LIFX HomeKit bulbs appear to be storing Wi-Fi passwords unencrypted
A hardware hacker has revealed a trio of vulnerabilities in the popular LIFX HomeKit-enabled smart bulbs, that could expose a user's Wi-Fi password to somebody devoted to rooting through your trash.
Limited Results took a hacksaw to the LIFX Mini white smart bulb to gain direct access to the logic board of the bulb. After removing a copious amount of fireproof paste, the researcher was able to interface directly with the primary board.
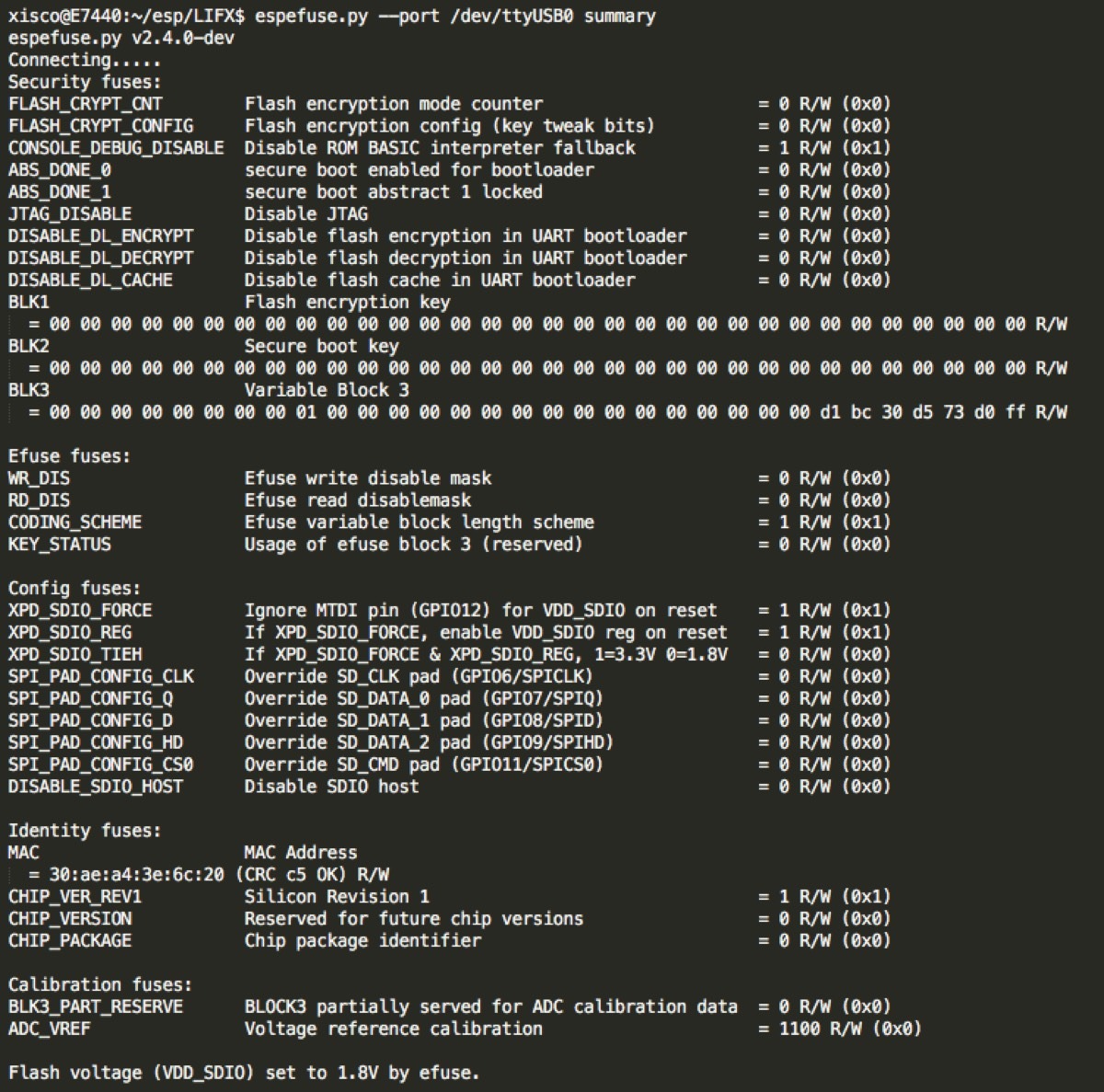
Once connected, and after a very short amount of time, the researcher was able to uncover a trio of flaws. Primarily, the Wi-Fi credentials are stored in plain text within the bulbs firmware. Using a hex editor, the WPA2 key can be found stored as ASCII encoded plain text.
There is no security on the firmware itself, with the researcher unable to locate secure boot features, flash encryption, or JTAG disabling — all leaving the device open to intrusion with physical access. Furthermore, both the RSA private key and the root certificate are present in the firmware and in plain text allowing for relatively easy extraction.
Anyone who has some basic electrical and programming knowledge, and has access to the bulb either functional or broken would be able to extract this information. It isn't a trivial extraction, but the fact that the credentials for the Wi-Fi network and RSA keys are being stored unencrypted is problematic from a security standpoint.
LIFX bulbs are arguably some of the best HomeKit bulbs on the market with a wide range of features unique from other bulbs. They also connect directly to Wi-Fi and don't rely on any gateway or hub to operate.
The bulb must be directly accessed — and destroyed — for this information to be gleaned. Then, hackers will only have access to your Wi-Fi credentials and still be unable to access or control your HomeKit devices.
Limited Results sent the information to LIFX in May of 2018, though they didn't receive a response until October. The security researcher then agreed to give LIFX 90 days before disclosing the vulnerability, which ended with Wednesday's public release.
It is still unknown whether LIFX has released an appropriate patch to address the vulnerabilities. AppleInsider has reached out to LIFX for comment, and will update when and if a response is received.
At this time AppleInsider suggests that you keep using any LIFX installation you may have as there does not appear to be a remote exploit at this time, but keep dead bulbs in your possession until LIFX issues guidance on the matter.
Update
LIFX has responded to AppleInsider stating how they addressed the concerns outlined in the original report. See our updated article for further details.
 Andrew O'Hara
Andrew O'Hara












 Mike Wuerthele
Mike Wuerthele
 Malcolm Owen
Malcolm Owen
 Chip Loder
Chip Loder

 William Gallagher
William Gallagher
 Christine McKee
Christine McKee
 Michael Stroup
Michael Stroup
 William Gallagher and Mike Wuerthele
William Gallagher and Mike Wuerthele






