A new mobile spyware is targeting both iOS and Android users in what appears to be an extortion campaign tied to illicit websites.
The malware, dubbed "Goontact," can steal data like contacts, SMS text messages, photos, and location information from an iPhone or Android. It currently appears limited to Chinese-speaking countries, Korea, and Japan.
According to the Lookout security researchers who discovered it, "Goontact" targets users who visit illicit sites, typically those offering escort services. The ultimate goal seems to be extortion or blackmail tied to users visiting or soliciting services from those sites.
The scam starts when a user is lured to a website hosting the spyware. Although they appear to be talking to an escort, scam victims are actually communicating with "Goontact" operators, who convince them that they need to side-load an app on their iOS or Android devices.
Although the spyware and similar scams are not uncommon, the portion of the campaign targeting iOS users has been previously unreported, Lookout said. The iOS version of "Goontact" primarily steals a user's phone number and contact list, though newer versions can also display a message to the victim.
Like other side-loaded iOS malware threats, "Goontact" operators use an Apple enterprise developer certificate to distribute the spyware outside of the App Store. The certificates used in the Spyware campaign all reference what appear to be legitimate companies, including credit unions and railroad corporations.
It isn't clear if those legitimate companies have been compromised, or if the bad actors masqueraded as representatives of them to obtain the certificates.
During the course of Lookout's research, the team noticed multiple certificates being revoked. Once they were, new identities appeared on distribution sites, indicating that "Goontact" operators had no trouble obtaining new certificates.
Who's at risk, and how to protect yourself
"Goontact" doesn't appear to have spread beyond China, Japan, Korea, Thailand, and Vietnam yet, though there's a chance that it or a similar spyware strain could.
The spyware operators rely on social engineering to convince users to side-load the malicious apps onto devices. Because of that, if you never attempt to side-load anything, you won't be at risk.
As far as general best practices, it's always recommended to only download apps through the official App Store from developers that you trust, and to keep the software on your iPhone, iPad, or other device up to date.
Update: Apple said it has revoked all the enterprise certificates used in the scam thus far, with one exception belonging to a developer that was compromised. The company said it's working with that developer to "safely revoke the certificate by the end of the week," and added that it has "already taken steps to block all the malicious enterprise profiles issued for that certificate."
 Mike Peterson
Mike Peterson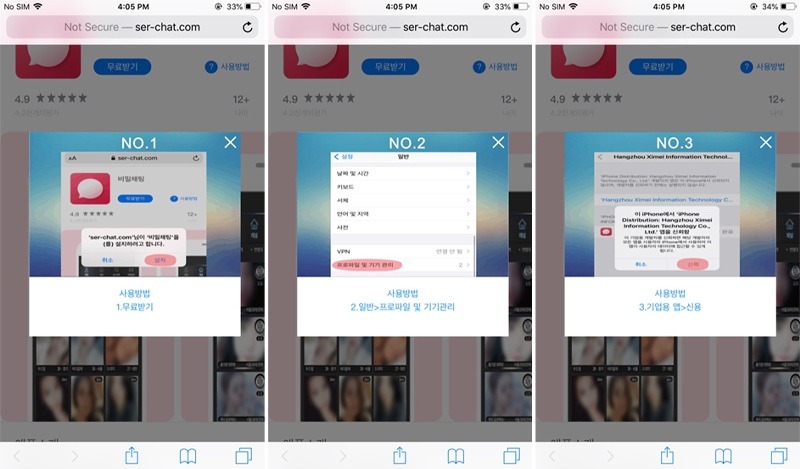

-xl-(1)-xl-xl-m.jpg)





-m.jpg)





 Wesley Hilliard
Wesley Hilliard
 Marko Zivkovic
Marko Zivkovic
 Andrew Orr
Andrew Orr
 Malcolm Owen
Malcolm Owen


 Andrew O'Hara
Andrew O'Hara
 William Gallagher
William Gallagher






7 Comments
Funny how these types of situations always seem to boil down to gullible users.
Would be really useful here to explain, or remind, what “side-load” precisely implies in the context of iOS.
I guess I knew but forgot...
Stopped reading after “side-loading”...And yes, side-loading means installing an app outside of th e App Store. Here you find some details: https://searchmobilecomputing.techtarget.com/opinion/Did-you-know-how-easy-it-is-to-sideload-iOS-apps-to-your-iPhone
Basically, whenever you encounter the request to side-load an app outside of of your company’s enterprise device management, chances are somebody wants to scam you. Just don’t.