Newly-published guidelines could lead Apple and other companies to find an alternative to SMS for two-factor authentication, such as dedicated apps, according to reports.
The U.S. National Institute of Standards and Technology has published a public preview of upcoming documents which specifically recommend against using SMS as an "out of band authenticator," TechCrunch noted. Such systems — in Apple's case used to authenticate Apple IDs — can send a verification code to a smartphone, which then has to be entered on the original device a person is trying to use.
The problem, according to the Institute, is that people can use virtual phone numbers in place of real ones, undermining the security of the process. For the time moment the NIST is continuing to accept SMS for two-factor authentication as long as a number is linked to a real cellular network, but future guidelines will deprecate SMS entirely.
Apple's system is optional, and not strictly dependent on phone numbers. Without one, though, people must have a second Apple device handy to display verification codes.
To keep two-factor authentication practical while meeting NIST standards, Apple would likely have to develop authenticator apps for other platforms, such as Android and Windows. Companies like Google and Valve already offer multi-platform apps for their services.
 Roger Fingas
Roger Fingas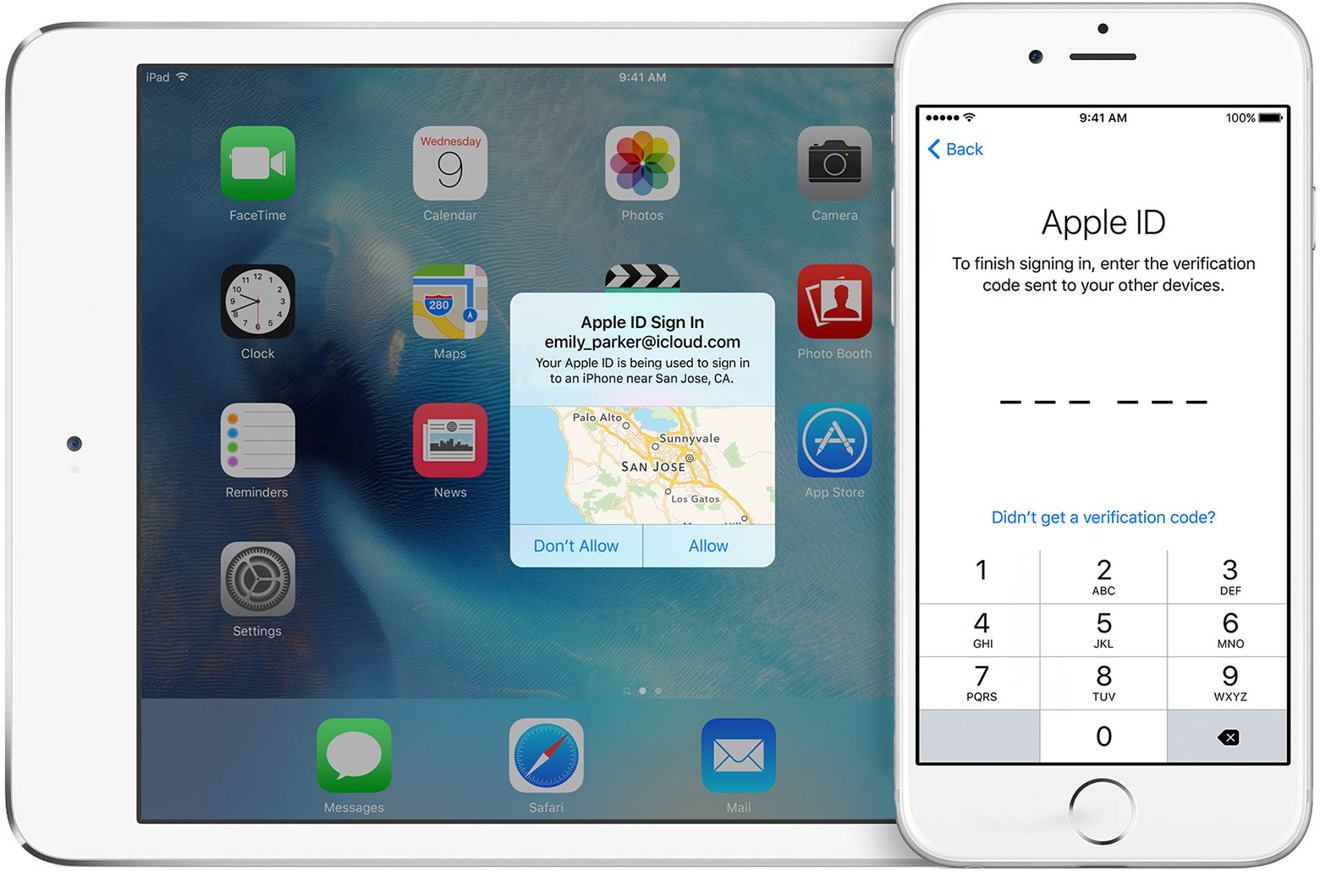






 Oliver Haslam
Oliver Haslam
 William Gallagher
William Gallagher
 Christine McKee
Christine McKee
 Sponsored Content
Sponsored Content

 Malcolm Owen
Malcolm Owen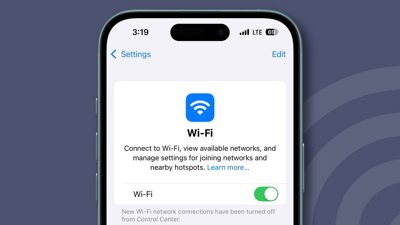
 Andrew Orr
Andrew Orr








17 Comments
"The problem, according to the Institute, is that people can use virtual phone numbers in place of real ones, undermining the security of the process. "
Are they talking about people creating fake numbers to attach to their own accounts to receive the 2FA SMS messages?
The real problem with email account security is the opportunity for intruders to mess around with the accounts. EXAMPLE: My wife has a very unique email address -- *********@me.com -- she has owned it from day one when @me.com accounts were made available by Apple. She has never once requested to Apple to change her password, or report she forgot her password, etc. Yet over the past 3 years she has weekly had individuals making these requests thus causing her account to be locked by Apple and requiring us to wait 8 hours later before we can unlock the account. All Apple would have to do to stop this merry-go-round would be to require these phony requests to be authenticated with a text message code or email message request for confirmation that the owner actually was the one making the request (or maybe there's an even better way). It's really nuts. Apple tech's response to us several times has been, "just give up the email address and go to something not so enticing to thieves." Like it's our fault we were early adopters and got a prime email address. Come on Apple!!!!
I'm confused...Apple doesn't use SMS now.
It sends encrypted push notifications to your trusted devices. At least that's how it works for me. Am I missing something?