Researchers at security conference Def Con 2019 demonstrated a method of exploiting regular database searches to produce malicious results, and used Apple's standard iOS Contacts app to prove it.
Security firm Check Point has demonstrated a vulnerability in the industry-standard SQLite database format which can be exploited. Speaking at Def Con 2019, the company showed the technique being used to manipulate Apple's iOS Contacts app. Searching the Contacts app under these circumstances can be enough to make the device run malicious code.
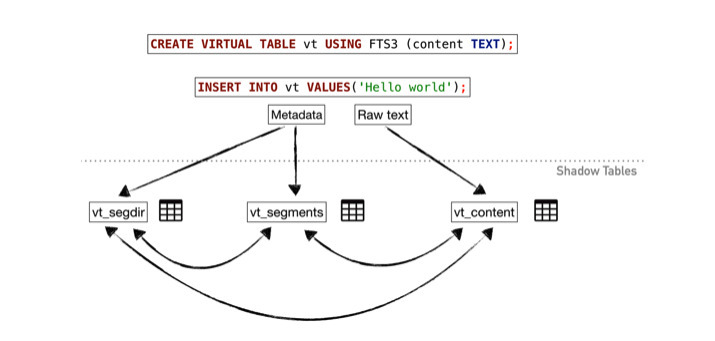
"SQLite is the most wide-spread database engine in the world," said the company in a statement. "It is available in every operating system, desktop and mobile phone. Windows 10, macOS, iOS, Chrome, Safari, Firefox and Android are popular users of SQLite."
"In short, we can gain control over anyone who queries our SQLite-controlled database," they continued.
When you search for a contact or look up information in any app, you are really searching a database and very commonly that will be using SQLite.
Documented in a 4,000-word report seen by AppleInsider, the company's hack involved replacing one part of Apple's Contacts app and it also relied on a known bug that has hasn't been fixed four years after it was discovered.
"Wait, what? How come a four-year-old bug has never been fixed?" write the researchers in their document. "This feature was only ever considered vulnerable in the context of a program that allows arbitrary SQL from an untrusted source and so it was mitigated accordingly. However, SQLite usage is so versatile that we can actually still trigger it in many scenarios."
In other words, the bug has been considered unimportant because it was believed it could only be triggered by an unknown application accessing the database, and in a closed system like iOS, there are no unknown apps. However, Check Point's researchers then managed to make a trusted app send the code to trigger this bug and exploit it.
They replaced a specific component of the Contacts app and found that while apps and any executable code has to have gone through Apple's startup checks, an SQLite database is not executable.
"Persistency [keeping the code on the device after a restart] is hard to achieve on iOS," they said, "as all executable files must be signed as part of Apple's Secure Boot. Luckily for us, SQLite databases are not signed."
They had to have access to the unlocked device to install this replacement for part of Contacts. After that, though, they were able to choose what they wanted to happen when the Contacts database was searched.
For the purpose of the demonstration, they just had the app crash. The researchers said that they could have crafted the app to steal passwords.
"We established that simply querying a database may not be as safe as you expect," they said. "We proved that memory corruption issues in SQLite can now be reliably exploited."
"Our research and methodology have all been responsibly disclosed to Apple," they concluded.
This is not the first time that a problem in an SQLite database has resulted in a bug, nor one that remained unfixed for years.
 William Gallagher
William Gallagher







-m.jpg)





 Amber Neely
Amber Neely
 Malcolm Owen
Malcolm Owen


 Christine McKee
Christine McKee




-m.jpg)



25 Comments
" And then, using a cheap pair of sunglasses and some tape..." ;)
"They had to have access to the unlocked device to install this replacement for part of Contacts." Well, if they have your unlocked device everything on the device is accessible. No need to install the replacement part of Contacts.
This is why MacOS needed a bug bounty program (which they now have).
Shocker. Those little (unimportant) bugs are important...
SQLite is not a full scale SQL RDBMS. As it name implies it is a small core offered to applications for their management of mundane data tasks, every developer is aware of that. If SQLite was threatening iOS security architecture Apple wouldn’t include it in iOS, remember how Flash has been made defunct by Apple. I bet that 4000 word report has a very short, say 40 to 400 word falsification from Apple engineers. “We exposed but they didn’t proceed” is not security nor engineering, it is marketing or sycophantism. “iOS security architecture is wrong, it must be implemented the way I have divinated after years long transcendental worshipping to ultimate singularity powers”. You wish... No one listens to you except click-freak media.
To be honest, if I give a perfect stranger my unlocked phone and then watch while they jailbreak it so they hacK replace “components” of the contacts app, then I’d be a lot more worried about my mental state than hacking my contacts list.
And why did they go to the trouble of replacing a ‘component of the Contacts’ app? Why couldn’t they just put an app on the store and give it permission to access the contacts? Is there something the contacts app is doing that isn’t available to third party developers?
Big whoop.
Pity you didn’t then, because that would’ve been a marginally more impressive demo.
If you put your passwords in your unencrypted contacts field then this hack is not your biggest problem.
I’m sure they have, and having assessed the risk, Apple decided to make it a low priority.