Quick Look is a marquee feature Mac users rely on to easily preview files without opening a dedicated app, but the years-old tool could potentially reveal sensitive information on encrypted drives.
The security hole, which has assumedly been present in Quick Look since the feature rolled out more than a decade ago, was detailed earlier this month in a blog post by security researcher Wojciech Regula. Patrick Wardle, with Regula's assistance, provided an in-depth explanation of the flaw in a blog entry last week that was picked up by The Hacker News on Monday.
As Regula notes, Apple's Quick Look mechanism generates and caches thumbnails of files, images, folders and other data for fast and easy access by macOS. This allows Mac users to quickly preview said information with the tap of the space bar. Instead of relying on a dedicated app, such as Acrobat for PDFs, macOS is able to provide a "quick look" at the file using OS assets.
The problem, which was initially discussed some eight years ago, is Quick Look's file handling practices. Apple's feature stores thumbnail caches on an unencrypted drive, meaning snippets of originating files, even those contained in encrypted containers, can be exposed to those who know where to look.
"This means that all photos that you have previewed using space (or QuickLook cached them independently) are stored in that directory as a miniature and its path," Regula writes.
To verify his claims, Regula created a proof of concept in which two images were saved in two separate encrypted containers, one created with VeraCrypt and another with macOS Encrypted HFS+/APFS. The researcher was able to find both images and their paths with a simple command, which in turn granted access to a miniature version of the original files.
Wardle adds that Quick Look's caching function extends to attached USB drives, with thumbnails stored on the host computer's boot drive. He further argued that while the Quick Look flaw does not reveal the entire contents of a given file, what it does provide could prove useful to nefarious actors or law enforcement agencies.
That said, it would be relatively simple for Apple to patch the issue. As Wardle notes, Apple could relegate Quick Look previews to files located outside encrypted containers or, alternatively, flush thumbnail caches when a volume is unmounted.
Without an official fix, users concerned about exposing potentially sensitive data can manually delete a Quick Look cache when a container is unmounted by using the qlmanage utility.
 Mikey Campbell
Mikey Campbell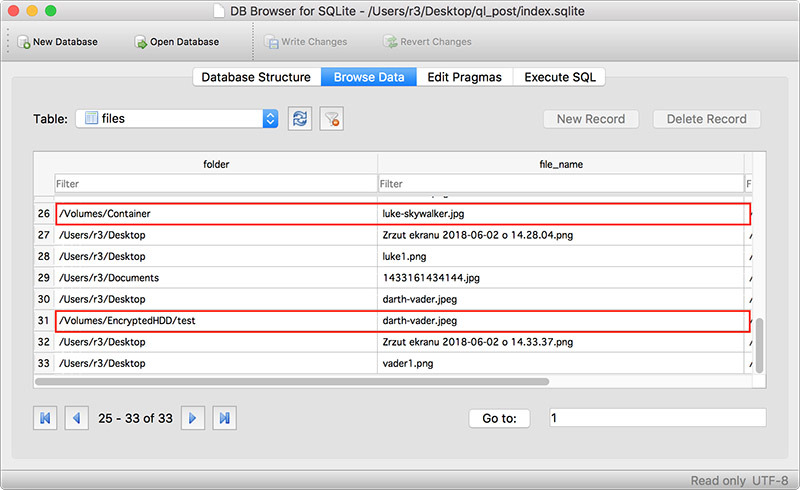












 Oliver Haslam
Oliver Haslam
 William Gallagher
William Gallagher
 Christine McKee
Christine McKee
 Sponsored Content
Sponsored Content

 Malcolm Owen
Malcolm Owen
 Andrew Orr
Andrew Orr







21 Comments
Apple can Just patch this. All software has bugs. Apple builds in security from the ground up.
Space bar always seemed like a bad idea.
Nice.
Should this one get flaw of the year, or flaw of the decade?
(I always kind of wondered how well behaved things like Spotlight and QuickLook were when it came to their caching/indexing... now we know.)
Complain all you want but had anyone else noticed it over the years? If not, then I doubt it was ever used. If it was I’m sure someone would have blabbed about it before this. Of course the researcher didn’t include the command to find the files.
A legitimate oops, and easily fixed.
Bravo security researcher!