A China-based security researcher has withdrawn a presentation on what was advertised as a workable Face ID hack from the prestigious Black Hat Asia conference after his employer, Ant Financial, called the talk "misleading."
Wish Wu, who was scheduled to deliver a presentation titled "Bypass Strong Face ID: Everyone Can Deceive Depth and IR Camera and Algorithms" at Black Hat Asia in March, told Reuters on Thursday that he pulled out of the conference at the behest of Ant.
An abstract of Wu's talk, which was pulled from Black Hat's website in December, claimed Face ID's facial recognition technology could be defeated with a black-and-white printed image and "some tape." According to the report, Ant uncovered incongruities in Wu's research late last year, which led to his withdrawal from the conference.
"The research on the face ID verification mechanism is incomplete and would be misleading if presented," the firm said.
Wu agreed with Ant's assessment, saying he was only able to reproduce the hack on an iPhone X under certain unspecified conditions. Apple's iPhone XS and XS Max are unaffected by the attack, Wu said.
"In order to ensure the credibility and maturity of the research results, we decided to cancel the speech," Wu told Reuters.
What, exactly, was amiss in Wu's research remains unknown. It should be noted that Ant, formerly known as Alipay, has long supported Apple's cutting-edge user authentication hardware, including Touch ID and Face ID.
Apple introduced Face ID with iPhone X in 2017, touting the biometric security solution's speed and accuracy. Apple claims Face ID false positives are one in a million, a figure that compares to a match rate closer to 1 in 50,000 for the outgoing Touch ID fingerprint system.
Part of the TrueDepth camera system, Face ID employs a dot projector, infrared camera and flood illuminator to collect depth map and image data of a user's face. Using this information, the onboard A-series system-on-chip creates a mathematical model of the target face and sends this data to a secure enclave for matching.
Face ID has proven extremely effective against spoofing and other physical hacks. In 2017, Vietnamese security firm Bkav claimed it defeated the system with a mask, though the technique has not been reproduced by other researchers.
 Mikey Campbell
Mikey Campbell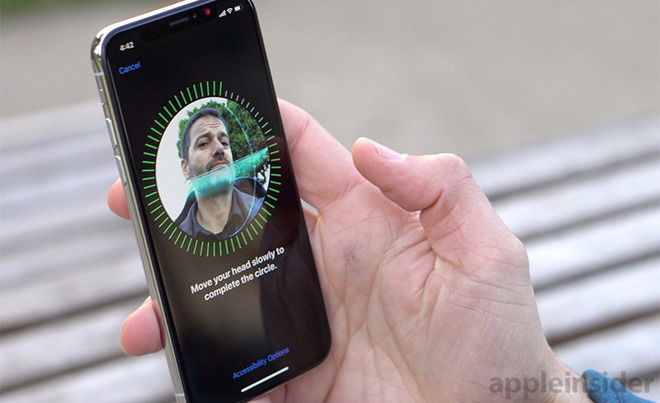







-m.jpg)





 Chip Loder
Chip Loder
 Wesley Hilliard
Wesley Hilliard
 Marko Zivkovic
Marko Zivkovic

 Christine McKee
Christine McKee
 Amber Neely
Amber Neely

 Malcolm Owen
Malcolm Owen







12 Comments
I Wish Wu well
Bkav doesn’t deserve anymore publicity from their PR stunt.
Ars asked them some very specific questions about their procedures which they either provided vague answers on or didn’t answer at all.
It’s pretty obvious that Bkav pointed the iPhone at the mask and then entered the PIN so it would learn/merge the mask with the original face (which is the way FaceID is supposed to work). The mask would then work to unlock the phone. This is the specific issue they were pressed on and refused to answer.
Just a bunch of scammers looking for their 15 minutes of fame. It’s interesting that we haven’t heard of anyone else successfully making a mask to unlock an iPhone with FaceID. With TouchID there were numerous people that successfully used a fake fingerprint to unlock iPhones (though they are also sketchy - mainly concerned with how they lifted such pristine fingerprints). But given a perfect fingerprint it’s possible to trick TouchID.
And yet not a peep about the myriad of Android security blunders... :/