A new iOS vulnerability discovered by researcher Jose Rodriguez enables would-be attackers to bypass a secured iPhone lock screen and access notes by leveraging a combination of VoiceOver and common sharing tools.
The exploit, which is functional on iOS 14.8 and iOS 15, was revealed in a video posted to Rodriguez's YouTube channel on Monday.
To bypass a target iPhone's lock screen, Rodriguez first asks Siri to turn on VoiceOver and navigates to Notes in Control Center. As expected, a new note field is displayed with no user content revealed.
Invoking Control Center again, Rodriguez selects and opens stopwatch, and after some finagling is able to select the previously opened Notes app via VoiceOver. Instead of an empty note, however, iOS grants access to the Notes database including saved content, which in the sample case includes a note with text, an audio recording, HTML link, contact card and more.
VoiceOver's rotor is then used to select and copy the note for export to a second iPhone. In one scenario, the target device is called by a second iPhone. The attacker can decline the call and paste the copied text into a custom Messages response. Alternatively, the text can be pasted into Messages should a second device send a text to the target iPhone.
The exploit does not work with passcode-protected notes.
There are more than a few caveats to successfully leveraging the apparent security flaw. First, an attacker needs physical access to a victim's iPhone. The device must have Siri activated, Control Center available in the lock screen, and Notes and Clock included in Control Center. The victim's phone number must also be known.
Rodriguez is "giving away" the exploit instead of reporting it through Apple's Bug Bounty program because he hopes to shed light on difficulties with the initiative, the researcher told AppleInsider. In addition to low payouts, the researcher said Apple can take months to respond to and corroborate filings.
Apple previously awarded Rodriguez $25,000 for discovering CVE-2021-1835, another lock screen bypass that enabled access to Notes content. Apple designated the workaround as a "partial access" bug that results in partial extraction of sensitive data, limiting the payout to a $100,000 maximum. Broad access to otherwise secured data can net payments of up to $250,000.
The bypass detailed by Rodriguez on Monday can be defeated by simply disabling Siri or restricting lock screen access to Control Center in Face ID & Passcode settings.
 Mikey Campbell
Mikey Campbell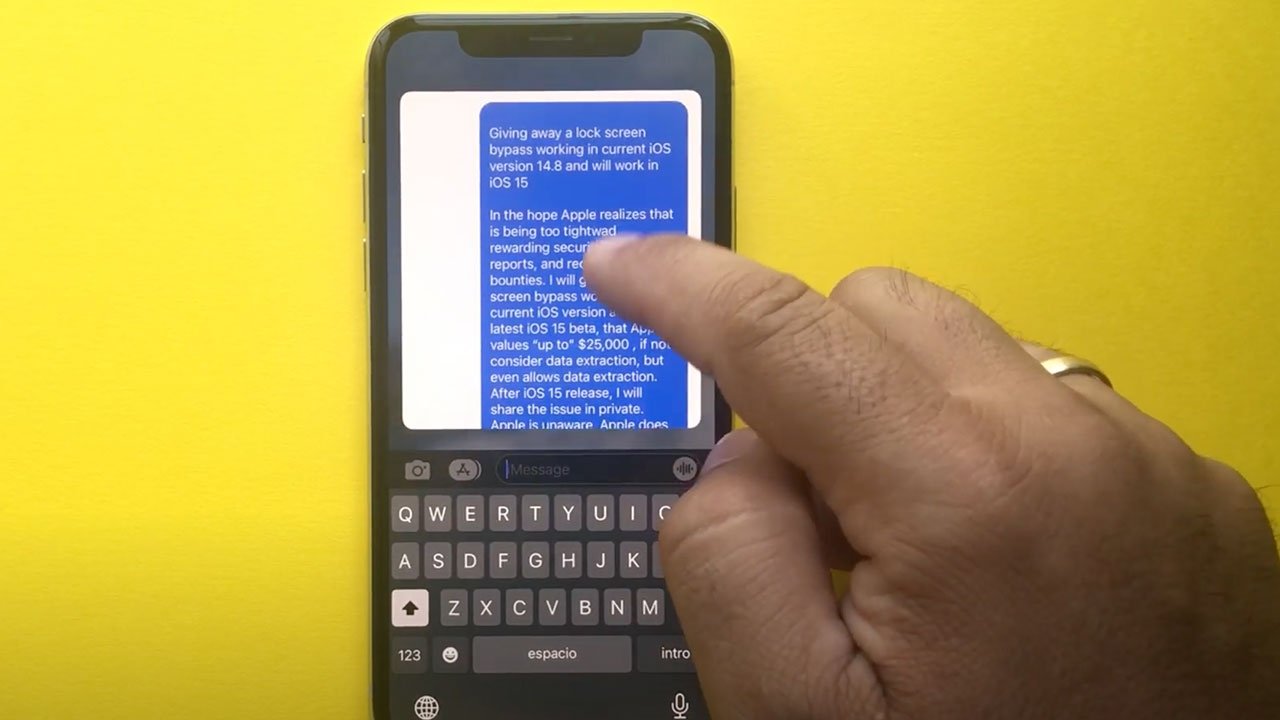







 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher

 Wesley Hilliard
Wesley Hilliard



 Christine McKee
Christine McKee



-m.jpg)




There are no Comments Here, Yet
Be "First!" to Reply on Our Forums ->