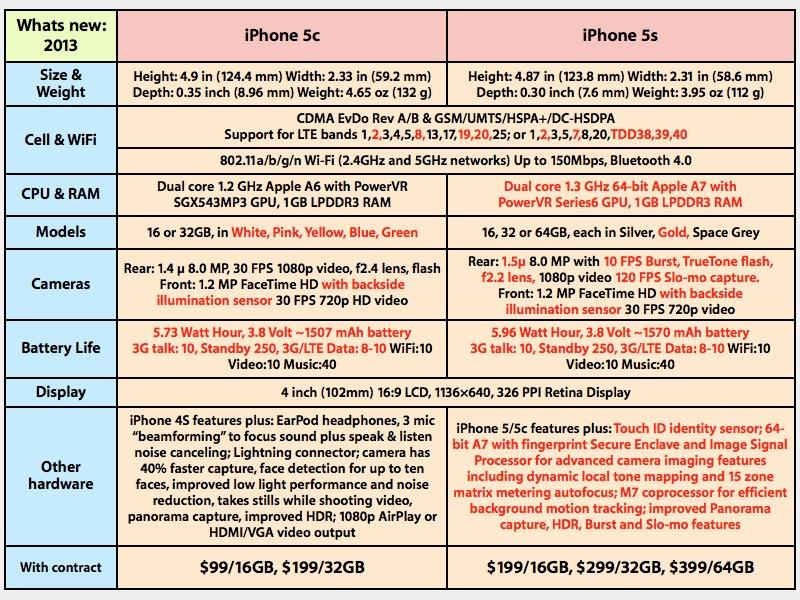
The new iPhone 5s positions Apple's flagship iPhone as a "forward thinking" high end luxury device priced the same as the model it replaces. It differentiates itself as a smartphone with an advanced new 64-bit processor architecture that powers a novel Touch ID fingerprint sensor and easy-to-use new camera features.
iPhone 5s delivers four major enhancements over Apple's bestselling iPhone 5 (which was already both the world's top selling iPhone and top selling smartphone): the new Touch ID for security and convenience; new camera-related features in hardware and software; an advanced new multiple-processors architecture that combines the speedy new A7 and background-task efficient M7; and new radio baseband components providing broader LTE carrier coverage and compatibility.
It's a pretty significant update. Below, new features compared to iPhone 5 are highlighted in red. In parallel, the new iPhone 5s repackages the previous model with a larger battery (sporting 2 hours of additional 3G talk time, up to two more hours of LTE data and 25 more hours of standby) and the same expanded LTE carrier coverage and compatibility features of iPhone 5s, for $100 less.
To help account for its beefier processors, iPhone 5s gets a larger battery, weighing in at 5.96 Watt hours. At 3.8 Volts, that appears to offer 1570 milliamp hours, compared to the previous iPhone 5 battery which was 5.45 Wh or 1440 mAh. It appears to easily outlast an iPhone 5, despite packing a larger processor and faster processing units.
What's new, #1: Touch ID
The most prominent external change is the new Touch ID fingerprint sensor. The Home button is now circled by a slightly inward-sloping metal ring (there to sense your finger's presence without a press) in the same finish color as the chamfered sides of the device (in Silver, Gold or Space Grey).
Rather than being slightly concave as previous iPhone Home buttons, the new sapphire Home button disc within the ring is placidly flat. Because the ring's edge lies perfectly flush with the front surface of the device and the button within is slightly recessed, it feels virtually identical to previous Home buttons.
The mechanical "click" action of the button feels the same, too, although its flat surface has a slightly nicer contact feel when depressed, similar to a high quality keyboard key. There's a slight optical illusion that makes the new Home button look smaller on the face of the phone, thanks to the color-accented metallic ring calling prominent attention to the button's periphery.
This results in a juxtaposition of Touch ID being both readily apparent and, essentially, invisible at the same time. Apple's software implementation of Touch ID is also intentionally invisible.
As Apple's software guru Craig Federighi noted in describing the feature to USA Today, there's no movie-style depiction of "scanning… authenticated!" with animations, buzzing or flashing lights for feedback. It just works: touch, unlock.
How Touch ID works
AppleInsider began reporting the potential functionality of AuthenTech's next-generation capacitative fingerprint sensor over a year ago as Apple urgently acquired the company and its advanced technology portfolio.
Setting up a new fingerprint is simple, as demonstrated last week in the hands on video of the process. The process seems to consistently work reliably, if you follow the instructions during setup.
I wasn't able to trigger any false positives to bypass the system, and false negatives seemed to be a result of focusing the setup on one part of your finger (the main pad, for example), then trying to unlock with just the tip.
If you get a "try again" rejection and correctly authenticate on the next touch, it learns from the process and enhances to your fingerprint profile, making successful recognitions progressively better. If you fail to login with a fingerprint five times in a row, it stops letting you try and insists that you enter the passcode.
Touch ID & security
All of the test scans I set up involving different users and different fingers were consistently accurate. This included fingers with scars and imperfections from healing wounds, of which I have plenty to test against. Touch ID is not a beta gimmick feature, it just works.
I was also able to get the system to recognize prints from a specific area on my palm, and toe prints also reportedly work, but I could not setup my nose, which some cold weather folks might like in the winter. Seems we don't have enough ridges and valleys on our faces for the system to identify. You can successfully configure a certain other appendage, but can't actually log in with him, just in case you were wondering about all of your available options.
A described bypass process involving lifting a user's print with a very high resolution scan and creating a 3D model fingerprint also requires some expert photo enhancement and cleanup of the fingerprint image, printing a transparency and then creating an offset print in latex. In ideal conditions, this lab process would appear to take hours. It's certainly not a simple hack, and requires a very high quality image of a known, specific print. Anyone attempting to use it would also only have five tries to get it right before locking out additional attempts. Powering off the device, or waiting more than 48 hours between Touch ID logins, also triggers a mandatory passcode login.
I attempted to create a simple wax print of a configured finger, but while I could craft a wax layer with a clearly discernible print, the system refused to even recognize it as an attempt, let along pass it as a match. In trying to spoof the system, it becomes clear how difficult of a task it actually is to try. Touch ID has not exactly been "hacked wide open," even if experts ostensibly may be able to fool it in the lab (if they first obtain a high resolution image of a configured print).
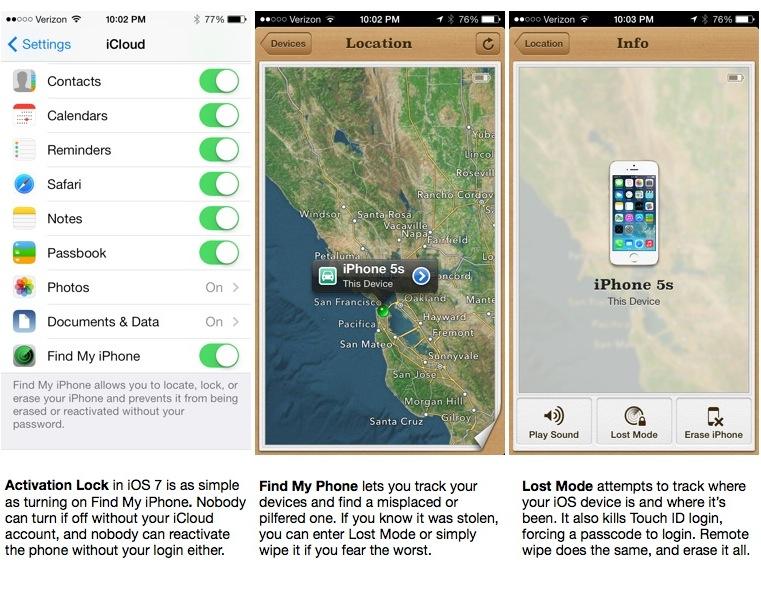
The limited value of such an expensive attack on Touch ID also limits the likelihood of it ever being attempted in the real world. On top of the basic time constraints, anyone who has their iPhone stolen can remote lock ("Lost Mode" in iCloud's Find My iPhone) or wipe the device. Once locked, the device no longer allows a fingerprint login attempt. If you go all the way to wiping it, the full disk encryption of the device is wiped.
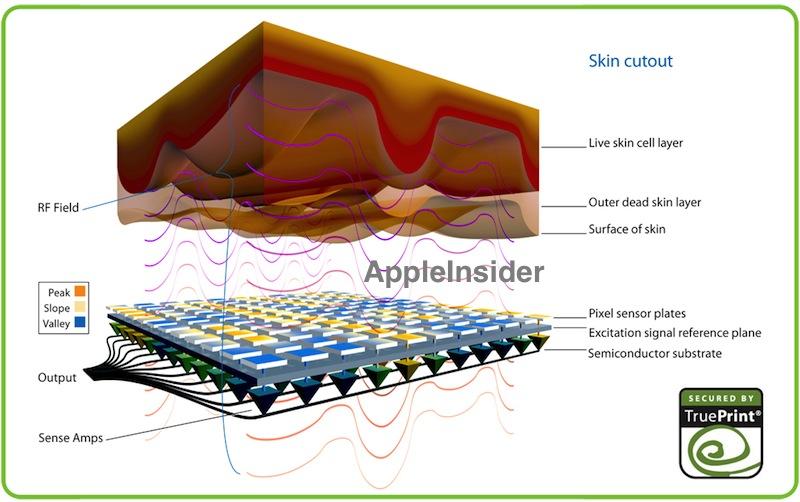
Using a fingerprint to unlock the device is equivalent to assigning a very complex password you don't have to call to mind to use. When you configure a new fingerprint, unique information about your print is stored in an encrypted "Secure Enclave" in the A7 Application Processor.
This takes advantage (apparently) of ARM's TrustZone architecture for secure data storage that is kept strictly separate from the general computing environment. This means that a rogue app you install by mistake can't access the data. It's also not stored or backed up to the network, so there's no potential for a snooping "man in the middle" attack.
Speaking to BusinessWeek, Federighi said of the Secure Enclave, "the main processor—no matter if you took ownership of the whole device and ran whatever code you wanted on the main processor—could not get that fingerprint out of there. Literally, the physical lines of communication in and out of the chip would not permit that ever to escape."
What Touch ID does
iOS 7 currently only exposes two features for the Touch ID sensor: Passcode Unlock and iTunes & App Store purchasing. This has allowed the company to focus entirely on getting the initial experience right, rather than unleashing a confusing blizzard of half baked feature concepts, or erring in other ways that, as Federighi added, "would be worse than never having done the feature at all."
In practice, being able to log in with a finger press is both a quick convenience and an intuitive mental simplification over having to manually type in a passcode, the same as having a proximity key that lets you get in and start your car without dealing with physical keys. This Touch ID convenience makes it much more likely that you'll use a passcode, and set your phone to lock immediately. Logging in with a finger touch is essentially just as fast as unlocking the phone without a passcode set
Initially, it felt a little foreign to touch the sensor to login. But after a day or two, it was strange to go back to an iPhone that required typing in its passcode. Apple says half of its users aren't using a passcode at all, and it's likely that even many of those who do, opt to set a delay period so they don't have to type it in every time they wake their device. With Touch ID, it's not a problem to have your phone locked all the time. Logging in with a finger touch is essentially just as fast as unlocking the phone without a passcode set.
While intrepid tech reporters have been frantically searching for evidence to prove their hunch that this is all just security theater that actually puts users at great risk for being violently maimed by thieves and can likely be worked around by the NSA's supercomputers or a lab of imaging experts, the reality is that the alternative is to either not use a PIN, or to rely on a simple 4 digit number that is quite easy to guess, or to configure a more secure passcode that will require an unreasonable effort to type in every time you wake your phone.
Apple's Touch ID certainly isn't designed to make your iPhone 5s impenetrable to spy agencies with billion budgets trying to stop you from amassing WMDs. But the reality is that Touch ID is more accurate, faster and more secure than a simple passcode, or the alternatives on the market: the easy-to-eavesdrop 'swipe to unlock' gesture used by Google's Android, or its gimmicky Face Unlock experiment. The latter provides a great example of how being first to market in a category (such as biometrics) is not better than being first to market with a great product.
Apple hasn't just beaten Samsung to market with workable fingerprint login as a feature, but it's made it known that Touch ID enhances security and is designed to deliver a great product, rather than being an invasive spyware tool designed to collect information about users and what they do, as Samsung demonstrated when it gave away a "free" music app in Google Play to its Galaxy customers. Who could trust Samsung or Google with their fingerprints after such shenanigans?
Using Touch ID with Activation Lock
Further enhancing the Passcode Unlock functionally of Touch ID is iOS 7's new Activation Lock capability, a new feature that activates automatically when you configure a device with a free iCloud account and turn on "Find my iPhone."
Activation Lock appears to link the device's activation process with its firmware ID and your iCloud account, so that if your device is stolen, a thief can't simply wipe it for quick and easy resale. Many stolen phones are collected for batch resale overseas, making U.S. carriers' blacklisting of stolen device IMEI numbers ineffective at addressing the problem. Apple's solution involves something it has that the Android platform does not: a centralized activation process.
The security afforded by Activation Lock is therefore similar to carrying a credit card instead of large amounts of cash. Crooks can still hold you up at gunpoint, but they can't be guaranteed a significant, quick and dirty payoff. Activation Lock an attack on criminal motive.
Effective security isn't a matter of building impenetrable systems, but rather of making successful attacks too expensive or difficult, while reducing the potential payoff to the point where the crime is simply not cost effective anymore. Activation Lock takes the current assumption that burgled or snatched iPhones can be easily wiped and resold for around $500 or more and throws a wrench into that business plan.
Apple has made Activation Lock available to every iPhone back to the 2010 iPhone 4 via the free iOS 7 update, which in just days has converted what appears to be around half of the entire installed base. Using Activation Lock doesn't necessitate a passcode on your phone, and turning off iCloud's Find My Phone isn't possible without your iCloud account. However, if a phone is unlocked, it could be possible for a thief to reset your iCloud password using access to your email and iMessage account.
Therefore, effectively using Activation Lock requires that you use a passcode. Touch ID erases the pain of doing so, allowing you to set a more complex passcode as well. This radically enhances the device level security of iOS users, both of their data and the resale value of their phone. Activation Lock and Find My Phone won't necessarily get your device back if its stolen, but it serves to put thieves on notice that a locked iPhone with iOS 7 is not an easy way to get $500 or more.
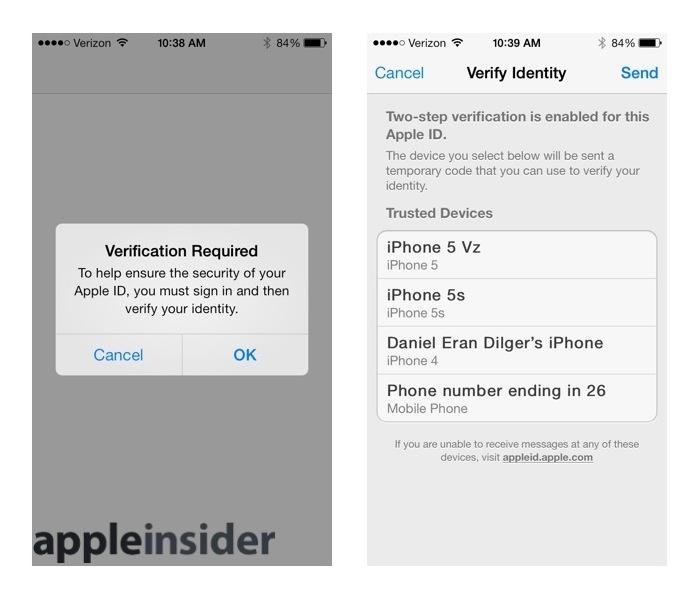
iPhone users should also configure iCloud / Apple ID to use "Two Step Verification," Apple's name for two factor authentication, which basically verifies password reset attempts by requiring physical access to one of your configured devices to get the verification message Apple pushes directly to that device. This prevents a remote user from being able to change your password by simply guessing, and allows users to remove verification access on a device that's stolen or gone missing.
Using Touch ID with iTunes & App Store
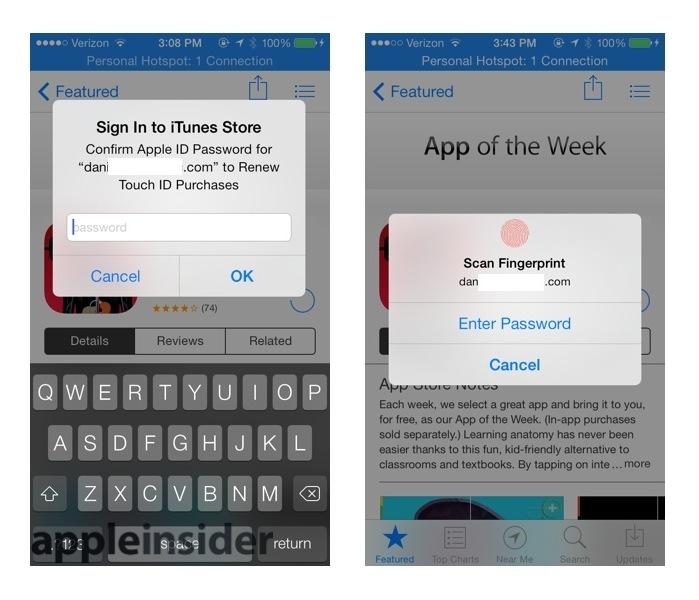
The other (optional) use of Touch ID is to authenticate purchases in iTunes or the App Store. Apple currently requires you to sign into your account to make a purchase, and sign in again after a 15 minute interval has expired. If you already have a secure Touch ID fingerprint configured, you can bypass signing in by turning on this new Touch ID feature.
When you first activate iTunes purchasing, it asks for your iTunes account password (above left). From then on, you can use your fingerprint instead (above right). Apple's priority for Touch ID was to secure users' devices, a task it had been working on for some time. However, the infrastructure behind Touch ID as a passcode clearly has broader applications, and the fact that Apple is launching it with iTunes support hints at plans for Touch ID for authenticating sales and adding security to other transactions.
While the media was initially enthusiastic about Google's launch of Wallet with NFC-tap authentication, there were too many security and compatibility problems in the poorly integrated, large scale rollout, resulting in both a collapse of the system and a big black mark against Google's credibility in managing digital payment transactions. More importantly, Wallet and NFC didn't really solve any real world problems. It simply replaced (in the U.S.) swiping a magnetic credit card with tapping a device. The only potential beneficiary was Google.
Touch ID immediately makes it more convenient for Apple's iPhone 5s customers to make online iTunes and App Store purchases. It doesn't require signing up for new accounts, and doesn't replace one easy swipe with another easy tap; it replaces a moderately annoying password prompt interruption with a finger touch. Once the company has more experience with how customers use it, it can move development forward.
What else Touch ID could do (but doesn't)
Outside of iTunes, there are other obvious applications for Touch ID, from authenticating purchases online to making purchases in person. Both would require a secure token infrastructure, because Apple will likely never allow apps (certainly not web apps) to directly access the Touch ID sensor.
"One place where that could be a bad idea," Federighi explained, "is somebody who writes a malicious app, somebody who breaks into your phone, starts capturing your fingerprint."
It is likely, however, that Apple could expand its existing payment system for iTunes to allow you to also send money or make purchases using a Touch ID-authenticated secure token that does not include any fingerprint data. Touch ID could similarly be used to digitally sign documents or verify your identity in other ways, likely in conjunction with its new iBeacons microlocation technology.
Additionally, the technology behind Touch ID can do far more than what Apple is exposing. It could be used as super high resolution touchpad controller, affording precise touch based gestures as shortcuts, were Apple interested in using it for this purpose. Additionally, configured prints from different fingers could be used to launch specific apps.
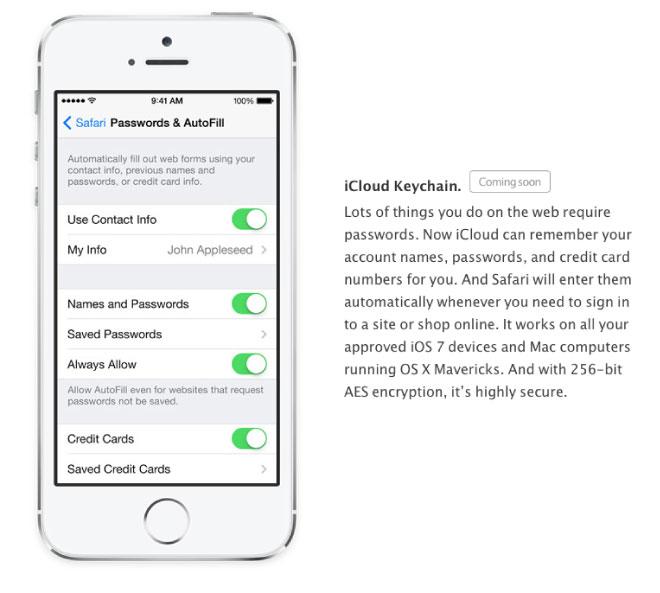
One conspicuous omission is iCloud Keychain, a feature of OS X Mavericks that securely syncs your keychain of account passwords and other credentials between your desktops and devices (restoring a feature lost in the transition from MobileMe back in 2011).
The feature appeared in developer releases of iOS 7, but did not ship publicly, likely because Apple is still perfecting the software, and also because it requires new software on the Mac side, too. OS X Mavericks is expected to launch next month.
Apple's measured launch of Touch ID is realistically a good thing, as overloading it with too much functionality for the sake of novel "innovation" would distract from the core value of the new sensor: securing devices, clamping down on theft and speeding sales though iTunes. It would be disappointing if Apple doesn't carry this further over the next year and into iOS 8 however.
At the same time, it's disappointing that, equipped with such a simple authentication system, Apple didn't at least include the option to also secure features such as turning off WiFi or mobile data, or requiring authentication to turn the device off. Find My Phone has now been around for over three years. Most thieves know to power a stolen device off immediately. Leaving it forced-on in an iCloud-trackable state could help recover devices stolen by anyone other than an idiot.
As implemented, Touch ID delivers geek cred and elegant sophistication at the same time. It adds distinctive novelty to iPhone 5s, makes it far more likely that users will secure their phones and erases the annoyance of having to constantly unlock or sign into iTunes. As a reason to upgrade, it makes sense for users for whom device theft is a real possibility and who are tired of typing in a passcode. But it's not the only new feature of iPhone 5s.
What's new, #2: Camera & True Tone flash
For many people, having an adequate camera available at all times isn't just convenient, it's downright life changing, as Apple touts in its "iPhone Every Day" ad. When the iPhone debuted in 2007, it had only a marginal camera, but its touchscreen-enabled iOS features and apps gave it a strong edge over simpler camera-phones from Nokia and Samsung equipped with much better cameras.
For the release of iPhone 4 in 2010, Apple began taking camera development seriously, introducing two cameras: a front facing shooter acceptable for the new FaceTime, as well as a rear sensor and optics capable of 720p video and quite decent photos. It also was capable of supporting HDR, which uses software processing to help make up for the limited dynamic range inherent with tiny mobile imaging sensors and optics.
Since then, iPhone 4S and 5 have supplied significantly better imaging sensors and optics. In addition, new software features like face detection and electronic image stabilization are being powered by a dedicated image signal processor (ISP) included within Apple's A5 and A6 Application Processors. The ISP also accelerates focusing, shutter responsiveness and other processor-intensive features like HDR and Panorama capture.
The latest iPhone 5s pushes ahead on all these fronts, adding a 15 percent larger larger sensor (with the same megapixel count, but using larger 1.5 micron pixels for noticeably better photos). It enhances its optics to support a larger f2.2 aperture, which allows more light to hit the sensor for capture. These factors combine to deliver noticeably better photos, with significantly more detail and less noise and visible grain, particularly in low light conditions (below, iPhone 5s on left, iPhone 5 on right).
The A7's ISP is also enhanced, enabling the iPhone 5s camera software to support much more sophisticated video and still imaging effects, perform those effects faster and work with large amount of image data very quickly, enabling a range new software features. Apple says when taking a shot the camera's ISP begins automatically setting the white balance, generates a dynamic local tone map, and performs autofocus matrix metering across 15 focus zones. There's also new Burst & Slomo shooting modes, and Panorama capture is greatly enhanced.
There's also a new "True Tone" flash unit with both a cool white and warm amber flash that are used together in independently variable degrees to match the needed flash intensity and color temperature with the ambient lighting conditions when taking low light photos.
The same subject above, shot with the flash on (below, iPhone 5s on left, iPhone 5 on right) reveals more detail and banishes shadows, while also appearing to allow the camera to focus better.
Using True Tone Flash
Flash on a mobile device typically means an LED lamp. Unlike the xenon flash on a point-and-shoot, an LED "flash" isn't as bright but also consumes far less power. This also means the "flash" can be used as a lamp while recording video.
Typically, however, a mobile LED flash just goes off accidentally when you forget to turn it off. The results are often unflattering, and generally only ever better than nothing (sometimes worse). Additionally, when using LED flash in a dark setting, a mobile camera usually can't focus fast enough to deliver a sharp picture. So LED has historically been best suited to wiping out your battery.
True Tone helps out in a number of ways. First, the concept is to intelligently light up a subject with a balance of light to deliver accurate colors and flattering skin tones. This does work; it helps a lot to improve lighting both as a fill flash in settings with limited or indirect light, and in illuminating a subject in the dark. True Tone also lights up longer, which combined with the faster ISP, lets the camera actually focus on the subject.
The downside is that it can be blindingly bright, and requires a double flash: one to get information about how to set the flash, and again to actually take the picture. Despite the downside, True Tone on the iPhone 5s might change your mind about the usefulness of flash and allow you to capture shots you couldn't otherwise get.
Using Burst, Slo-mo and Panorama Camera features
The camera in iPhone 5s appears to take significantly better photos. Additionally, there seems to be less purple light bounce in its optics; a light source in or near the subject may cause a peripheral purple haze of light pollution for iPhone 5, but the issue is much improved with iPhone 5s. Also enhanced is HDR, which now occurs almost instantly and often results in more detail and sharpness (below, iPhone 5s on left, iPhone 5 on right)
Another significant beneficiary of the improved image processing in iPhone 5s is Panorama capture, which can now adapt to changing light conditions across the shot via dynamic auto exposure. Below, two greatly scaled down panoramas captured from Corona Heights in San Francisco, with inset detail. Both were captured at once at the same pace.
iPhone 5s captures more foreground detail and avoids blowing out the sky at the horizon. It also copes with the bright sun to the West better, while iPhone 5 washes out before it even gets to Sutro Tower on the far left.
Burst mode, demonstrated in our initial hands on video, allows rapid 10 frame per second captures that are presented as a "stack" in Photos, with the system marking recommended best shots. You're free to select any of them for saving, and can then delete the rest. However, other apps (such as Instagram) don't have access to the images in a "Burst stack." They can only see the top image until you enter the Favorites menu of the stack and select specific images for saving as standard pictures.
Another thing to keep in mind about stacks of Burst photos: iPhoto currently sees them all as individual photos, and once you import them and delete the photos off the phone, there's no way to get the Burst Favorites menu back. You now have ten photos per second worth of photos filling up your iPhoto library you have to manually sort through. It would also be nice to have a built in mechanism for capturing and sharing a stack of photos as a .gif flipbook.
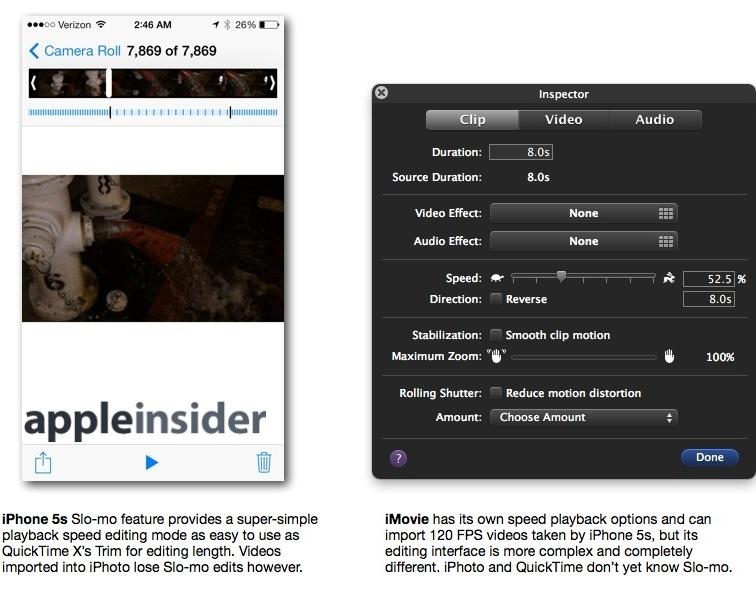
Slo-mo capture, also demonstrated in a hands on video, grabs 120 frame per second video and then presents a similar, specialized editing interface for setting simple in and out points for creating a dramatic video that drops down to quarter rate playback for a period. This is a super easy way to add interesting and dramatic flair to your videos.
However, once you import the videos into iPhoto, they become flat 120 fps videos that play at normal speed. To keep the Slo-mo effect, you have to expressly Share it via AirDrop, Email, iMessage, iCloud, YouTube, Facebook or Vimeo. This "freezes" your set slow-motion in and out points and delivers a standard 30 fps movie with a (no longer editable) Slo-mo effect intact.
Other apps on your phone don't see the Slo-mo effect and apps such as Instagram don't currently seem to work with the 120 fps video at all. iCloud Photo Stream doesn't automatically upload your videos (Slo-mo or no) and also doesn't yet understand Burst stacks; it just uploads the first image of the Burst.
After sharing Slo-mo clips, you can continue to edit the Slo-mo video on your phone. Essentially, as long as it remains on the phone, it's kept editable. However, once you export videos to your computer, you'll have to use iMovie or another app to change the playback rate to have your effect. However, creating slow motion effects in iMovie is completely different, and requires cutting your video into clips and manually setting the playback speed for each.
Apple needs to make iPhoto both Burst and Slo-mo "aware" so you could perform the same simple editing effects you can within the iPhone 5s Photos app. Until that happens, there should be some warning that all your Burst favorites and Slo-mo settings you have on the phone will be lost if you export them to your iPhoto library, with no way to restore them back to your device afterward.
What's new, #3: A7 & M7 Processors
The new iPhone 5s debuts the world's first 64-bit processor architecture used in a smarphone. However, the more important aspect of the A7 is what it can actually do. That's evident on a few fronts: it's currently the only way to deliver Touch ID, which does some sophisticated math but also requires secure data storage provided in the A7's Secure Enclave.
The A7 also packages the ISP used by the camera, along with dual ARMv8 CPU cores custom developed by Apple under the code name "Cyclone" (closely following the A6's "Swift" core design), and appears to be the first to use Imagination Technologies' advanced new PowerVR Series6 Rogue GPU architecture, providing new support for OpenGL ES 3.0.
The new M7 motion coprocessor is effectively an external feature of the A7, as it handles functionality that was previously part of the A6.
Being external appears to enhance the efficiency of the overall system when tasked with processing background motion events, allowing health related features (like a step counter) to remain running without taxing the battery. The benefits of the M7 will become more apparent once more software is written to take advantage of the new architecture, which Apple supports in its new Core Motion API.
Using A7
Putting the A7 to work and evaluating the advantages of its new 64-bit architecture is not as easy as benchmarking a desktop Mac. Sure, you can run benchmarks and see that the new iPhone 5s is indeed faster than the iPhone 5 it replaces. However, mobile devices aren't usually tasked with running processor-intensive apps like Photoshop (outside of gaming, of course), so there aren't many cases where today's users are aching for increased processor speed to run their current crop of apps.
That being the case, Apple must constantly find new applications of the horsepower it is packing into its chips. Touch ID and the new and improved camera features are prefect examples of this. They simply wouldn't be possible on a slower chip. Once the power is there and broadly available, third parties can take advantage of it in video games and other apps making novel use of such enabling technologies.
Note that this isn't really happening on other mobile platforms despite the availability of fast hardware, due to fragmentation and an apps focus on the lowest common denominator. The majority of new iPhone sales has historically gone to the latest and greatest model. In contrast, other brands offering premium hardware, like Nokia and Samsung, are selling the majority of their phones in low end categories.
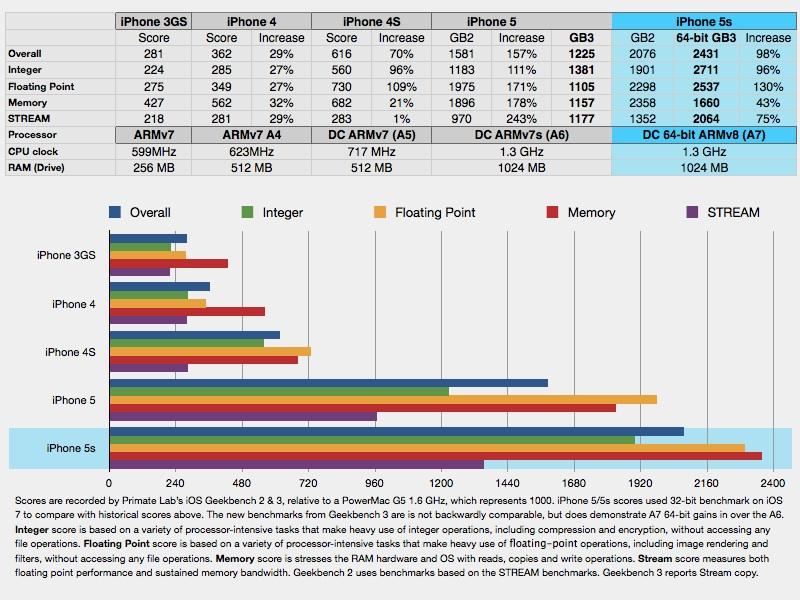
The A7's Cyclone CPU cores report better performance than last year's A6 even at the same clock speed, with the same amount of RAM, and when running 32-bit benchmarks. In addition to providing 64-bit data processing and benefitting from the modernized 64-bit ARMv8 instruction set, the A7 is also equipped with L1 instruction and data caches that are twice as large (64KB, compared to 32KB on the A6), and has twice the integer and floating point registers.
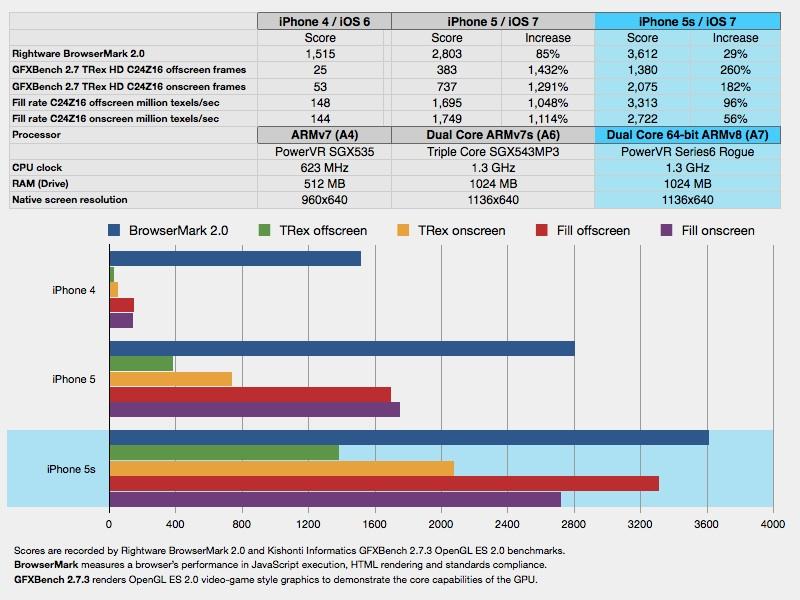
Using Primate Lab's new Geekbench 3, which supports 64-bit benchmarks, the A7 processing scores are around twice as high and memory tests are improved significantly. The scores are relative to a 1.6GHz PowerMac G5, so by these numbers the A7 is 2.7 times faster at integer math than a fast workstation-class machine that powered professional work less than ten years ago.
Rightware BrowserMark 2.0 provides a real world test of performance that indicates a major improvement in iOS 7's browser itself, although the new A7 chip executes the web-based benchmark 29 percent faster than last year's iPhone 5 running the same software.
Graphics performance is also interesting on the A7, because many of the standard algorithms that CPU benchmarks test are not run on the CPU anymore. As GPU technology outpaces CPU performance in a number of specialized ways, it now makes more sense to run a variety of tasks on the GPU (or other specialized processing units, like the A7's ISP or its external M7).
Apple recognized this trend many years ago, introducing OS-level hardware acceleration of graphics in OS X and making it a key differentiator in iOS on the original iPhone. In parallel, Apple also launched OpenCL as a common, standardized way to offload more general computing tasks on the GPU. The new Series6 Rogue GPU on the A7 has specialized enhancements of its own, including support for both OpenCL and OpenGL ES 3.0.
GFXBench 2.7.3 tests OpenGL ES 2.0 performance, and the gains it shows over previous iPhones is pretty spectacular, with frame generation scores 3.6 times higher than iPhone 5. The vast span of performance increases in GPU speed since the 2010 A4 actually make it pretty astounding that Apple can support iPhone 4 in iOS 7. Doing so requires scaling back some of the processor intensive effects on display on newer hardware, such as live translucency in Notification Center.
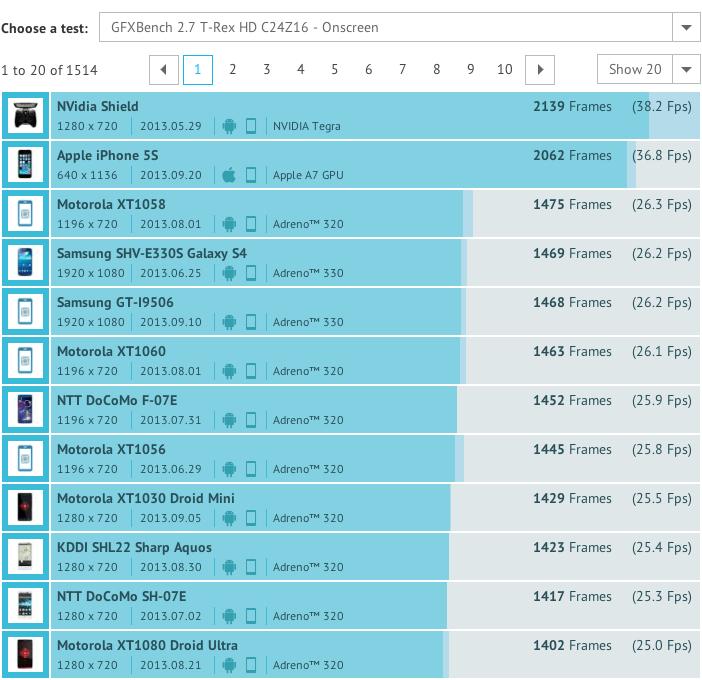
GFXBench scores indicate that onscreen graphics performance of the iPhone 5s very close to the Nvidia Shield, a dedicated video game console that shipped this summer and was described by its GPU-vendor creator as "a revolutionary new gaming and entertainment device designed for the modern gamer." Critics called it impressive hardware dogged by "impractical cost and a scarcity of compelling games" while CNET noted "there is currently a lack of available games worth your time."
Onscreen performance is a function of both the raw processing power of the GPU and the resolution of the display it must drive. Apple's design choices in providing a Retina Display but not simply going for maximum pixels allows it to beat other high end smartphones by a significant margin in this real world experience metric, while also delivering better battery performance without going for a massive battery. At the same time, Apple's iOS platform is also seeing real development of new, exclusive apps and impressive video games, so it's not just adding wasted hardware for bragging rights.
Outside of games and special, processor intensive apps, it can be hard to spot all of this new performance under the hood compared to iPhone 5, because last year's phone was already very fast. Perusing 3D Flyover Maps feels about identical, as does the speed of overall interface animations and the length of time it takes to do things like check mail. The primary everyday beneficiaries of the A7's power are Touch ID (which in turn makes unlocking much faster) and the Camera, where existing features like HDR are slightly faster, and new features like Burst are now possible.
What's new, #4: New LTE support
Apple's incredible progress in putting faster and faster chips in its iOS devices has been blunted somewhat by the fact that mobile devices are often hamstrung by their network connection. If you're accessing the web or saving data to the cloud or streaming music, the weakest link isn't likely your Application Processor but rather your mobile data connection.
The original iPhone started out as one of the last premium smartphones still stuck in the pre-3G world of AT&T's GSM/EDGE. Over time, it gained support for 3G and then increasingly faster versions of 3GPP 3G standards, from 7.2 Mbps HSDPA (downloads) on iPhone 3GS to 5.8 Mbps HSUPA (uploads) on iPhone 4 and 14.4 Mbps HSDPA on iPhone 4S.
Last year's iPhone 5 added the first support for 4G LTE networks as well as DC-HSDPA (with downloads up to 42Mbps, it's at least as fast as most carriers' 4G LTE service). This year, the iPhone 5s (and the redesigned iPhone 5c) both use the same Qualcomm MDM9615M Baseband Processor but it's paired with a new WRT1605L receiver, allowing it to work with more networks over new LTE bands and China's TDD-LTE variant used in that country and in Australia, the Middle East and some other places.
Both new models have identical carrier support, shifting from iPhone 5's three hardware models to four versions of the iPhone 5s (A1533 North American GSM/CDMA for AT&T, T-Mobile & Verizon; A1453 Sprint/Japan CDMA with additional support for LTE bands 18 & 26; A1457 for Europe lacking LTE bands 4/AWS, 13, 17, 18, 19, 26 but adding 7; A1530 for Asia/Pacific, identical to Europe but adding support for China Mobile's TD-LTE bands 38, 39 and 40, also used in Australia).
There's now support for many more LTE bands than before, allowing broader global compatibility with new, additional carriers. There are some potential features Apple isn't supporting: one is simultaneous CDMA voice while using LTE data (which would require dual radios, as a few higher end big phones have). Apple does have support for VoLTE, which puts voice calls on the LTE data network, but most major carriers haven't yet rolled out support for this.
Apple also supports "wideband voice," which uses more wireless cellular bandwidth to deliver a higher quality voice call. This also only works on a few carriers, as each company builds out its own technologies and support for various available standards (there's so many to choose from!).
Apple also has its own high quality VoIP technology: Audio FaceTime, although again, carriers have been slow to support this over their 3G/4G networks. This largely restricts it use over WiFi. When you have a WiFi connection, you may be amazed at how much better a FaceTime call is in both quality and reliability. You can also use FaceTime to connect to Macs, iPads and an iPod touch, and of course connect via a video FaceTime call as well.
What's missing
It would be great if Apple could link FaceTime with phone numbers as seamlessly as it linked iMessage with SMS, enabling users to upgrade calls to FaceTime when available on the other end. As it is, the company has added prominent FaceTime options to Contacts.
And speaking of FaceTime and missing features: why hasn't Apple clued into the appeal of Snapchat-style expiring picture messaging, or videoclip texting, or walkie-talkie voice messaging, or all of the above?
Another feature missing from the new iPhone 5s and 5c is the emerging LTE-Advanced, which features downloads up to 150 Mbps (and requires an entirely new baseband system). The technology appears to currently be in use primarily in Korea, where both LG and Samsung are releasing the first network equipment and handsets.
Also unchanged its support for Bluetooth 4.0 with Low Energy, and 802.11a/b/g/n WiFi wireless networking on 2.4 and 5 GHz bands. Apple didn't add support for the latests 802.11ac standard it recently began adding to its AirPort base stations and latests MacBook Airs. However, like last year's iPhone 5, the 5s and 5c both support WiFi data rates up to 150 Mbps, and reach that in real world tests.
Apple could improve upon WiFi throughput without jumping to 802.11ac simply by adding more antennas, just as existing generations of MacBooks can achieve 300 or 450 Mbps using 802.11n. Given the space constraints within today's iPhone, the limited deployment of faster-than 150Mbps WiFi, and the difficulty in actually making practical use of network data rates faster than that in a mobile device, it does not seem to be a significant omission.
The biggest lapses in iPhone 5s relate to new features: Burst and Slo-mo capture having no support on the desktop or iCloud side; the 64-bit A7 and new M7 chip having no outstanding software applications yet, and Touch ID lacking an extravagant portfolio of commercial applications.
Hold on to your hats, because Apple sold 9 million iPhones this last weekend, guaranteeing that iPhone 5s will inherit the "worlds biggest installed base of smartphones" title, necessitating rapid support from Apple and its third party partners.
iPhone 5s in Review
iPhone 5s assumes a middling role as the minor successor of iPhone 5, simply enhancing last year's major jump to a larger screen and 4G LTE networking. But it's really kind of a big deal. There's really no reason apart from Tim Cooks' gentlemanly southern humility for this advanced portfolio of industry-disrupting technology not to claim the status of iPhone 6, or even iPhone 7 for that matter.
If you need the latest and greatest, you don't need to be told that iPhone 5s is the bees' knees. If you passed on iPhone 5 waiting for a more serious SKU to sweep you off your feet, the 5s sweetens the pot with a fancier camera, a handy new way to enhance your mobile security without the regular annoyance of tapping in your credentials, and the future-proofing of a world-leading 64-bit miracle in mobile technology. And gold: it comes in a finish that whispers affluence and plugged-in, fashionable techno-chic, with a dazzling metallic ring that begs for a demonstration of the unbridled futurism you wield in the palm of your hand. You got the iPhone 5s.
iOS 7: Rating 5 out of 5
A free download for exiting iPhone 4/4S and iPhone 5 users: an awesome deal with nary a drawback unless you're afraid of the future or question the effect that animated, day-glo colors might have on your reputation as a serious business person. Relax and enjoy the parallax. Apple has thousands of developers at work, massaging iOS 7 into a very comfortable experience that does all sorts of thinking for you in advance.
All that's left up to you is to decide which year of technology you want to run it on. It's 2013, why not opt for the latest bit of hardware, the one that squeezes every last drop of power out of the billion dollar A7, and highlights every bit of potential radiance imagined by Sir Jony? Not too worry if you're short on resources: iOS 7 still animates iPhone 4 as well.
iPhone 4S: Rating 2 out of 5
Slightly cheaper than iPhone 5, but missing 4G LTE data, a much improved new case and larger screen and a variety of other substantial improvements. Hardly worth settling on to save $4 per month over a two year contract. Come now, if you can afford a cellular contract don't skimp on your handy. You'll be using it every day this year. Sell your handset (iPhones retain tremendous value) and upgrade yourself into the future.
iPhone 5c: Rating 3 out of 5
Not too shabby, and if you recently purchased one, you can be fully content that you have nearly the best smartphone available this year. The camera is good, the network speed can't really bet bettered, and you can run any app near the top of where it was designed to run. Remember to turn on Activation Lock in iOS 7, although you will have to bother with typing in a password, but apart from that, there's no compelling reason to trade things in and upgrade unless you're gonzo for soaking up the latest in what can be done these days.
iPhone 5s: Rating 5 out of 5
Tens of thousands of some of the smartest people in America have collaborated to develop an advanced technology portfolio embodied in a product you can afford to own for use on a daily basis. Can you imagine not availing yourself of such a luxury? It has a monstrous chip with world-leading, advanced technology that springs to life when you authenticate with your finger, and gates into submission when you point it at your friends for a super-automatic photo or dramatic Slo-mo capture.
It also has something no other smartphone platform can offer: a rich array of the world's leading apps, created by thousands of developers who are fighting for your dollar or two in exchange for the best games, edutaiment and social connectivity the planet earth has to offer. You sprung for the world's greatest smartphone, why not spring for some amazing software to boot?
Pros:
- Solid, sophistiated construction
- Leading battery life even when using LTE 4G, without a big heavy package
- A7 processor blows the pants off of the other SoCs
- Camera makes you look good, particularly the True Tone flash
- Price competitive with lessor alternatives
Cons:
- Apple has some 'splaining to do with these new Camera features in iPhoto
- LTE is everywhere, but HD Voice and FaceTime audio aren't necessarily
- Perhaps you were looking for a screen larger than 4 inches
Trade in
Those upgrading to iPhone 5s can also check out AppleInsider's breakdown of trade-in offers for previous-generation iPhones. A number of online providers offer cash in return for a used iPhone 3GS, iPhone 4, iPhone 4S or iPhone 5, making the cost of the new iPhone 5s easier to afford.
 Daniel Eran Dilger
Daniel Eran Dilger



















-m.jpg)






 William Gallagher
William Gallagher
 Chip Loder
Chip Loder
 Marko Zivkovic
Marko Zivkovic
 Malcolm Owen
Malcolm Owen


 Christine McKee
Christine McKee
 Andrew O'Hara
Andrew O'Hara


-m.jpg)




44 Comments
as opposed to the 5s running iOS 6?
It's not the colour. It's the big flat blocks of it. Folder backgrounds I'm talking about. I have mostly folders on my home screen and now it looks like a pallete of water colours - except they are basically all the same colour. Plus, minus one star for dropping podcasts out of the music app again. Poor form apple.
Rather than allowing third party apps access to the fingerprint sensor, why doesn't Apple branch into online payment facilitation — like PayPal.
Perhaps iCloud Payments or simply iPay. Then Apple could leverage the huge number of registered iTunes accounts with credit cards that they have, and allow their customers to make secure online payments with their iPhone 5s.
Let's face it, Apple is more liquid than most banks at the moment!
A.
Rather than allowing third party apps access to the fingerprint sensor, why doesn't Apple branch into online payment facilitation — like PayPal.
Perhaps iCloud Payments or simply iPay. Then Apple could leverage the huge number of registered iTunes accounts with credit cards that they have, and allow their customers to make secure online payments with their iPhone 5s.
Let's face it, Apple is more liquid than most banks at the moment!
A.
No. As Tim has stated over and over: Apple is a PRODUCTS company. Payments is NOT their bailiwick. You don't mess with success. You simply keep doing the things that made you successful.
It's not the colour. It's the big flat blocks of it. Folder backgrounds I'm talking about. I have mostly folders on my home screen and now it looks like a pallete of water colours - except they are basically all the same colour.
Plus, minus one star for dropping podcasts out of the music app again. Poor form apple.
BETTER from, Apple! Podcasts AREN'T music!