New documents revealed on Monday show the U.S. National Security Agency has the capability of deploying software implants on Apple's iPhone that grants remote access to on-board assets like SMS messages, location data and microphone audio.
In a talk at the Chaos Communications Congress in Germany, security researcher Jacob Appelbaum summarized the NSA's iPhone-targeting spyware program called "DROPOUTJEEP" as part of a broader discussion dealing with the agency's controversial electronic surveillance initiative, reports The Daily Dot.
As it pertains to Apple's smartphone, the findings — concurrently published by German magazine Der Spiegel — are limited to a single top secret document dating back to 2008. The page details DROPOUTJEEP's basic operational structure and capabilities, which include the interception of SMS messages, access to on-board data, microphone activation and approximate positioning via cell tower location. All communication takes place covertly over SMS or GPRS data protocols.
While a startling revelation, DROPOUTJEEP's proliferation within the iPhone community is largely unknown. The NSA boasts a 100 percent success rate for implanting the spyware on iOS devices, Appelbaum said, but the document suggests physical contact with a target phone is required to implant the surreptitious software. In practice, the method is likely similar to a consumer jailbreak looking for root device access.
To this point, Appelbaum alludes to complicit involvement by Apple, but tempers his — so far baseless — allegation with "I can't really prove it."
I don't really believe that Apple didn't help them," Appelbaum said. "I can't really prove it yet, but [the NSA] literally claim that anytime they target an iOS device, that it will succeed for implantation. Either they have a huge collection of exploits that work against Apple products, meaning that they are hoarding information about critical systems that American companies produce and sabotaging them, or Apple sabotaged it themselves. Not sure which one it is. I'd like to believe that since Apple didn't join the PRISM program until after Steve Jobs died, that maybe it's just that they write [expletive redacted] software. We know that's true.
Der Spiegel asserts specialized NSA Tailored Access Operations (TAO) teams intercept incoming device shipments, carefully open packages and install spyware before sending the "bugged" units along to end users.
A more efficient delivery mechanism is remote installation, something the NSA said was being "pursued for future release." Once again, it is unknown if the agency moved forward with such a system in the intervening five years since the document was first issued.
Video of Appelbaum's talk with iPhone discussion starting at around 44:30:
 Mikey Campbell
Mikey Campbell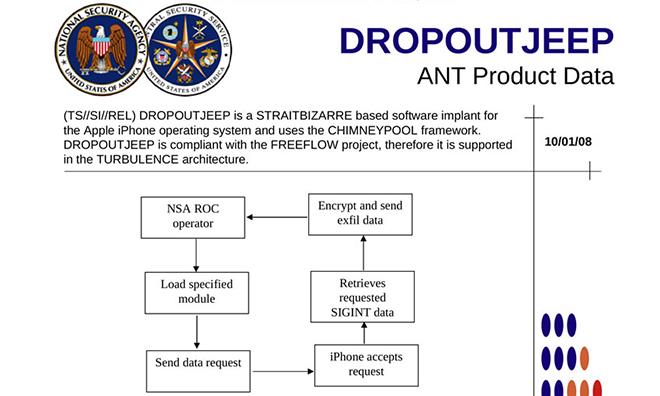







-m.jpg)






 Wesley Hilliard
Wesley Hilliard
 Malcolm Owen
Malcolm Owen
 Andrew Orr
Andrew Orr
 William Gallagher
William Gallagher
 Sponsored Content
Sponsored Content
 Christine McKee
Christine McKee

 Thomas Sibilly
Thomas Sibilly







86 Comments
Der Spiegel asserts specialized NSA Tailored Access Operations (TAO) teams intercept incoming device shipments, carefully open packages and install spyware before sending the bugged units along to end users.
A more efficient delivery mechanism is remote installation, something the NSA said is being "pursued for future release." Once again, it is unknown if the agency moved forward with such a system in the intervening five years since the document was first issued.
Video of Appelbaum's talk with iPhone discussion starting at around 44:30:
Why is half the article crossed out?
My fucking god, to what ends?
What a worm: "I don't really believe that Apple didn't help them," Appelbaum said. You have no proof of anything. You can't prove a negative. Can't wait for the headlines: Apple allegedly works with NSA to hack iPhones. Then in paragraph 7: we have no proof.
Apple is erasing discussions on this topic at their support forum, right now the whole forum is shut down for a complete cleanup. [IMG ALT=""]http://forums.appleinsider.com/content/type/61/id/36735/width/350/height/700[/IMG]
[quote name="DarkLite" url="/t/161398/nsa-worked-on-iphone-spyware-to-remotely-monitor-users-leaked-documents-show#post_2451687"] Why is half the article crossed out? [/quote] I'd say you are using either the HTML or markup strikethrough in your quoted reply. If that was in the originally posted article it's no there now.