Amateur iOS hacker Jose Rodriguez on Friday unearthed another obscure, yet effective, lock screen bypass that leans on an unpatched bug in VoiceOver to gain unauthorized access to photos on a target device.
Detailed in a brief video posted to Rodriguez's YouTube channel, the exploit requires a would-be hacker have both their personal device and a target iPhone handy at the time of attack.
As Rodriguez explained to AppleInsider, the target iPhone first receives a phone call from an outside number, which triggers a standard iOS call dialogue. If the attacker does not know the target iPhone's number, they can acquire caller ID information by invoking Siri and asking the assistant to call their personal phone digit-by-digit.
In his proof-of-concept video, Rodriguez taps on the "Message" option on the iOS call screen and selects "Custom" to display the Messages user interface. After entering a few random letters in the text box, he once again invokes Siri to activate VoiceOver.
Returning to Messages, Rodriguez taps on the camera icon and, while invoking Siri with iPhone's side button, double taps the screen to trigger what appears to be a system-level conflict. While this particular step must be performed with a certain level of precision, an attacker can repeat the process multiple times until the desired effect is achieved.
A black screen is displayed when the bug condition is met. As Rodriguez demonstrates, however, VoiceOver's text selection tool is able to access "hidden" UI options through typical navigation gestures. Swiping left on the blank screen takes Rodriguez to "Photo Library" which, when selected by double tapping, returns him to the Messages app.
The app drawer below the text input box is blank, but leaves the app card collapse button active. Tapping on said element — a small handlebar — and swiping right grants VoiceOver unseen access to a target device's photos, details of which are read aloud by the system.
Swiping through the photo library, which is seemingly obscured by the Messages UI, and double tapping on a given photo inserts the image into the Messages text box. Multiple photos can be inserted, viewed and sent to an attacker's device in this manner.
AppleInsider independently confirmed Rodriguez's findings using current model iPhones, including iPhone X and XS devices, running the latest iOS 12.0.1.
Word of the bypass arrives two weeks after Rodriguez discovered a pair of similar VoiceOver vulnerabilities that grant unauthorized access to user contacts and photos. Unlike the previously uncovered methods, today's technique is far less involved and allows would-be attackers to offload photos onto another device with relative ease.
Concerned users can minimize exposure to the apparent bugs by disabling Siri lock screen access in Settings > Face ID & Passcode or Settings > Touch ID & Passcode under the "Allow access when locked" heading.
 Mikey Campbell
Mikey Campbell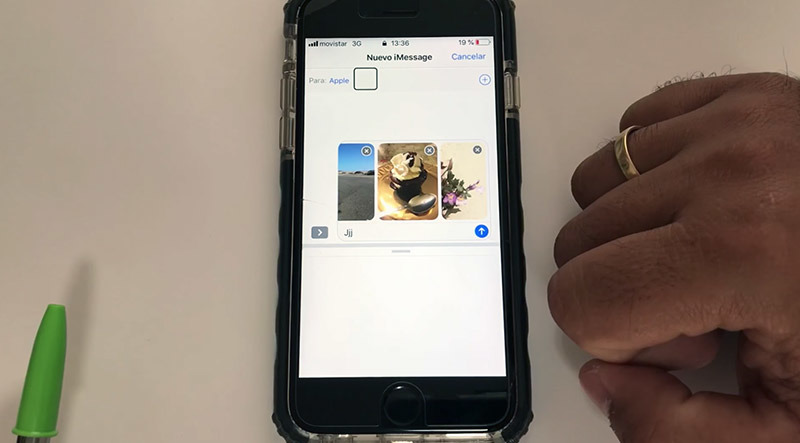







-m.jpg)






 Charles Martin
Charles Martin
 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher

 Christine McKee
Christine McKee
 Wesley Hilliard
Wesley Hilliard

 Andrew Orr
Andrew Orr







6 Comments
Heeeeere we go again.....
Damn, he’s really quite good at this!
Apple should hire him.
Pretty good job dude. Please file a bug report to Apple about this.
Those lockscreen bugs exist since years now and have generated a lot of bad press so far. I have most lockscreen access features disabled until Apple eventually hires a professional developer working on it. And they should hire this guy. It is embarrassing.
Yes, it should be fixed. However, this bug will be leveraged for nefarious means "0" times. Guaranteed.