A team of researchers has disclosed a new vulnerability that could allow attackers to trick modern Bluetooth-enabled host devices into pairing with a malicious device masquerading as a trusted one.
The security flaw, which the team has dubbed Bluetooth Impersonation Attacks (BIAS), affects a slew of devices that use Bluetooth, including iPhones, iPads and Macs.
Essentially, BIAS attacks exploit a vulnerability in how Bluetooth devices handle long-term connections. When two Bluetooth devices are paired, they agree on a "link key," which allows them to reconnect to each other without going through the pairing process again.
The researchers, a group of academics at the cole Polytechnique Federale de Lausanne in Switzerland, found that they were able to spoof the Bluetooth address of a previously paired device to complete an authentication process without knowing this link key.
More specifically, the flaw kicks in when an attacking device pretends to be a previously trusted one that only supports unilateral authentication — the lowest security setting in Bluetooth. A user's device would normally be the one to authenticate whether this connection was valid. By using a tactic known as role-switching, however, an attacker could spoof that authentication and establish a secure connection with the user device simply agreeing to it.
Combined with other Bluetooth exploits like Key Negotiation of Bluetooth (KNOB), an attacker can compromise devices running in Secure Authentication mode. Once the BIAS attack is successful, an attacking device could be used to carry out other exploits, including accessing data sent via Bluetooth or even controlling the functions that a previously paired device would have.
Because Bluetooth connections oftentimes don't require explicit user interaction, the BIAS and KNOB attacks are also stealthy and can be carried out without a user's knowledge.
Who's at risk from the BIAS exploit
This flaw only impacts Bluetooth Basic Rate / Enhanced Data Rate, also known as Bluetooth Classic. But that still leaves relatively recent Apple devices subject to the attack, including the iPhone 8 and older, 2017 MacBook devices and older, and 2018 iPad models and older.
To carry out the attack, a bad actor would need to be within Bluetooth range of a vulnerable device, and know the Bluetooth address of a previously paired device. For a skilled attacker, finding these Bluetooth addresses is relatively trivial, even if they're randomized.
Potential mitigations for the attack include turning off Bluetooth when you aren't using it, or ensuring that your device has no prior link keys by manually forgetting every device that you pair with.
The researchers have alerted the Bluetooth Special Interest Group (SIG), which has already updated the Bluetooth Core Specification to mitigate the flaw. It's likely that manufacturers such as Apple and Samsung will roll out firmware or software patches with the fix in the near future.
 Mike Peterson
Mike Peterson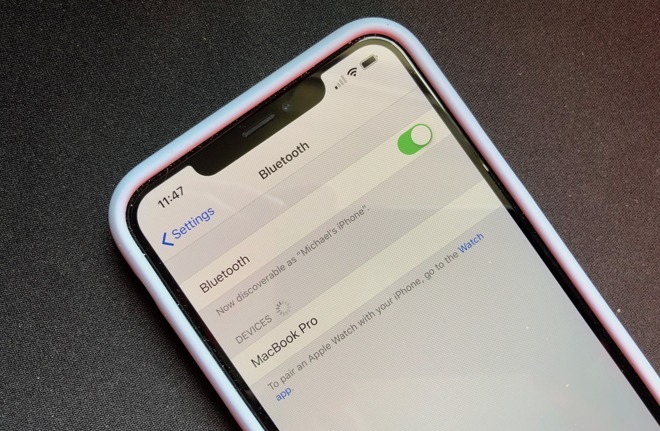






-m.jpg)






 Charles Martin
Charles Martin


 Wesley Hilliard
Wesley Hilliard
 Stephen Silver
Stephen Silver
 William Gallagher
William Gallagher

 Marko Zivkovic
Marko Zivkovic









4 Comments
“Potential mitigations for the attack include turning off Bluetooth when you aren't using it”
You never know when a new vulnerability will be discovered. Bluetooth is going to continue to be one of the “low hanging fruits” for attackers.
It’s like not using a VPN when on a public WiFi. Not taking basic protections/precautions is just lazy,