Just prior to a hacker's conference, a participant has revealed that the iPhone 5s Secure Enclave has been hacked, and the decryption key for it has been revealed. However, at present, there is nothing for iPhone users to immediately worry about.
First spotted by Redmond Pie on Wednesday, Twitter user "xerub" posted the information, and an extraction tool for the Secure Enclave firmware, in advance of the Singapore Hack in the Box conference.
The tool and hack is not for the inexperienced. The outputs of the tool are binaries of the kernel and related software regulating the communications between the Touch ID sensor and Secure Enclave — but not any information transmitted presently or in the past between the Touch ID sensor and the Secure Enclave.
key is fully grown https://t.co/MwN4kb9SQI use https://t.co/I9fLo5Iglh to decrypt and https://t.co/og6tiJHbCu to process
— ~ (@xerub) August 16, 2017
The exposure of how to extract the encryption key from an iPhone 5s does not mean that the device is no longer secure. However, it does mean that people angling to make exploits for the device are able to examine the Secure Enclave firmware on the device in more detail than previously possible.
At present, there is no known exploit utilizing the tool, or the gleaned data, and it is not clear how one would even be produced or installed on a target device. Any exploit developed with the tool would be specific to the iPhone 5s, and require physical access to the device to load custom firmware as well.
Apple's Secure Enclave is in Apple's A7 processor and later and provides all cryptographic operations for data protection in iOS devices. The Secure Enclave utilizes its own secure boot and can be updated using a personalized software update process that is separate from the application processor — which is how any exploit would have to be installed, one device at a time.
The Secure Enclave is responsible for processing fingerprint data from the Touch ID sensor, determining if there is a match against registered fingerprints, and then enabling access. Each pairing of the Touch ID uses the shared encryption key, and a random number to generate that session's full encryption key.
 Mike Wuerthele
Mike Wuerthele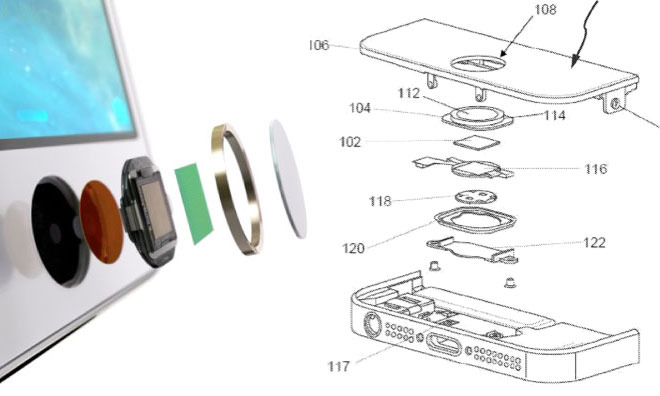







-m.jpg)






 Charles Martin
Charles Martin
 Christine McKee
Christine McKee
 Wesley Hilliard
Wesley Hilliard
 Malcolm Owen
Malcolm Owen
 Andrew Orr
Andrew Orr
 William Gallagher
William Gallagher
 Sponsored Content
Sponsored Content







23 Comments
As a stock analyst, I am telling all my clients to sell their APPL positions immediately. I also suspect that this will be the demise of Apple; this breach will more than likely cause the stock price to decrease at least 54% within the next 1 to 14 years.