A Google engineer has demonstrated it is possible for a malicious iOS app to spy on a user, with a proof of concept app capable of photographing or recording from both iPhone cameras without the user's knowledge, all by exploiting the permissions granted by the user allowing access to the cameras.
Researcher Felix Krause, founder of Fastlane.Tools, created the watch.user concept app to show how far the camera permissions could be pushed, reports The Next Web. Once granted, Krause advises it is possible for an app to photograph and record from the cameras any time the app is in the foreground, without informing the user the images and video are being captured with flashes or other indicators.
Krause also claims it can then upload the images and video to an app's servers, including broadcasting a live feed from the iPhone itself. It is suggested that it is possible for a malicious developer to determine the user's location based on the image data, and to run facial recognition on still frames to find other photos of the user or to discover their identity.
A video demonstrating the test app's capabilities also shows it can also track the movements of the user's mouth, nose, eyes, and the entire face, and can even determine the mood of the user based on their facial expressions. Krause advises this part uses the Vision framework introduced in iOS 11, designed to allow developers to track a user's facial movements.
Notably, the issue is only a problem if the app is in the foreground, but Krause highlights that this could still cause privacy problems. For example, if a user decides to browse a social app while in the bathroom, and the app includes such code, it would be theoretically possible for it to record the user in a somewhat compromising position.
To answer criticism that people would never grant camera permissions, Krause warns many users will have already provided access to their image libraries and cameras to social networks and messaging apps, which could be updated with the malicious code.
Krause suggests worried users could protect themselves by using camera covers which block out the camera's view entirely, claimed by the researcher to be "the only real safe way." It is also suggested for users to revoke camera access for all apps, to always use the build-in camera app, and to use the image picker of each app to select the photograph to publish, or to use Copy and Paste to move the image to the application.
The researcher has disclosed the issue to Apple, at the same time as making some suggestions for how to avoid this from becoming a long-term issue. Suggestions include providing apps temporary access to the camera, and putting an icon in the status bar showing the camera is active and forcing the status bar to be visible when an app accesses the camera.
On the hardware side, Krause suggests adding an LED to the camera modules on both sides that cannot be kept off by sandboxed apps. This would be similar to the LED used by the MacBook, which lights up whenever the camera is in use, but it is doubtful Apple would make such a change to the iPhone's design, given the evolution of the top bezel to a notch in the iPhone X.
This is not the only potential security hole in iOS that Krause has discovered. Earlier this month, Krause disclosed another proof of concept app that displayed a popup similar to one used to enter an iTunes or Apple ID password, which could theoretically be used to steal a user's credentials.
 Malcolm Owen
Malcolm Owen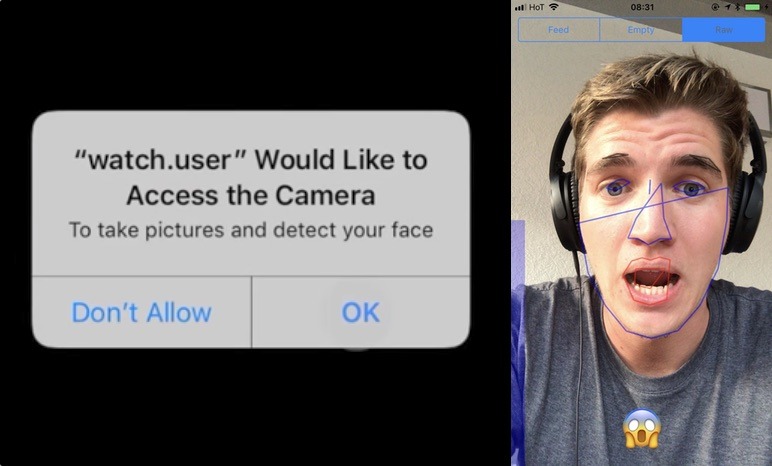







-m.jpg)






 Christine McKee
Christine McKee

 Sponsored Content
Sponsored Content

 Amber Neely
Amber Neely











103 Comments
A running app to which I gave permission can use the camera. SHOCKER !!
C'mon man! This always make me wonder why the Google team does not focus on fixing the huge list of Android flaws instead of getting so dedicated to helping other companies.
OMG!!!! Stop the presses... An App with permission to use the camera can.... OMG!!!! USE THE CAMERA!!!!.
Is this a serious news item?
Alert: Apps that have permission to use the microphone can listen to you!
Google engineer straining for IOS gnats while swallowing Android camels.