Apple's iOS and OS X platforms aren't directly affected by the rampant malware infestations that plague Google's Android and Microsoft's Windows, but that doesn't mean they can't be victimized by it, as the collateral damage and smokescreen of a reanimated botnet targeting unpatched, vulnerable systems demonstrates.
A report by John Biggs of TechCrunch details how a massive Windows botnet, despite having been taken down by authorities last month, has been reused by thieves to create a distracting smokescreen that's being used to block fraud victims from accessing their own accounts while they are being hacked.
The "openness" of insecure platforms including Windows and Android (which now accommodates 99 percent of all mobile malware) are resulting in mass infections among large volumes of lower-end devices that are unlikely to ever receive security updates.
No updates are bad, m'kay?
Last July, a U.S. Government report titled "Threats to Mobile Devices Using the Android OS" warned that Android "continues to be a primary target for malware attacks due to its market share and open source architecture," and stated that this "makes it more important than ever to keep mobile OS patched and up-to-date."
A year later, Google still reports that more than 53.4 percent of active Android users accessing Google Play are still using an "Ice Cream Sandwich," "Gingerbread" or other editions of Android prior to 4.2 that still "have a number of security vulnerabilities that were fixed in later versions."
One specific Android WebView vulnerability was recently detailed by Dan Goodin of Ars Technica. While Google patched that particular flaw in Android 4.2, according to Google's published figures for its Play Store active user base, only 46.6 percent have installed that fix as of this week. Outside of Google's own apps ecosystem, the flaw is even more widespread.
"The WebView vulnerability," Goodin stated, "allows attackers to inject malicious JavaScript into the Android browser and, in some cases, other apps. In turn, it helps attackers gain the same level of control as the targeted program. The easiest way to exploit the bug is to lure a vulnerable user to a booby-trapped webpage. Within seconds, the site operator will obtain a remote shell window that has access to the phone's file system and camera. In some cases, the exploit can also be triggered by performing a man-in-the-middle attack while the victim is on an unsecured Wi-Fi network. By hijacking the app's update process, attackers can gain control over the same resources already granted to the app, including permissions such as access to SD cards and geographic data."
Compromised PC and Droid users are frequently not even aware that their devices are being used to do things that hurt others, including distributed Denial of Service attacks that provide cover for other, more targeted online attacks. Further, the damage resulting from those botnets can also be used to attack and disrupt users on secured platforms.
Increasingly sophisticated attacks start on insecure platforms
The ZeuS botnet, a network of infected Windows machines believed to include 3.6 million PCs in the U.S. alone, was publicly targeted by the FBI in 2010. Back then, the trojan malware was used to secretly capture users' credentials which its operators then used to access and rob the victim's bank accounts.
In 2013, Wired reported that 24 year old Algerian Hamza Bendelladj, the man believed to be the mastermind behind both the EyeSpy and ZeuS mass infections of malicious software, was arrested and his malware networks were taken down.
However, ZeuS components later reappeared in a new form as "Gameover Zeus" with enhanced, encrypted peer to peer communications designed to make the infection harder to track.
In June the U.S. Department of Justice announced that a global collaboration of law enforcement agencies had broken the centralized control the infection as part of an operation that "disrupted a global botnet that had stolen millions from businesses and consumers as well as a complex ransomware scheme that secretly encrypted hard drives and then demanded payments for giving users access to their own files and data."
The Justice Department's Criminal Division Assistant Attorney General Leslie R. Caldwell stated at the time that "these schemes were highly sophisticated and immensely lucrative, and the cyber criminals did not make them easy to reach or disrupt."
The investigation charged 30 year old Russian Evgeniy Mikhailovich Bogachev and identified him as "as a leader of a tightly knit gang of cyber criminals based in Russia and Ukraine."
Unpatched users of insecure platforms enable botnet resurrection
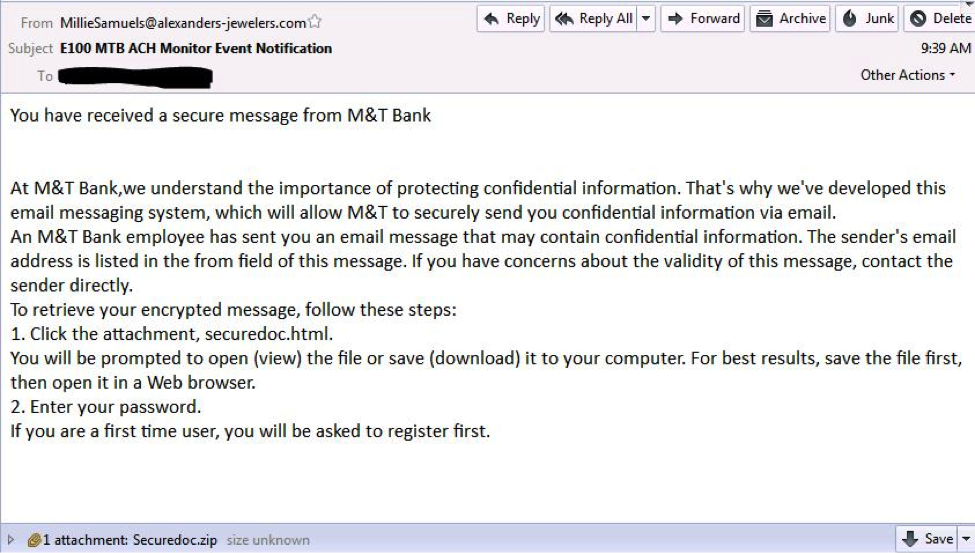
However, a month after taking the Gameover Zeus botnet down it has now reappeared in email spam distributions identified by Malcovery Security as phony messages asking users to install "securedoc.html" to enable secure banking communications.
"In the original GameOver Zeus, the domain generation algorithm and its associated command and control resources serves the botnet as a fallback to the peer-to-peer botnet which serves as this malware's primary means of distributing instructions to infected machines," the site explained.
"Using the websites associated with the domain generation algorithm the GameOver botnet operators may distribute commands to infected machines with which the peer-to-peer botnet has lost contact," it added, noting that "the binary that is dropped and injected into Internet Explorer after contacting the C&C is randomly named" to make it harder to identify.
Malcovery added that it had identified "a number of the command-and-control hosts believed to be involved in this attempt to revive the GameOver botnet. Following contact with any of these hosts, the malware began to exhibit behaviors characteristic of the GameOver trojan— including the characteristic list of URLs and URL substrings targeted by the malware for Web injects, form-grabs, and other information stealing capabilities."
Apple's tight security ship
Apple has made security a key selling point of its OS X and iOS platforms, including app signatures and other security measures in the initial design of the App Store at its birth six years ago this month.
Across 75 billion app downloads, Apple has been able to address and patch security vulnerabilities on an unprecedented scale and speed. Following the delivery of iOS 7 last fall, the company now notes that as of June, 89 percent of its users have installed it. In the months since, Apple has acted to quickly release interim patches for discovered vulnerabilities, including an SSL verification flaw that Apple addressed in a 7.0.6 update it then deployed before most users were even aware of the issue.
By the time Reuters reporter Joseph Menn could craft a misleading hit piece about the flaw, he had to admit that the fix had already been released by Apple.
Additionally, Apple not only patched the flaw for the 89 percent of users on iOS 7, but also released a parallel iOS 6.1.6 update addressing another 9 percent who haven't or can't upgrade to iOS 7.
At the same time, the far more serious Android flaw Ars described in February can't even be obtained by most Android users affected by it, because Google has refused to patch the older versions of Android those users are stuck on, and neither the manufacturers nor carriers who profit from selling Android devices see any need to make newer, patched versions of Android available to the majority of the Android installed base who can't upgrade.
Microsoft has scrambled over the past fifteen years to secure the hundreds of millions of PCs running Windows, prodded in part by Apple's once incessant Get a Mac ads that pointed out the embarrassing security and privacy issues affecting PCs in contrast to the relatively tranquil security enjoyed by Mac users.
So far, Apple has done very little to advertise its dramatic security advantage over Android with its own iOS devices. Corporations and government agencies are well aware of the issue however, resulting in adoption metrics that indicate Apple has maintained a lead in enterprise mobile devices and has kept a virtual lock on tablets adopted for business use with iPad. Good Technology reported in May that 93 percent of the custom corporate apps deployed by its clients are developed for iOS.
 Daniel Eran Dilger
Daniel Eran Dilger

-m.jpg)






 William Gallagher
William Gallagher

 Andrew O'Hara
Andrew O'Hara
 Wesley Hilliard
Wesley Hilliard

 Malcolm Owen
Malcolm Owen
 Marko Zivkovic
Marko Zivkovic





-m.jpg)




53 Comments
Fate of Android similar to that of Windows. Death by a thousand cuts.
Can't tell you how many people I know who use Samsung & Windows who pooh-pooh the idea of a phishing-botnet-malware attack on their equipment. I've almost given up talking about it except in a new business startup where some people from "corporate America" think Windows is the only way to get things done.
Putting the Gameover Zeus botnet in the same title with Android while there is no evidence of the Gameover Zeus botnet infecting Android (this btw also counts for the original Zeus botnet where there are no known infections within the Google ecosystem, only one outside of Play Store)? Typical. Well at least it gave DED the chance to regurgitate the same stuff again (for the thousand time).
"Trust me"... classic Get A Mac ad.
[quote name="Chipsy" url="/t/181343/gameover-zeus-botnet-reanimated-exposing-the-harm-in-open-android-windows-malware-platforms#post_2563330"]Putting the Gameover Zeus botnet in the same title with Android while there is no evidence of the Gameover Zeus botnet infecting Android (this btw also counts for the original Zeus botnet where there are no known infections within the Google ecosystem, only one outside of Play Store)? Typical. Well at least it gave DED the chance to regurgitate the same stuff again (for the thousand time).[/quote] Hmmm, after checking articles on other sites you seem to be correct. What does Gameover Zeus have to do with Android specifically? The linked TechCrunch article makes no mention of Android at all but perhaps DED assumed no one would go and read it. http://techcrunch.com/2014/07/11/crooks-reainmate-a-dead-botnet-to-target-high-value-bank-accounts/ Weird and deceptive headline if there's actually NO relationship which seems to be the case. :???: