Apple has introduced a number of features designed to protect users from malware in OS X, but these tools occasionally go too far when trying to save people from themselves.
TL;DR:If you have an app from an unidentified developer and you're sure the app is safe, you can force it to run by right clicking (or command-clicking) the app and choosing "Open" from the context menu.
OS X's Gatekeeper feature — introduced with OS X Mountain Lion — places restrictions on which apps can be run on a Mac based on the avenue through which the apps were acquired. There are three tiers: apps which are distributed by registered developers through the Mac App Store, apps which are distributed by registered developers outside of the Mac App Store, and apps which are not made by registered developers.
Gatekeeper distinguishes between the latter two based, broadly, on whether the app has been signed with a legitimate Apple-issued signing key.
By default, Gatekeeper is configured to allow apps from the Mac App Store and from registered developers. Users can make this more or less strict:
- Open System Preferences
- Open the "Security & Privacy" pane
- Select the "General" tab
- Click the lock icon in the lower-left corner and enter an administrative username and password
- Select one of the three available levels under "Allow apps downloaded from:" and close the preference pane
Unless you choose to allow apps downloaded from anywhere, OS X will warn you against opening apps that aren't signed: you'll see a dialog box that says "
If you're sure the app is safe, you don't need to alter your security preferences to open it — there's a faster workaround.
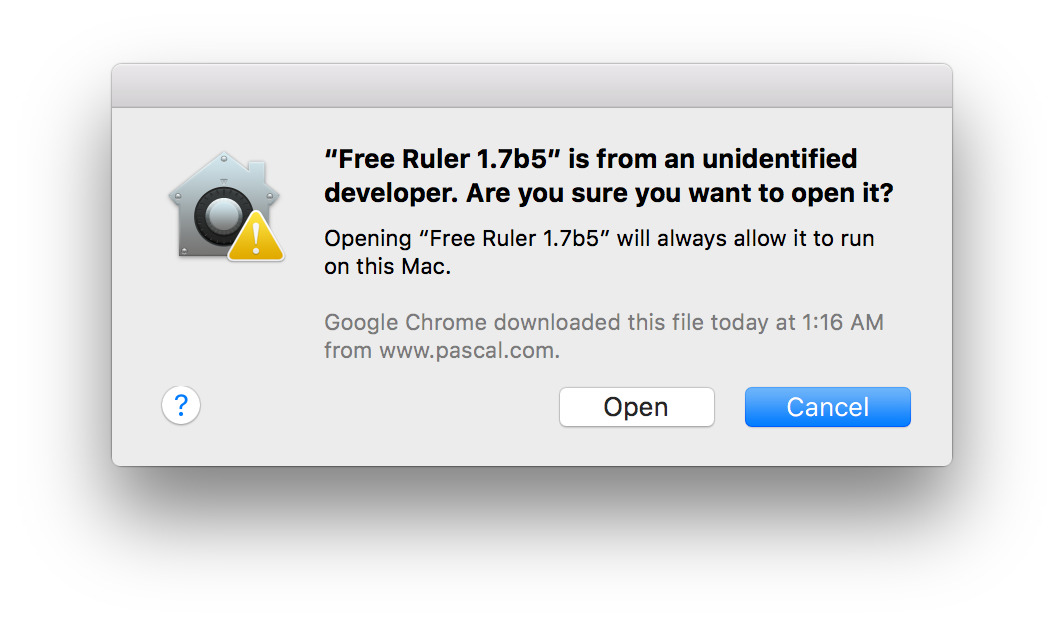
Right click (or command-click) on the app and select "Open" from the context menu. This will present a slightly different dialog box: this time, you'll be presented with an "Open" button that will let you force OS X to run the app.
Remember: only do this if you're sure the app is from a reputable developer and has not been tampered with.
 AppleInsider Staff
AppleInsider Staff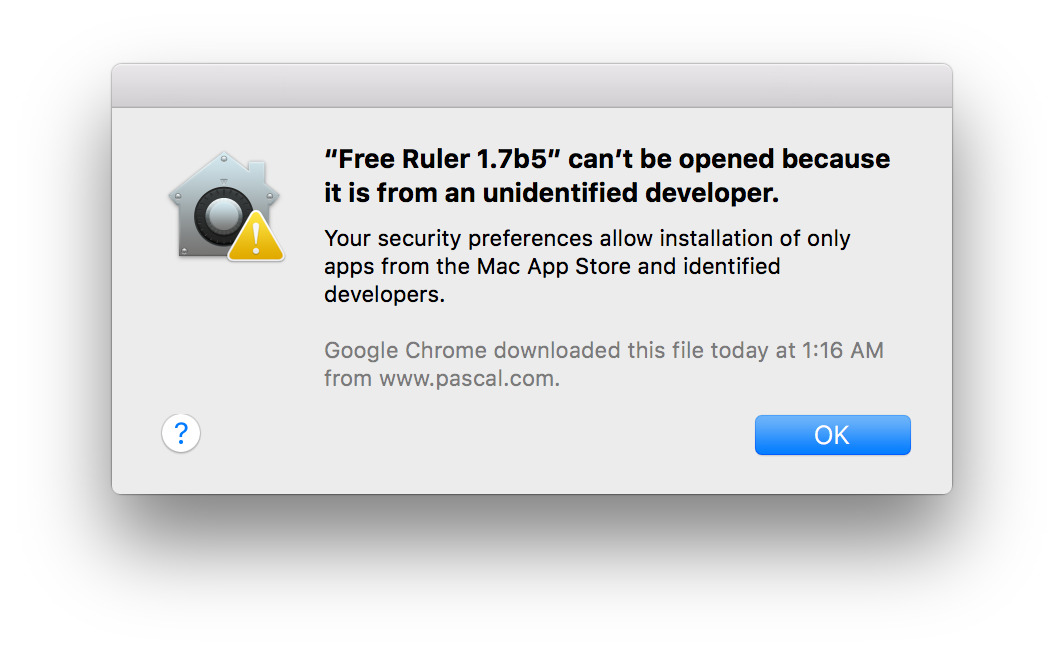







-m.jpg)






 Wesley Hilliard
Wesley Hilliard
 Marko Zivkovic
Marko Zivkovic

 Malcolm Owen
Malcolm Owen

 Amber Neely
Amber Neely











12 Comments
Gatekeeper does not "go too far" in protecting users from themselves. If a user doesn't understand how Gatekeeper works then maybe they shouldn't be messing around with software of unknown origin. It's a matter of education. The user can bypass Gatekeeper if educated about it. How many "do you really want to do this" flags are required to finally let a user brick their system voluntarily?
I think you meant to say Right click (or CONTROL-click), instead of "Right click (or command-click)"
Gatekeeper "goes too far"? Hardly.
An effective security strategy is a multilayered one, and Gatekeeper is just one part of an overall mindset that any computer user must adopt in order to avoid inadvertently installing malware, or just simply junk software. Gatekeeper is also easily bypassed by control-clicking the app (no, command-click is incorrect). A two-finger tap works also. That will cause the dialog box in the illustration to appear. It's incumbent upon the user to read, comprehend, and act upon what it says.
If the user doesn't do that, well, they get what's coming to them. You can't fix stupid.
You can't really rely upon that either. Even reputable developers have had their distribution sites hacked.
I can see why the person who wrote this idiot's guide to installing malware didn't sign their name to it. (to clarify: I have no problem with people using software that is not offered on the Mac App Store, I use some myself. This article, though, does nothing to help newbs distinguish legit non-MAS stuff from dangerous trojans, and in doing that encourages users who don't know what they're doing to install anything they see that sounds interesting/tempting -- a sure path to malware.)