With iOS 11.4.1, Apple has quietly turned on USB Restricted Mode, a feature designed to make it harder for hackers — as well as spy and law enforcement agencies — to gain physical access to iPhones and iPads.
A new "USB Accessories" toggle is present under the "Face ID/Touch ID & Passcode" menu. The option is off by default, meaning than if a device has been locked for an hour or more, iOS won't allow physical data connections.
"At Apple, we put the customer at the center of everything we design. We're constantly strengthening the security protections in every Apple product to help customers defend against hackers, identity thieves and intrusions into their personal data," the company said in an earlier statement to AppleInsider about the feature's planned inclusion in iOS 12. "We have the greatest respect for law enforcement, and we don't design our security improvements to frustrate their efforts to do their jobs."
Although Apple has denied any intention at interfering with law enforcement, USB Restricted Mode will inevitably make work harder for police departments and third-party forensics firms like Cellebrite and GrayShift, at least until they develop new tools or successfully pressure governments into mandating backdoors.
Cellebrite in particular is believed to be the firm the FBI used to crack the iPhone 5c of San Bernardino shooter Syed Rizwan Farook, allowing both Apple and the U.S. Department of Justice to avoid a protracted battle over whether the former could be forced to code a backdoor into iOS.
A number of officials in U.S. spy and law enforcement agencies have complained that internet communications are "going dark," thanks to the growing use of end-to-end encryption, which prevents even the companies employing it from intercepting data. Some politicians have called for backdoors, though nothing has come of those efforts so far.
Apple and other encryption supporters have countered by arguing that privacy is a right, and that any backdoor is bound to be discovered by malicious entities or abused even by well-meaning ones, given mass surveillance efforts by the FBI and NSA.
 Roger Fingas
Roger Fingas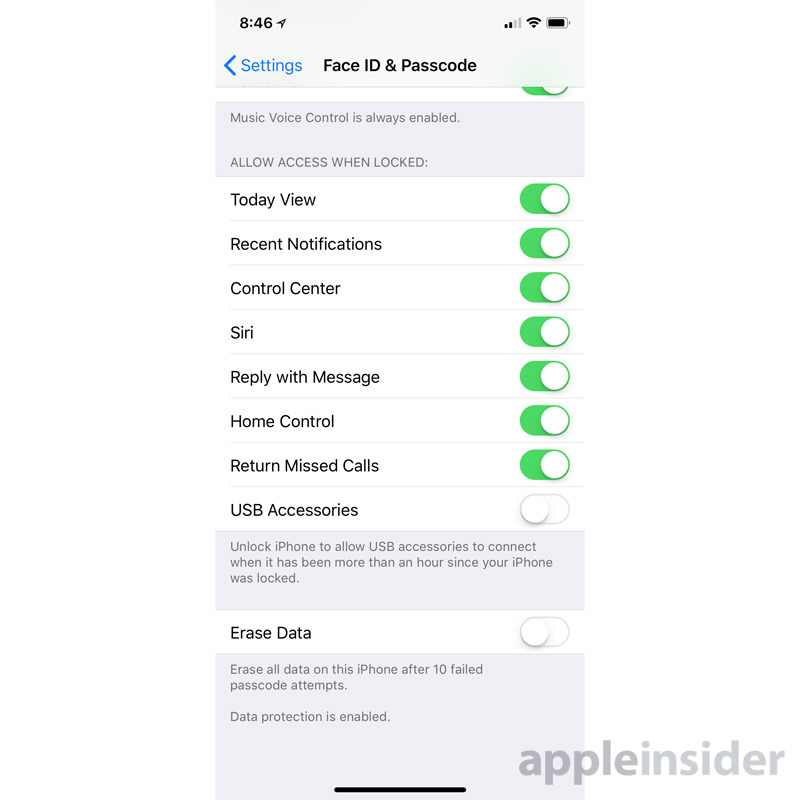







-m.jpg)






 Andrew Orr
Andrew Orr
 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher

 Wesley Hilliard
Wesley Hilliard






-m.jpg)




18 Comments
Good for Apple.
Thanks Apple.
Excellent Apple!
one small change, the word BE is missing from the following paragraph.
Cellebrite in particular is believed to the firm the FBI used to crack the iPhone 5c of San Bernardino shooter Syed Rizwan Farook
It should be:
Cellebrite in particular is believed to “BE” the firm the FBI used to crack the iPhone 5c of San Bernardino shooter Syed Rizwan Farook