Among the flurry of patents granted to Apple on Tuesday, an interesting invention regarding iPhone security was discovered, with the property describing various methods to protect sensitive data if an unauthorized user gets hold of the device.
Illustration of gathered information log, including unauthorized user data. | Source: USPTO
U.S. Patent No. 8,289,130 for "Systems and methods for identifying unauthorized users of an electronic device" offers a unique security solution to the ever-present problem of having one's iPhone lost or stolen.
The patent's innocuous language starts out by saying, "This is generally directed to identifying unauthorized users of an electronic device," but goes far beyond any identification technology currently available in Apple's handset. For example, one embodiment of the invention calls for heartbeat monitoring, which can be used to determine whether the person holding an iPhone is its owner.
From the patent abstract:
In some embodiments, an unauthorized user of the electronic device can be detected by identifying particular activities that may indicate suspicious behavior. In some embodiments, an unauthorized user can be detected by comparing the identity of the current user to the identity of the owner of the electronic device. When an unauthorized user is detected, various safety measures can be taken.
The patent essentially covers three main operations: the detection of an unauthorized user; the gathering of information of an unauthorized user; and the transmission of an alert notification to the electronic device's owner containing said information.
As mentioned above, a person's heartbeat can be used to determined whether he or she is the owner of a device, though more conventional methods are also described, such as taking a photograph or matching voice recordings. Perhaps most effective are the patent's other embodiments in which an unauthorized user is identified through a number of actions. For example, "entering an incorrect password a predetermined number of times in a row, hacking of the electronic device, jailbreaking of the electronic device, unlocking of the electronic device, removing a SIM card from the electronic device, or moving a predetermined distance away from a synced device" can all be used as means of detection.
When a non-owner is identified, the device can enter an information gathering mode in which location, photographs, voice recordings, screenshots, keylogs, and internet usage are stored. Another option is to restrict the phone's functions and erase sensitive information when an unauthorized user takes control of the device.
Finally, an alert is sent to a "responsible party," such as the device owner or police, containing a predetermined message like "Warning, your electronic device may have been stolen." In addition, the alert, sent via text, email, instant message, or over the internet, can contain the information the device gathered when in the hands of the unauthorized user.
Detection and security flowchart.In some embodiments, near field communications, or NFC, can be employed to pair the handset with a key fob or similar device. If the phone moves far enough away from the key fob, it will issue a warning which will turn into a formal alert if the device moves a substantial distance.
As with most Apple patents, it is unclear if the technology will be deployed in an upcoming product, however recent additions to iOS like Find My iPhone illustrate the company's focus on device security.
 Mikey Campbell
Mikey Campbell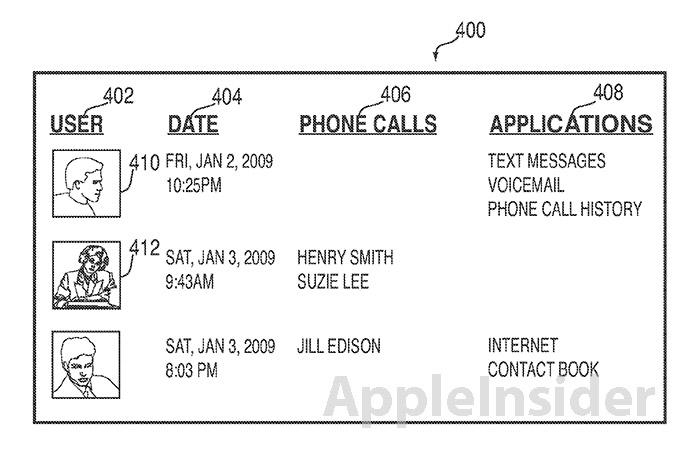







-m.jpg)






 Wesley Hilliard
Wesley Hilliard
 Malcolm Owen
Malcolm Owen
 Andrew Orr
Andrew Orr
 William Gallagher
William Gallagher
 Sponsored Content
Sponsored Content
 Christine McKee
Christine McKee

 Thomas Sibilly
Thomas Sibilly







5 Comments
Breaking news! New, never been done before, feature coming to the Galaxy S4. It detects your heartbeat to warn you if your phone is being used by an unauthorized user.
Is a heartbeat signature as specific as a fingerprint? Maybe we can login to accounts via heartbeat soon!
A system to recognise you by a unique heartbeat signature?
I'm going to stick my neck out and say this won't show up in the iPhone5s.
Interesting that Apple sees jail-breaking as an indicator of a stolen phone. Wonder how that's going to play out...
Gee, if only they had some way of detecting users touching the device, say by way of the acquisition of a company that made a new kind of fingerprint scanner that can detect who's fingers are on the screen.
... Interesting that Apple sees jail-breaking as an indicator of a stolen phone. Wonder how that's going to play out...
Don't get too paranoid here. Obviously, jail-breaking would be an invaluable factor to monitor in any kind of corporate situation or anywhere the device is "managed." This would account for a huge number of phones.
It's also patently obvious that any attempt at security is completely nullified if the end user takes complete control of the phone (jail-breaking), as you then have no idea what they can or cannot do.
It's not a conspiracy, it's just common sense. Jailbreaking is a definite security risk to any entity seeking to secure the iPhone.
No one concerned with the security of their iPhone (even an individual), would jailbreak it without realising that at that point, they alone are now responsible for security.
No security protocol of any worth can ever be put in place with a giant loophole like jail-breaking being allowed at the same time.