Apple on Wednesday released a special security update for macOS High Sierra, solving a recently uncovered flaw which would let people gain root access without entering a password.
The patch, Security Update 2017-001, should be available through the Updates tab in the Mac App Store. After installation, the build number of High Sierra will be 17B1002.
Apple notes that if people require a root user account on their Mac, they can create one and assign a password through System Preferences.
The vulnerability was first exposed on Tuesday. Within hours, Apple was already promising an update, though it didn't provide an exact timeline.
Apple also issued a statement to The Loop on the misstep:
Security is a top priority for every Apple product, and regrettably we stumbled with this release of macOS.When our security engineers became aware of the issue Tuesday afternoon, we immediately began working on an update that closes the security hole. This morning, as of 8 a.m., the update is available for download, and starting later today it will be automatically installed on all systems running the latest version (10.13.1) of macOS High Sierra.
We greatly regret this error and we apologize to all Mac users, both for releasing with this vulnerability and for the concern it has caused. Our customers deserve better. We are auditing our development processes to help prevent this from happening again.
 Roger Fingas
Roger Fingas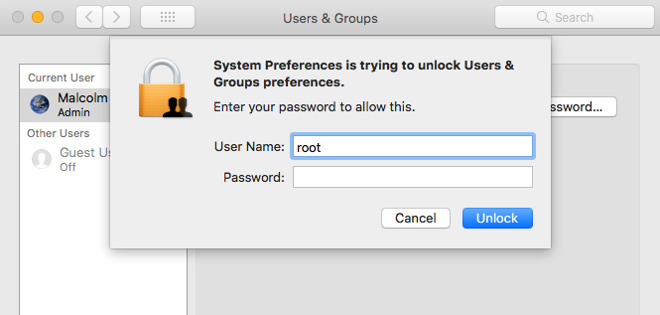








 Brian Patterson
Brian Patterson
 Charles Martin
Charles Martin


 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher
 Christine McKee
Christine McKee
 Marko Zivkovic
Marko Zivkovic









55 Comments
That was fast! Well done Apple.
Unless already baked in, this security update patch is not available if using the current 10.13.2 Beta (17C83a) build.
Ok to use black as the password user root?
I'm impressed. I wouldn't have thought it possible to push out of fix to users within (essentially) 24 hours of being notified of the vulnerability. Perhaps you have to be in IT and have some experience with release management to appreciate how exceptional this type of turnaround is. More than a people at 1 Infinite Loop and/or Apple Park didn't get any sleep last night.