XProtect is Apple's Mac virus detection system which keeps your Mac safe. Here's how the protective macOS feature works.
Viruses and other malware are a constant threat to computers, which web surfers have to work around every time they go online.
A computer virus is a small piece of code that gets silently installed onto your computer. One where it runs or embeds itself into other software and causes havoc.
Malicious software is written by bad actors who intend to damage computers, systems, or other electronic devices. Once a virus gets into the wild, it can rapidly spread across millions of computers - often undetected until its too late.
As a response to viruses and other malware, many software and operating system vendors have developed anti-virus or anti-malware software. These can scan and "clean" a computer of malicious code.
One way anti-virus software does this is to scan for known app signatures, sizes, and code. They're then compared against downloaded databases of known malware.
If a match is found, the bad software can be removed from the computer.
Two early anti-virus software packages dating back decades on the Mac are Norton Anti-virus and Virex. McAfee is another anti-virus app that has been around on the Mac for years and is still available today.
XProtect
Starting in Mac OS X 10.6 Snow Leopard in 2009, Apple added its own anti-virus protection called XProtect.
XProtect runs in the background, analyzing whenever an app is first launched, when an app changes in the filesystem, or when a new downloadable XProtect signatures database becomes available.
These are the Security Responses you'll often see listed in System Settings->General->Software Updates
Some users have reported high CPU usage of the background XProtect service (XProtectService) as seen in the Activity Monitor utility, but personally, we haven't seen it yet.
As XProtect runs silently in the background it watches the filesystem and apps as they are run - checking your Mac for any malware that is listed in the XProtect signatures database. If a match is found, XProtect prompts you to remove the malware from your computer.
By using a silent background monitor to watch for malware, XProtect keeps your Mac safe and free from potentially harmful apps.
Since XProtect is part of macOS, and since its signatures files are hosted and installed by Apple, you don't need to worry about anything - your Mac takes care of everything for you.
The X(Protect) Files
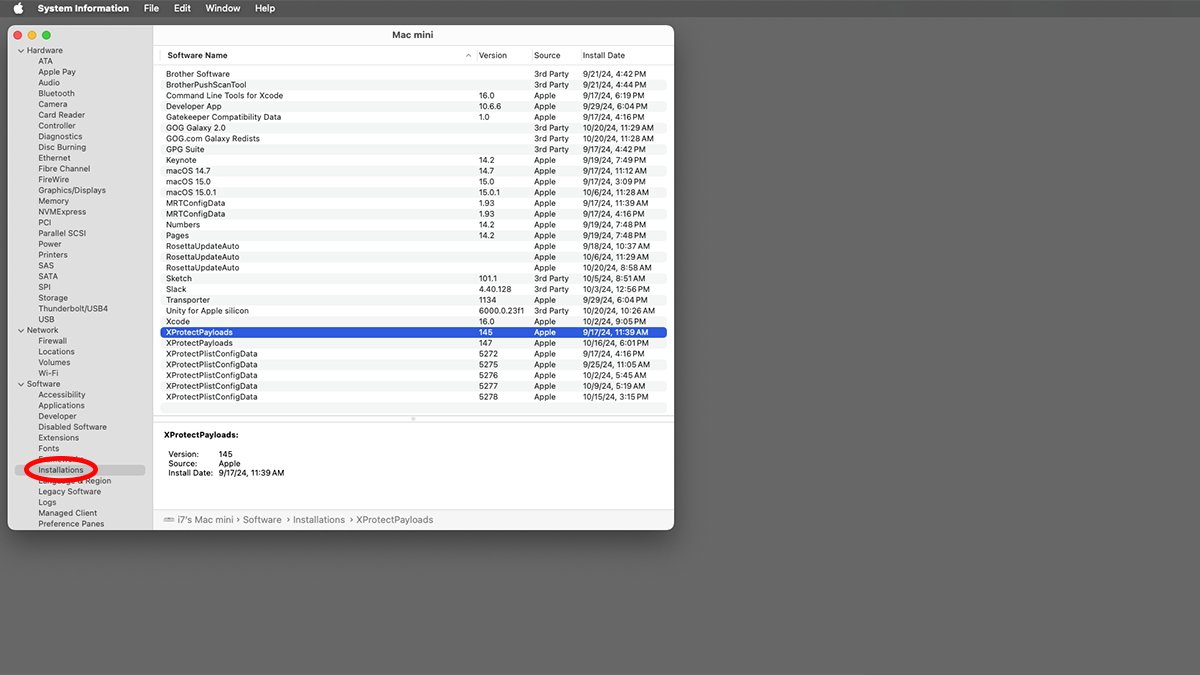
You can view which XProtect signature files have been downloaded to your Mac by holding down the Option key and selecting System Information from the Apple menu in the menu bar.
This runs the System Information app in /Utilities. Scroll to Software->Installations on the left to see XProtectPayloads and XProtectPlistConfigData which show the version and date/time each XProtect signature database was downloaded from Apple.
Notarization and Gatekeeper
When third-party developers build a Mac app they can send it to Apple for Notarization. Apps submitted to Apple in this way are scanned for malware, and Apple makes a signature of known versions of the app to include in the XProtect signatures file.
Apple provides developers with two command-line tools for notarization: altool (obsolete), and the newer notarytool which shipped after Xcode 13. altool no longer ships with macOS 15 Sequoia and Apple has a technote (TN3147) on migrating from the old tool to the new one.
You can get help on using notarytool in macOS's Terminal app by typing:
man notarytool and pressing Return.
Press Control-Z on your keyboard to exit the man page.
Apple also has a page on Customizing the Notarization Workflow in the Developer Documentation.
Notarization works together with Apple's Gatekeeper and Developer ID to ensure Mac apps distributed outside the Mac App Store are authentic and don't contain malware - including viruses.
Once Apple has notarized a third-party app it can be released outside the Mac App Store by developers.
Notarization and Gatekeeper - along with XProtect - are what cause the "Verifying..." dialog box to appear in the Finder the first time you run an app not released via the Mac App Store.
The app scanning process scans the app's bundle (folder) for malicious components and prevents it from running if any are found. It also compares the app's contents against known malware signatures contained in the XProtect signatures database.
This is one reason the "Verifying" process can take so long for larger apps the first time you run them.
When you double-click a notarized Mac app in the macOS Finder, you'll see the "This app is an app downloaded from the internet. Are you sure you want to open it?" dialog. This gives you a chance to back out of running the app if you want to.
If you click OK the Finder launches the app, and if it has been notarized XProtect begins scanning it for malicious components.
Previously it was possible to disable Gatekeeper altogether, but Apple removed this capability in 2016. Non-Gatekeeper third-party Mac software won't run on current versions of macOS if it hasn't been notarized or built with Developer ID without warning you first.
If you get the "Move to Trash" or non-verified warnings in the Finder when launching a Mac app, you'll need to go to System Settings->Privacy & Security. Click the Open Anyway button and enter an admin password for your Mac.
Apple also now requires third-party developers to add the LSQuarantine (com.apple.quarantine) extended filesystem attribute to their app downloads before distributing them on the internet. This attribute triggers Gatekeeper to scan the app before running it.
However, it's still possible for developers to release Mac software on the internet without this attribute added.
Taken together, these security features mean it's much more difficult for malware actors to infect your Mac with bad software.
XProtect runs at least once a day and when user activity on a Mac is low, according to Apple.
YARA Rules
XProtect uses a set of YARA rules from VirusTotal to compare its database to apps on your Mac. YARA uses signature-based detection to locate malware embedded in code.
When XProtect scans apps on your Mac for malware, it uses the YARA rules to check each app for a set of comparisons. These might yield clues pointing to malicious code embedded in apps or in app bundles.
CISA has a somewhat outdated document about using YARA for malware detection. You really don't need to know the internal details for YARA to be useful since Apple handles its use in macOS.
XProtect alerts for malware
If you try to launch an app containing known malware, XProtect will run the XProtect Remediator and will alert you in the Finder that it thinks the app may contain malware. Finder will ask you if you want to move it to the Trash.
If you click Move to Trash, the Finder will move the app into macOS's Trash can but not delete it. You must use the Finder->Empty Trash menu item to actually delete the app from your Mac.
XProtect Remediator tells you in the Finder which malware XProtect found in a particular app when you tried to launch it. You can then decide whether to move it to the Trash or not.
Howard Oakley at Eclectic Light Company has a nice page about what happens when the XProtect Remediator runs.
Oakley also has a note from 2022 about changes Apple made to XProtect - and which malware it scans for, although the list is by no means exhaustive.
For summary info on how XProtect and other macOS security software works, see Apple's Platform Security Guide and Gatekeeper and runtime protection in macOS.
xprotect command-line tool
macOS also includes a command-line interface (CLI) to XProtect called xprotect. You can run this tool in the Terminal with a command to get info about XProtect running on your Mac.
For a list of xprotect commands in Terminal type:
man xprotect and press Return on your keyboard.
Briefly, the commands are:
- update - force download of new XProtect files
- check - print currently available online update version
- version - print currently installed version of XProtect files
- logs - display XProtect logs
- status - print current status of XProtect
- help - print help for a subcommand
Note that all xprotect commands must be run using the sudo command and an admin password in Terminal in order for them to work.
For example, running sudo xprotect update prints:
Starting update.
No update applied, already up to date
when there are no new parts of XProtect to download.
How Apple responds
As Apple notes, when XProtect detects malware Apple may respond in several ways - including but not limited to:
- Any associated Developer ID certificates are revoked
- Notarization revocation tickets are issued for all files
- XProtect signatures are developed and released
spctl command-line tool
In general, you can also check your Mac's system security policies in Terminal using the spctl command line tool:
spctl --status (System Policy Control).
If security scanning is enabled you'll see this response:
assessments enabled
spctl has a huge array of options and tools - so you'll want to check the man page out in Terminal for more info.
Can XProtect be disabled?
The answer is: mostly. But don't.
Unless your Mac is always offline, you rarely install software, or you're seeing specific performance problems, there's no real reason to disable XProtect. Doing so opens your Mac to a flood of known and unknown malware on the internet - and you're just asking for trouble if you do.
Having said that, if you absolutely must disable XProtect, you can do so in the Terminal with the following command:
sudo spctl --master-disable
To re-enable XProtect use:
sudo spctl --master-enable
and press Return.
Even if you do disable XProtect, you'll want to do so for as brief a period as possible - always re-enable it as soon as you're finished with whatever task required it to be disabled.
Third-party scanners
Although XProtect is managed by Apple and is part of macOS there may still be times when you want to run a third-party malware scanner on your Mac to look for malicious software.
Tried-and-true scanners such as Norton and McAfee have been around for decades, so they're always a safe bet. There are also smaller third-party ones that are good, such as PrivacyScan ($15) from SecureMac.com.
If you do use a third-party scanner, try to use one sold in the Mac App Store, since Apple reviews all App Store apps to make sure they don't contain malware either.
Apple has done a good job with XProtect, and for the most part, it's silent and reliable. You might want to turn on automatic security updates in System Settings just to make sure your Mac gets all the new vulnerability files and updates as soon as they are released by Apple.
 Chip Loder
Chip Loder






-xl-m.jpg)


-m.jpg)





 William Gallagher
William Gallagher
 Andrew Orr
Andrew Orr

 Christine McKee
Christine McKee

 Thomas Sibilly
Thomas Sibilly
 Wesley Hilliard
Wesley Hilliard








6 Comments
How? Definitely worse than Kaspersky.
Was this article written by AI perhaps?
From TFA:
"
Er, not it doesn't. Yara International ASA is "
YARA is actually provided by VirusTotal:
https://github.com/VirusTotal/yara
Get it together lads....
I guess it’s just how things evolved over the decades, but it’s hard to understand why system security and virus protection wouldn’t be a core function of the operating system itself, or why it should be possible for third party vendors to even be able to perform this function.
I appreciate your deep knowledge and experience. This article interesting and informative. Thank you.