Apple is seemingly attempting to combat the problem of phone scammers and other types of nuisance callers, by coming up with a method to detect if the inbound call is using a spoofed number and warning the recipient before they answer.
Nuisance calls are continuing to be a major problem for phone users around the world, with telemarketing spam, scams, and other types of "robocalls" bombarding people with calls and messages they do not want to see. While there are ways to block regularly-received nuisance calls, such as with block lists, the callers have ways to work around the restrictions.
One way is to spoof phone numbers, namely to make the call seem like it is coming from a different number. Spoofing allows calls to pass through blocking systems if the number is not on the list, as well as preventing the user from seeing the actual source of the call via caller ID before answering, something which can even make them more likely to answer if it's supposedly from a local area code, a trusted company, or a government agency.
Hiding the number behind another also reduces the possibility of a scammer from being reported to the authorities. It also means that irate callers cannot phone the scammer or telemarketer back to complain.
Published on Thursday by the U.S. Patent and Trademark Office, Apple's patent application for "Detection of spoofed call information" proposes a system where an iPhone or other mobile device could perform checks on a call to ascertain if it is genuine, then either warn the user of the problematic call or prevent it from disturbing the phone user at all.
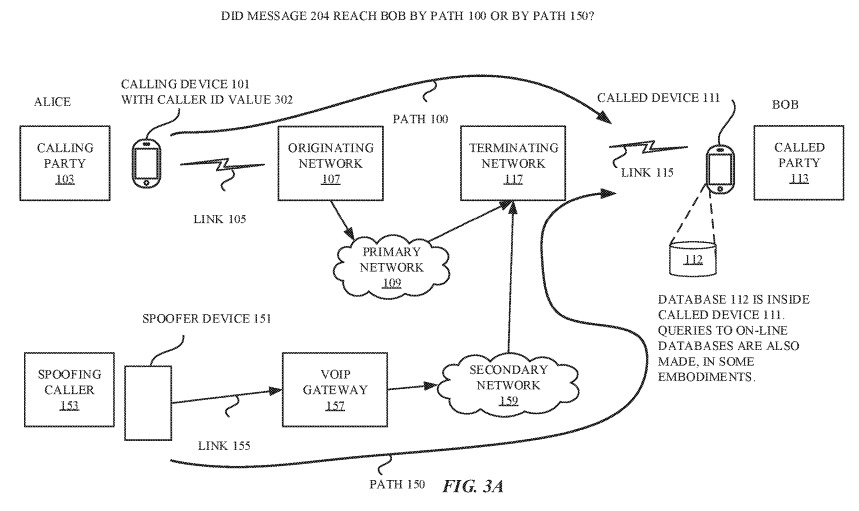
In some cases when a call is made, a session initiation protocol (SIP) invite is sent along between phone networks to the user's device. The SIP invite can contain a number of elements, with headers providing data meant to establish the call, such as speech codec information, network equipment identifiers, 3GPP VoLTE protocol information, server identifiers, and other elements.
While the spoofing caller can fill in some of the SIP invite fields, some are populated or overwritten by network servers as it travels. This automatically added or altered information constitutes a signature for that network, which could be used to compare with other existing call signatures to determine if the call itself is legitimate.
For example, the speech codec information could state the call is from a network's "internet multimedia subsystem" rather than VOIP, which would lean the device towards the call being legitimate due to VOIP being favored by nuisance callers. Identifiers could also be checked against a list of similar already-known identifiers, to confirm the call is passing through the correct phone networks and servers for the claimed origination point.
The system could also be used to determine if the spoofer is passing the call through a forwarding device, which is connected to a legitimate network and sends the SIP invite itself, potentially through a number from the user's address book. Using VIA headers, the device can check the number against the address book of the user, or a previously-established list, to verify the call is coming from the correct identified source.
In cases where the phone believes there to be too many discrepancies in the SIP invite, it can refer the "call record" to a database of other call records online. The database includes templates for different types of call initiation messages, which could be used to either confirm the call as legitimate or provide where it is really coming from.
Apple files numerous patent applications each week, and while the appearance of a granted patent or an application at the USPTO may be promising, there is no guarantee the concepts in the filing will become available in a future consumer product.
In this case, it is plausible for such a detection system to be enacted, but it would require cooperation between telecommunications firms to set up and operate. Apple does have influence over mobile networks due to the popularity of the iPhone, which could be used to implement the system in this way.
Apple is involved in an FCC "Robocall Strike Force," along with Google, AT&T, and 30 other companies, aiming to cut down on the number of nuisance calls made and received in the United States.
During Wednesday's launch of the Google Pixel 3, Google revealed the smartphone will include Call Screen, a screening feature that uses Google Assistant to answer and transcribe the caller's request and display the text to the user. The transcription is then provided to the user, who can answer, decline the call, or report the call as spam.
Apple is also currently in a legal battle with India's TRAI, where the regulator is threatening to ban iPhones from all of the country's networks if Apple does not enable its Do Not Disturb anti-spam app to be installed on iOS devices.
 Malcolm Owen
Malcolm Owen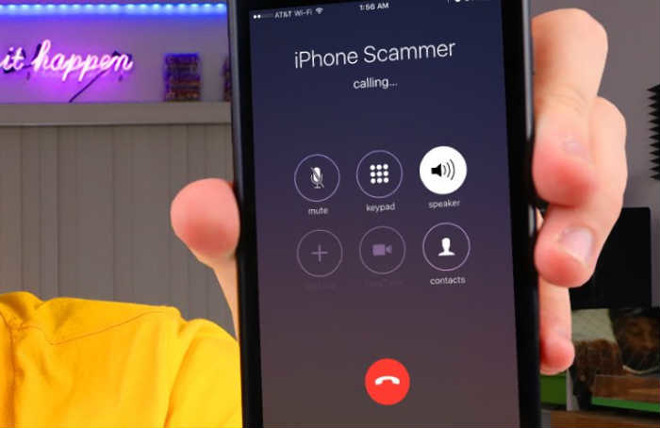







-m.jpg)






 Christine McKee
Christine McKee
 Marko Zivkovic
Marko Zivkovic
 Mike Wuerthele
Mike Wuerthele

 Amber Neely
Amber Neely
 Sponsored Content
Sponsored Content
 Wesley Hilliard
Wesley Hilliard








26 Comments
I sure hope this can be done in a future version of iOS and not future version of iPhone. This sounds like a task the Bionic chip was meant to do.
Cool, my wifes Pixel has been doing this for a year or two now. Looking forward to this development!
gatorguy said:
Well, if it's software, roll it out in beta now... at least flashing 'potential scam' on the screen on the phone with a 'screen' and a 'block/report' button to the carrier
I can't believe all the 'you qualify for lower interest calls from 'my card issuer, VisaMaster Card Services' who then proceed to ask me for my credit card number, and then tell me that 'it's secure because they don't ask me for the CCV number' (yeah, I answered about 1 a day to ask them to stop) I've been blocking all of them after the fact, and it's now down to about 3 a week vs 5 a day.
(Thank you, EquiFax)
In a related note... I got a call from another user in my exchange (XXX-XXX-nnnn) who said I called them... I'm wondering if you start 'blocking' calls if the robocallers start using YOUR phone number (thinking it's dead/disconnected, and a good candidate for spoofed robocalling). [If I were evil... I would]. Anyone else hearing that condition happening?
It is just enough for telecommunication companies to check if line is registered to anyone and if it is open (in use currently by subscriber - this can be done and I had that as solution to someone spoofing my line for some activity years ago). Also Apple as first step could allow blocking not by number, but by all blocks of numbers settings. I also find blocking by schedule primitive - there is different schedule for business days and for weekend/holidays, but they do not seem to support it. On top of that why do I need to agree to any software to give access to my contacts? You are supposed to get access to my blocking list. It is none of anybody's business what my contacts are when we are talking about blocking (I might block even some of my contacts temporarily). This logic should be straightend out and we will be closer to solution.