Just one day after Apple rolled out the latest iOS 6.1.3, which patched an iPhone lock screen security flaw, a similar bug has been discovered that replicates the bypass albeit in a more involved and limited process.
The flaw, found on Wednesday by YouTube user "videosdebarraquito," allows unauthorized users access a locked handset's address book and photos by ejecting the SIM card while using voice control to make a call.
It appears that the flaw is limited to iPhones without Siri support, as AppleInsider was not able to reproduce the behavior on an iPhone 5.
As seen in the demonstration video, the process is somewhat more involved than simply dialing and canceling an emergency call. In order to reproduce the bug, a malicious user must be using an iPhone incompatible with Siri, which has Voice Control activated, and have a paper clip or SIM card extraction tool. By holding down the Home button when an iPhone is locked, a user can request a number to be dialed. When the Voice Control system initiates the call, the removal of the SIM card tray, and thus the SIM card, defaults the phone app back to the dialing screen. From there, contacts, photos and recent call information can be accessed.
When Apple released iOS 6.1.3 on Tuesday, the company patched a similar lock screen bug that bypassed the lock screen security code to give low-level access to contact information and other assets available from the phone app.
While Tuesday's discovery is likely to be fixed in an upcoming iOS update, for now users can simply turn off "Voice Control" in the Settings menu to disallow unwanted iPhone access.
 AppleInsider Staff
AppleInsider Staff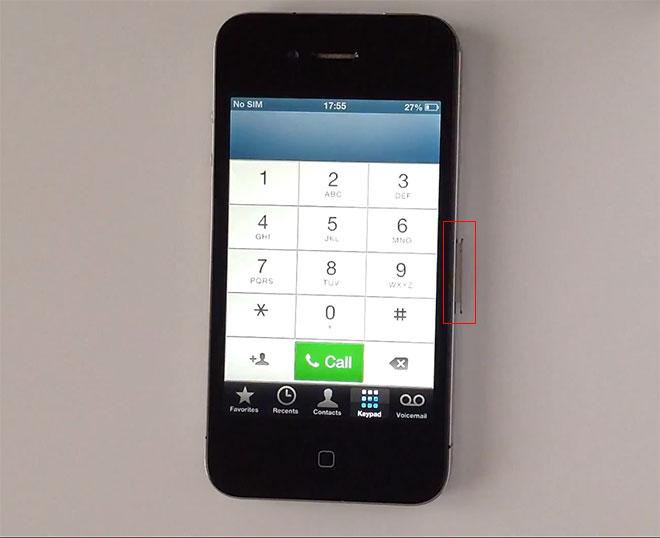









 Chip Loder
Chip Loder
 Christine McKee
Christine McKee
 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher


 Andrew Orr
Andrew Orr





32 Comments
This is getting a little ridiculous...
[quote name="ombra2105" url="/t/156569/new-iphone-lock-screen-flaw-found-in-ios-6-1-3-grants-access-to-address-book-and-photos#post_2297486"]This is getting a little ridiculous...[/quote] To be fair, who actually uses Voice Control anyway?
…by ejecting the SIM card while using voice control to make a call.
This is probably the stupidest exploit I've ever heard of. This is like Woz getting the students to make weird poses to keep the TV running.
Ousting Scott wasn't such a great idea...
Ousting Scott wasn't such a great idea...
Implying he's somehow leaking all these exploits or that he personally would have been able to prevent them?