Wireless features like AirDrop and Wi-Fi password sharing on iPhones, Macs, and other Apple devices can expose exploitable data, according to a recent report — but there are two easy solutions.
The technologies broadcast a partial cryptographic (SHA256) hash, which can be used to obtain details like an iPhone's phone number or a Mac's static MAC address, said security outfit Hexway. The underlying issue is data packets sent through Bluetooth Low Energy (BLE), which for all Apple devices transmit information such as name, OS version, battery status, and whether Wi-Fi is on.
This is often innocuous and necessary, but could be used by some parties to track people or launch a more serious attack. In one short video, Hexway demonstrated an AirDrop-based exploit that allows someone to send an SMS message to a target.
Attackers may also be able to send their own BLE requests and disguise themselves as devices like AirPods, or force target hardware to share a Wi-Fi password.
The issue is present on all iOS devices from iOS 10.3.1 onwards, Hexway said, though products prior to the iPhone 6s are only sending a limited number of messages instead of a continuous stream. Regardless, the only way of completely mitigating the threat is turning off Bluetooth, which may not be worth it — especially for people with accessories that depend on wireless, such as headphones or an Apple Watch.
"This behavior is more a feature of the work of the ecosystem than vulnerability," Hexway commented.
Much of this vector of attack is inherent to the BLE protocol, but AirDrop and similar sharing standards slightly expose the vector. It's recommended that Apple users lock down AirDrop as much as they can by setting it to "Contacts Only," or disabling it entirely, since strangers might otherwise be able send harassing images and other files.
The attack is still mostly a targeted one, and most users won't have to worry. There is no evidence that this vector is currently being exploited.
 Roger Fingas
Roger Fingas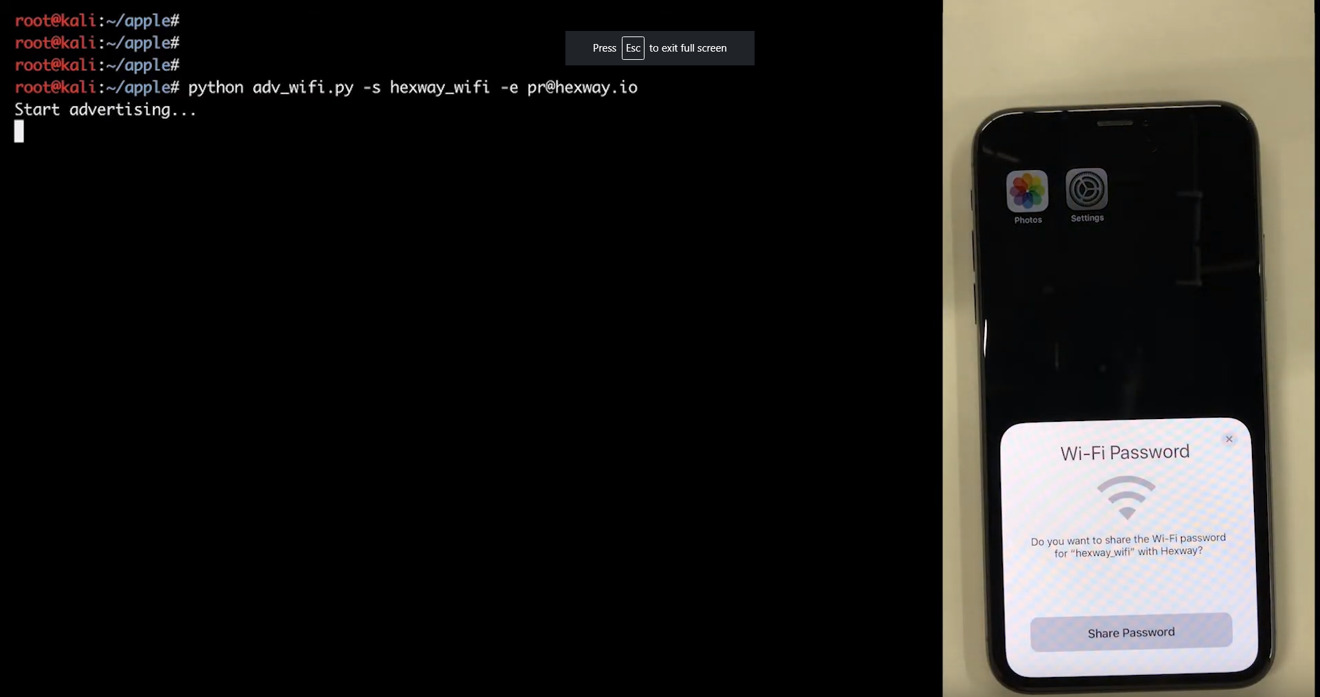







-m.jpg)






 Thomas Sibilly
Thomas Sibilly
 Wesley Hilliard
Wesley Hilliard
 Marko Zivkovic
Marko Zivkovic

 Malcolm Owen
Malcolm Owen

 Amber Neely
Amber Neely









14 Comments
"They" will always find a way to get in.
Whether or not they do depends mainly on: How hard they are willing to work based on the value of the prize versus how hard it is to get in, and, the relative difficulty compared to somebody else's system.
I was just talking about AirDrop as a minor security hole this morning. I'm glad this specific threat is being addressed, but this is also nothing that anyone needs to worry about. Sure, Apple should worry about it and work to make these features more secure for the user, but I wouldn't even contact friends and family to have them adjust their AirDrop settings. I say this as someone that has used AirDrop as a way to put illicit files on someone's machine to set them up for a crime they didn't commit… in a thriller I've written.
Personally, when it comes to personal security, I really wish Apple didn't have any phone numbers show up for calls and texts on the lock screen before the device is authenticated with a passcode after a restart. I find these numbers a lot more revealing than some name I've put in, like Bob.
"Critical data"
This trend of being obsessed with the exposure of data that is not meaningful in the least is incredibly obnoxious and needs to die.
Tomorrow's headline: COMPANY CREATES GIANT BOOK OF EVERYONES NAME AND PHONE NUMBER AND MAILS IT TO EVERYONE! OUTRAGE CANNOT BE QUELLED!
I don't think I have ever used AirDrop successfully when set to "Contacts Only", only when set to "Everyone" (on my iOS devices). I find it very convenient but I wish that issue would be rectified.
It seems like week rich for threats: https://www.zdnet.com/article/apples-awdl-protocol-plagued-by-flaws-that-enable-tracking-and-mitm-attacks/ https://www.techradar.com/news/imessage-security-flaws-google-project-zero