated stores are more secure and reliable, but they're still not foolproof.
The Mac is slightly different, because in its early days, it too could accept software from any source. Classic apps such as Virex and Norton Utilities helped "clean" Macs of malware.
The Mac App Store today features curation, app receipt validation, and app notarization. But the Mac still allows software installation from anywhere, if certain settings are turned off.
Code Signing, Developer ID, and Gatekeeper
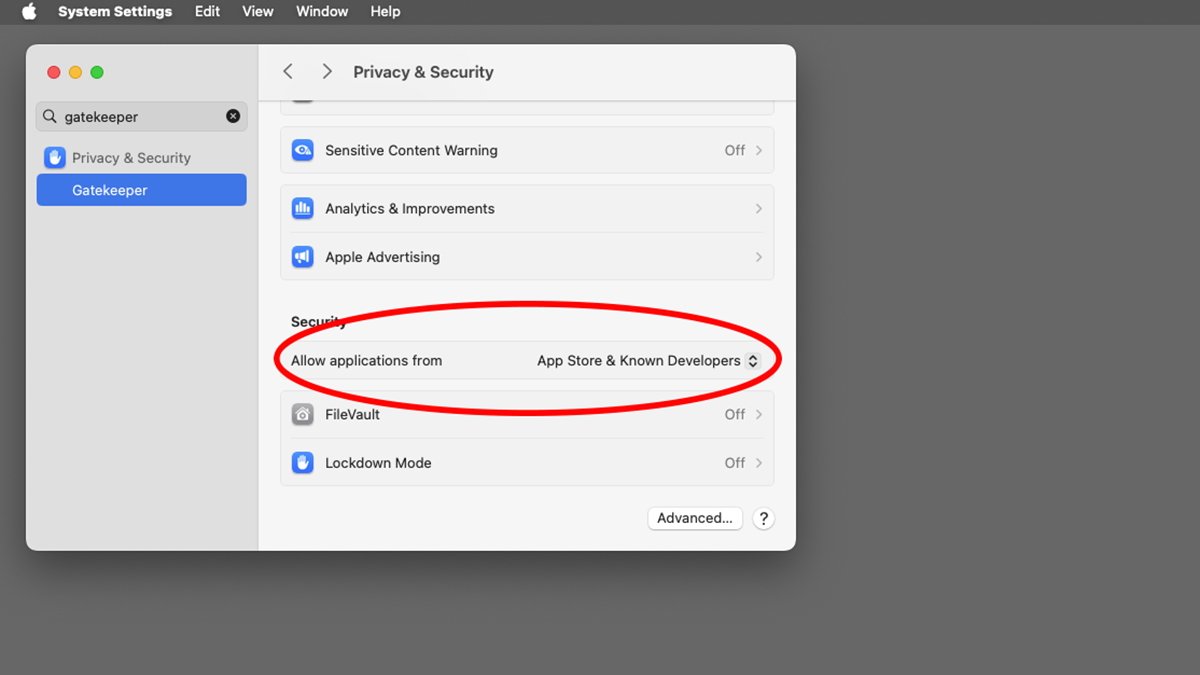
Years ago, Apple introduced an additional security measure for macOS software: Gatekeeper. Along with Developer ID, Gatekeeper by default ensures that downloaded Mac software is secure.
With Gatekeeper, macOS developers register with and are issued a Developer ID by Apple, which is then used to digitally sign Mac software they create.
If Gatekeeper is turned on in macOS, it ensures apps are signed by the developers who make them. It also warns on a Mac app's first-run for apps that aren't from known, registered developers.
Mac users can choose in System Settings->Privacy & Security->Allow Applications from which apps they want to allow installation for: either App Store-only apps or App Store & Known Developers.
Code Signing Services and app Notarization ensure the software is valid and not hacked or malicious when users download it.
System Integrity Protection (SIP)
macOS offers one other system security feature that helps keep Mac secure: System Integrity Protection or SIP.
SIP restricts which apps can be allowed to run and what code can be run on Macs. By default, only App Store apps or software from registered Apple developers can run.
It also restricts system files from being tampered with or modified without authorization.
It is possible to turn off SIP in the Terminal, but it's not recommended. Doing so defeats the security of macOS and may allow malicious code to run on Macs.
The csrutil command-line tool can be used to inspect and change SIP parameters.
To get the current status of SIP on your Mac in Terminal type:
csrutil status and press Return.
Privileges, escalation, sockets, and helper tools
Most UNIX software uses the concept of privileges and privileged users. The root user, for example, has unlimited security privileges and can make changes to software at will.
For security reasons, the root user is disabled by default in macOS. Other users may have other varying levels of privileges, which allow certain actions including software installation or removal.
admin users have elevated privileges, and an admin password is required for many operations in macOS.
By using temporary privilege escalation, macOS users can be granted additional rights for a short period of time.
Well-designed software should be factored so that security-critical code runs in a separate process called a helper tool. Helper tools ensure that only small parts of code can be run with elevated privileges - thus restricting which parts of software can perform critical tasks that can endanger the system's security.
An app with good factoring will put all at-risk code into a helper tool, then when permissions are needed run the helper tool after the user has been authorized. This increases security and also means compromised apps can't run all code at elevated privileges - which is a security risk.
The idea is to run the helper tool and elevate privileges for the least amount of time, perform privileged operations, and then drop privileges back to their previous level when the helper tool exits.
UNIX domain sockets and pipelines can also be used to securely pass information between processes.
Security daemons and frameworks
macOS is one of the most secure operating systems in the world, but it's not foolproof.
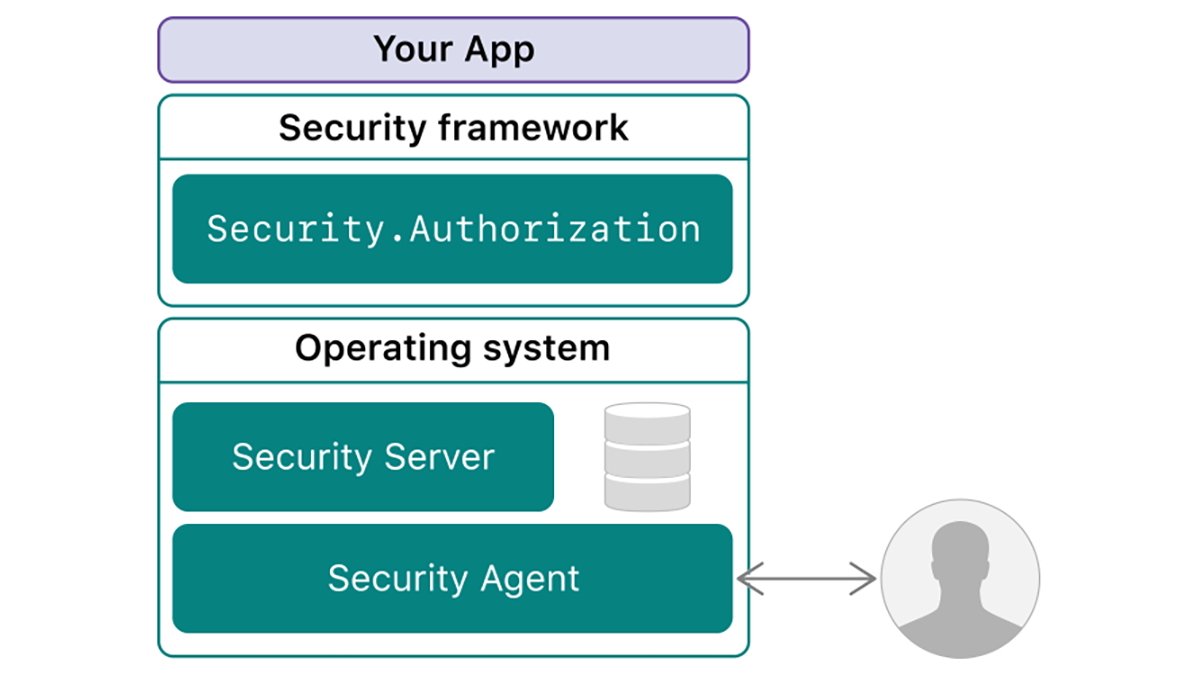
Security in macOS is managed with a combination of background processes (daemons), and Apple code frameworks loaded into apps when they are run. These include:
- launchd
- secured (the security server)
- XPC Services
- Authorization Services.framework
- Security.framework
- System Configuration.framework
- Service Management.framework
- Endpoint Security.framework
- Cryptographic Services
- Code Signing Services
- Keychain Services
- Hardened Runtime
Dynamic linking ensures frameworks are only loaded into memory when their APIs or interfaces are actually used.
The above software components provide the following services:
launchd (the Launch Daemon) is a system-wide daemon that runs in the background and manages the launching and termination of apps and other processes in macOS.
secured (the Security Daemon) manages secure access, elevating privileges, running tools and certain user IDs, and other security services.
XPC Services manages secure interprocess communication between software components as well as working with launchd to run helper tools securely.
Authorization Services.framework manages prompting users for an admin password, caching privilege escalation, and maintaining timers which lower privileges after a given timeout. When your Mac prompts you for an admin password to install software or change a setting, it sends a message to secured to display the admin password dialog box so the user can enter a name and password.
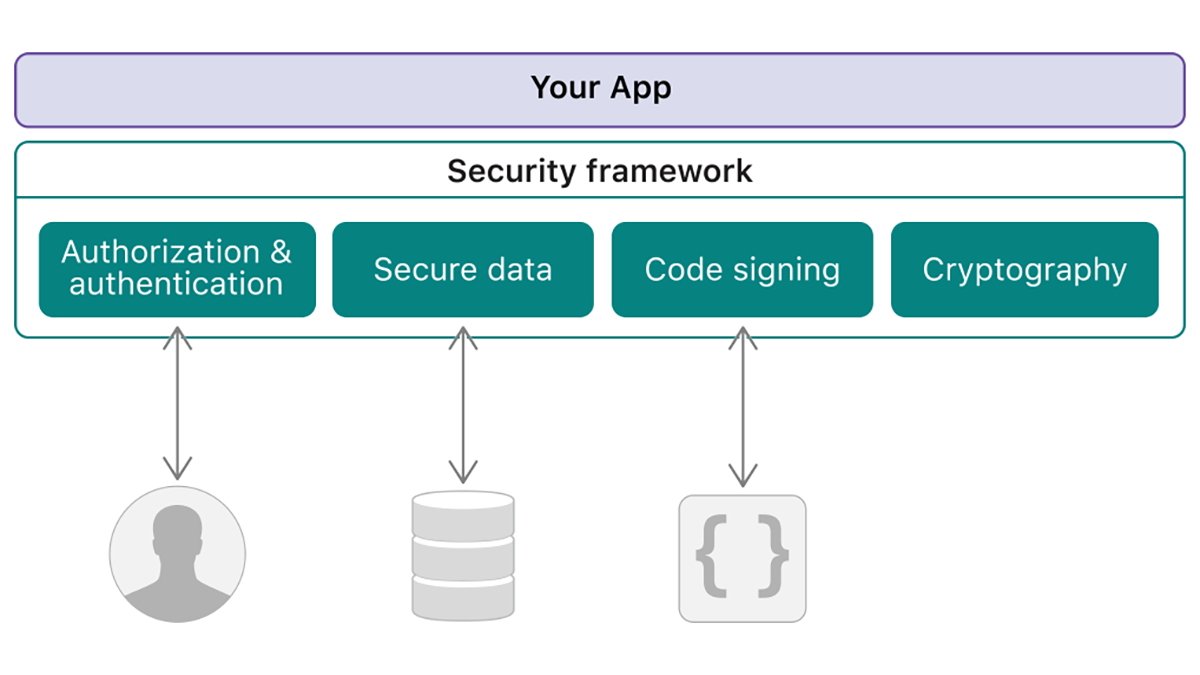
Security.framework manages user identity (authentication) and grants access to resources, secures data on disk and across network connections, and verifies the validity of code before it runs.
System Configuration.framework manages system settings and ensures restricted settings can only be changed if required authorization has been provided.
Service Management.framework allows apps to manage launch agents, launch daemons, and login items.
Endpoint Security.framework allows developers to write their own system extensions which enhance security.
Cryptographic Services provides standard cryptography APIs, manages keys, certificates, and passwords, and generates random numbers and hashes.
Code Signing Services provides services to sign and verify built software to ensure it's valid and hasn't been compromised.
Keychain Services manages system keys, certificates, and identities.
Hardened Runtime (along with SIP) protects macOS from code injection, memory tampering, and dynamic library hijacking. Apple's Xcode IDE includes Hardened Runtime settings including allowing or disallowing Just-In-Time (JIT) code, use of unsigned memory, and dynamic linker (DYLD) environment variables.
Changing environment variables before running malware is one way malicious code can be injected into running apps.
All of these components work together to ensure macOS software can be as secure as possible.
The security concept of Zero Trust means that all privileged software access is restricted unless a privileged user explicitly authorizes some secure action. Zero Trust implies by default that malware can't run without specific authorization.
You can see which daemons are currently running on your Mac in the Activity Monitor utility, or by using the top command in Terminal. To use top type:
top and press Return.
This displays all running processes - including daemons, process IDs (PIDs), runtimes, CPU use, ports, and more.
Malware on Macs
Malware can be defined as malicious software that can breach or infect a computer, network, or device to disable, corrupt, or damage a device, or to steal and transmit unauthorized data across a network.
The Computer Fraud and Abuse Act makes it a federal crime in the US to tamper with, disable, or gain access to a computer or network without specific authorization. It also makes transmitting or intercepting stolen information across a network a crime.
Types of malware include (but aren't limited to) viruses, Trojan horses, malicious apps or frameworks, drivers, and even firmware. Network attacks are also possible by injecting malware into network code, or listening in on network communications.
Ransomware is malware that steals company trade secrets or customer data, then allows bad actors to demand a payment from an organization not to use or release the stolen data.
Viruses are small pieces of code that can be installed and run remotely on a user's local computer and wreak havoc silently.
Viruses can corrupt or modify application code, drivers, files, databases, or system software to perform some malicious activity. This can include erasing/damaging data, or modifying software to perform some malicious act.
Viruses can be silent, undetectable, and tiny - and often go unnoticed until it's too late. Because viruses can be installed almost anywhere, they're hard to stop and even harder to get rid of once they infect a computer or device.
In the past, viruses have even been known to infect the firmware of devices such as storage drives or network routers, rendering them permanently damaged and unusable.
A Trojan horse is generally considered to be an app which, when run harms stored data or other installed software and causes it to perform some malicious activity. One common attack vector of Trojan horses is to silently replace software frameworks or system components with a malicious impostor version, which linked apps then unwittingly run.
Trojan horses make normal apps unaware that when hacked framework APIs are called the impostor will cause damage. Trojan horses often come in the form of standalone apps or installers, or frameworks and linked libraries.
Device drivers, likewise can be installed to run malicious code when a specific device is used. Network malware drivers are especially notorious since they can transmit data at will over a network - which can't be retrieved or "unseen" once sent.
Malicious firmware infects or replaces existing firmware inside external devices, causing them to wreak havoc upon normal operation, or when specific standard commands are sent to a device. Malicious storage device firmware is probably the most common, since it can easily be installed via flash commands in the device - and then cause standard disk I/O commands to trigger data loss or corruption.
Network attacks come in the form of malicious code injected into web pages or database commands, usually by adding additional code at the end of standard commands and data.
Buffer overflow malware for example appends a small amount of malicious code to the end of a URL, web page, script, or network packet - which when received and run on the client computer causes damage.
Buffer overflow attacks are one of the most common web-based attacks. They are hard to detect because most network code and web pages run automatically and outside of most software security models.
Most web browsers now include settings for restricting what kinds of software can be downloaded and run automatically in their windows.
Java applets are particularly well-known for enabling malware downloads.
Other types of network attacks include impostors, man-in-the-middle, credential theft, phishing, email spoofing, and Distributed Denial of Service (DDoS) in which remote computers flood servers with so much data they stop working.
Social engineering attacks are deceptive tactics in which bad actors convince victims they are legitimate in order to gain access to their protected information, or cause them to take some action which might harm them. Social engineers might also try to manipulate victims into unwittingly performing crimes, so that in the event they are caught they can blame someone else.
Social engineering in particular is used in the vast and largely unknown field of industrial espionage (spying).
What you can do
Due to the well-thought-out macOS security model and UNIX privileges, the Mac is a very secure system. Still, breaches can and do happen.
Due to the disabled root user and limited privileges which most Mac software runs under, it's hard for an attacker to trick macOS into running malicious code with elevated privileges. Signed and secure helper tools make these attempts even more difficult - and ensure most malicious software can't hang around long enough to do serious damage.
Under the watchful eyes of secured and launchd, tricking a piece of Mac software into running at full permissions without an admin password is difficult. It's also hard to defeat secured itself since it can only run as a certain OS-controlled user with elevated privileges - and without it other secure software can't be authorized to run.
Apple removes most malicious software from its app store quickly As long as SIP is enabled, software from non-authorized registered Apple developers can't be run without a user warning.
You can also run various "cleaner" apps to scan your Mac and storage devices for malware. But be cautious - even cleaner apps have been disguised as malware in the past!
Periodic virus scans and removing suspect apps from your Mac may help reduce risk. Another good policy is to simply keep the number of apps you install to a minimum, thus narrowing the attack surface.
You might want to install little-used software on a single external drive - and then only plug the drive in when you need to access that software.
Keeping system extensions, scripts, third-party fonts, drivers, and kernel extensions to a minimum is also a good idea - this will also reduce background task overhead.
You might consider setting your web browser's security to its highest level, and turning on blocking of suspected malicious sites by default. This can help reduce the possibility that a network attack from a malicious site can harm your Mac.
Some browsers have settings that block all downloads of web applets to protect against dangerous Trojan horse downloads.
Also, make certain all WiFi passwords and access points on your networks are secure - and don't allow anonymous logins. Some Mac network settings allow you to require an admin password to change the settings.
Be sure to restrict admin users on your Mac - only giving admin permission to users who absolutely need it, and only for the length of time required. By default, most users on your Mac shouldn't have admin access.
You might also want to keep Guest users disabled. Enabling Guest users allows any remote user to connect to your Mac without a password.
Also keep Remote Management, Remote Login, and Remote Application Scripting turned off in System Settings->Sharing unless you absolutely need them.
Gatekeeper and runtime protection
If you download and run a non-App Store piece of Mac software that isn't from an authorized Developer ID, macOS will warn you and ask if you're sure you want to run it. This is accomplished by a part of macOS called Gatekeeper.
If you're certain you want to run the software, you can click Allow in the Finder's alert box, which will allow the software to run. This simple security check gives you an extra chance to verify the software before it blindly runs on the first double-click.
Restricting apps to only App Store apps in System Settings means you can only install and run App Store apps on your Mac. This will prevent all possible third-party apps downloaded outside the App Store from running - but you will be more restricted in your software selection as a result.
For background and historical info on how daemons and agents work on the Mac, see TN2083
Daemons and Agents.
Also, be sure to read the Apple Platform Security Guide and Apple's general Security page.
Apple has taken great pains to design and build macOS to be secure - and in most cases, you won't need to worry about security on your Mac. But keep all of the above in mind as you use your Mac to ensure the chance of being hit by malware is as small as possible.
 Chip Loder
Chip Loder









-m.jpg)







 Marko Zivkovic
Marko Zivkovic
 Malcolm Owen
Malcolm Owen

 William Gallagher
William Gallagher
 Christine McKee
Christine McKee
 Andrew O'Hara
Andrew O'Hara
 Andrew Orr
Andrew Orr




-m.jpg)




4 Comments
I need to update a piece of software which is used by the country government I live in.
Gatekeeper is stopping update.
How do I get past this ?
Ie turn off gatekeeper just for this app alone for 2 minutes while I do update.
Nice article Chip. You mentioned network router hacks. Today a UK ISP directed me to use https://www.samknows.com/technology/agents to check connection speed. This agent seems to be being installed quite widely on routers and smells like a dangerous thing to have lurking on a router.
triggered by accessing a website https://samknows.com/realspeed/ which then weasels its way onto your router to access privileged data, seems like an exploitable way of accessing network traffic.
"admin
I still question this statement. The privileges are