Fake Adobe Flash malware seeks to disable Mac OS X anti-malware protection
According to security researchers at F-Secure, “Flashback.C†is potentially capable of disabling the auto-update component of Apple’s built-in XProtect anti-malware application by overwriting the system binary that checks for updates, XProtectUpdater. That functionality is apparently not yet active, however.
Once the malware is installed and delivered an external payload from malicious servers, the local system would be unable to obtain the latest anti-malware definitions and could subsequently be infected by other malicious programs the user installs without seeing the warnings that Mac OS X's XProtect feature is designed to present to users when they attempt to install malicious software that matches known threats, a definition list Apple maintains and which XProtectUpdater references daily.
Disabling system defenses is a common tactic employed by malware programs, the security firm notes, with built-in malware detection programs being “the first target on any computing platform.â€
Discovered in late September, the “Flashback.A†Trojan poses as an Adobe Flash installer in an attempt to trick Mac OS X users into installing the program in order to access Flash-based content on the web. The trojan primarily targets Mac OS X Lion users, since Apple’s latest desktop operating system doesn’t come with Flash preinstalled.
“Flashback.C†similarly masquerades as a Flash installer, displaying the same visual elements during the installation process (shown below) in an attempt to convince users they are installing a genuine copy of Flash. Once installed, “Flashback.C†first checks to see if the user is running "Little Snitch," a firewall program that could alert the user of its actions. If it is found to be installed, the trojan deletes itself.
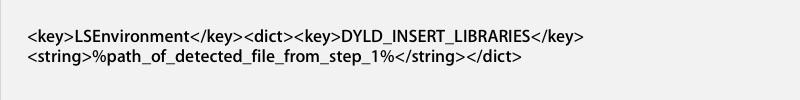
If it doesn't find Little Snitch, the malware then tries to connect to a remote host in China in order to obtain other installation files and configurations. F-Secure notes that "the remote host is up but it does not [yet] push anything." If and when the site becomes active, it could deliver a payload that the trojan could use to disable the system's auto-updater, using Safari or Firefox to deliver the malicious code via an LSEnvironment variable that loads when the browser restarts.
In order to prevent a potential infection with “Flashback†Trojans, Mac users are advised to obtain their copy of Adobe Flash Player directly from Adobe’s official website and to disable the "Open 'safe' files after downloading" option in Apple's Safari browser to avoid automatically running files downloaded from the Internet.
Users should also refuse to enter their local account password at any prompt to do so unless they understand why it is required.
In case an infection has occurred, F-Secure provides instructions for removing the Trojan: Scan the whole system and take note of the detected files, then remove the plist entry:
From:
/Applications/Safari.app/Contents/Info.plist
/Applications/Firefox.app/Contents/Info.plist
Delete all detected files
At this time there is not yet a fix from Apple that would automatically flag the new Trojan version as malware when it is being installing on Mac systems, but the trojan is not actually working yet either, so users shouldn't be afraid they are already infected unless they are in the process of installing Adobe Flash from a non-legitimate source.
The evolutionary attempts to create new Mac OS X malware highlight the problems with allowing users to install software from any source, something that has plagued Windows and Mac users with the threat of user-installed malware, and something that has recently exploded as a growing concern among Android users. iOS users are protected from such malware attempts by the security of the App Store, and Apple's Mac App Store affords similar security to its desktop users.
However, web browser plugins such as Adobe Flash, along with other software that plugs into the system on a low level, are not possible to deliver through the App Store under Apple's current policies. Somewhat ironically, users can install the Flash Block app from the Mac App Store, which for 99 cents, offers to temporarily kill active Flash content to conserve battery life, or to block Flash entirely.
 Chris Smith and Daniel Eran Dilger
Chris Smith and Daniel Eran Dilger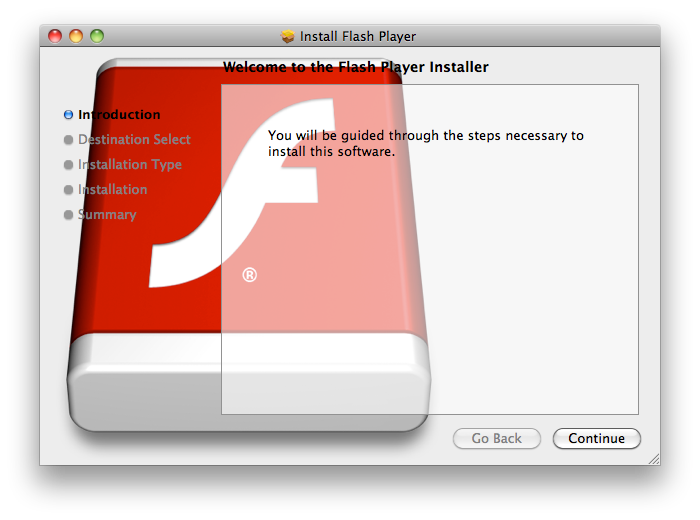











 Malcolm Owen
Malcolm Owen
 Chip Loder
Chip Loder

 William Gallagher
William Gallagher
 Christine McKee
Christine McKee
 Michael Stroup
Michael Stroup









